[ad_1]
A brand new variant of the infamous Mirai botnet has been discovered leveraging a number of safety vulnerabilities to propagate itself to Linux and IoT gadgets.
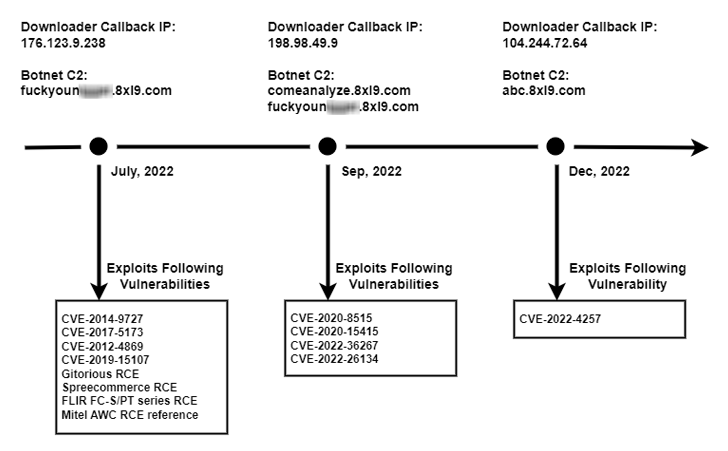
Observed in the course of the second half of 2022, the brand new model has been dubbed V3G4 by Palo Alto Networks Unit 42, which recognized three completely different campaigns seemingly performed by the identical menace actor.
“Once the susceptible gadgets are compromised, they are going to be totally managed by attackers and turn into part of the botnet,” Unit 42 researchers stated. “The menace actor has the potential to make the most of these gadgets to conduct additional assaults, reminiscent of distributed denial-of-service (DDoS) assaults.”
The assaults primarily single out uncovered servers and networking gadgets operating Linux, with the adversary weaponizing as many as 13 flaws that would result in distant code execution (RCE).
Some of the notable flaws relate to vital flaws in Atlassian Confluence Server and Data Center, DrayTek Vigor routers, Airspan AirSpot, and Geutebruck IP cameras, amongst others. The oldest flaw within the listing is CVE-2012-4869, an RCE bug in FreePBX.
Following a profitable compromise, the botnet payload is retrieved from a distant server utilizing the wget and cURL utilities.
The botnet, along with checking if it is already operating on the contaminated machine, additionally takes steps to terminate different competing botnets reminiscent of Mozi, Okami, and Yakuza.
V3G4 additional packs a set of default or weak login credentials that it makes use of to hold out brute-force assaults by Telnet/SSH and proliferate to different machines.
It additionally establishes contact with a command-and-control server to await instructions for launching DDoS assaults towards targets through UDP, TCP, and HTTP protocols.
“The vulnerabilities talked about above have much less assault complexity than beforehand noticed variants, however they keep a vital safety affect that may result in distant code execution,” the researchers stated.
To stave off such assaults, it is really useful that customers apply obligatory patches and updates as and after they turn into relevant, and safe the gadgets with robust passwords.