[ad_1]
The menace actor behind the BlackRock and ERMAC Android banking trojans has unleashed one more malware for hire known as Hook that introduces new capabilities to entry information saved within the gadgets and create a distant interactive session.
ThreatFabric, in a report shared with The Hacker News, characterised Hook as a novel ERMAC fork that is marketed on the market for $7,000 monthly whereas that includes “all of the capabilities of its predecessor.”
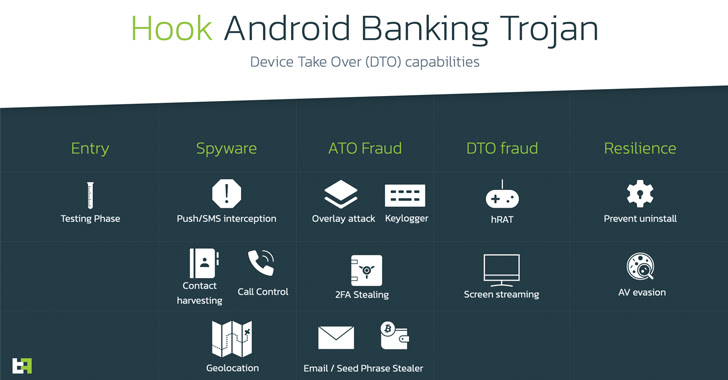
“In addition, it additionally provides to its arsenal Remote Access Tooling (RAT) capabilities, becoming a member of the ranks of households resembling Octo and Hydra, that are succesful performing a full Device Take Over (DTO), and full a full fraud chain, from PII exfiltration to transaction, with all of the intermediate steps, with out the necessity of further channels,” the Dutch cybersecurity agency mentioned.
A majority of the monetary apps focused by the malware are situated within the U.S., Spain, Australia, Poland, Canada, Turkey, the U.Okay., France, Italy, and Portugal.
Hook is the handiwork of a menace actor generally known as DukeEugene and represents the newest evolution of ERMAC, which was first disclosed in September 2021 and relies on one other trojan named Cerberus that had its supply code leaked in 2020.
“Ermac has at all times been behind Hydra and Octo by way of capabilities and options,” ThreatFabric researcher Dario Durando advised The Hacker News by way of e-mail. “This can be identified amongst menace actors, preferring these two households above Ermac.”
“The lack of some type of RAT capabilities is a significant concern for a contemporary Android Banker, because it doesn’t present the likelihood to carry out Device Take Over (DTO), which is the fraud methodology that’s more than likely to achieve success and never detected by fraud scoring engines or fraud analysts. This is more than likely what triggered the event of this new malware variant.”
Like different Android malware of its ilk, the malware abuses Android’s accessibility companies APIs to conduct overlay assaults and harvest all types of delicate info resembling contacts, name logs, keystrokes, two-factor authentication (2FA) tokens, and even WhatsApp messages.
It additionally sports activities an expanded record of apps to incorporate ABN AMRO and Barclays, whereas the malicious samples themselves masquerade because the Google Chrome internet browser to dupe unsuspecting customers into downloading the malware:
- com.lojibiwawajinu.guna
- com.damariwonomiwi.docebi
- com.yecomevusaso.pisifo
Among the opposite main options to be added to Hook is the power to remotely view and work together with the display screen of the contaminated machine, receive information, extract seed phrases from crypto wallets, and monitor the cellphone’s location, blurring the road between spyware and adware and banking malware.
ThreatFabric mentioned the Hook artifacts noticed up to now in a testing section, however famous it may very well be delivered by way of phishing campaigns, Telegram channels, or within the type of Google Play Store dropper apps.
“The predominant downside of making a brand new malware is normally gaining sufficient belief by different actors, however with the standing of DukeEugene amongst criminals, it is rather seemingly that this is not going to be a difficulty for Hook,” Durando mentioned.
[ad_2]