[ad_1]
Authored by Dexter Shin
McAfee’s Mobile Research Team has recognized new malware on the Google Play Store. Most of them are disguising themselves as cleaner apps that delete junk recordsdata or assist optimize their batteries for machine administration. However, this malware hides and constantly present commercials to victims. In addition, they run malicious companies routinely upon set up with out executing the app.
HiddenAds capabilities and promotion
They exist on Google Play regardless that they’ve malicious actions, so the sufferer can seek for the next apps to optimize their machine.
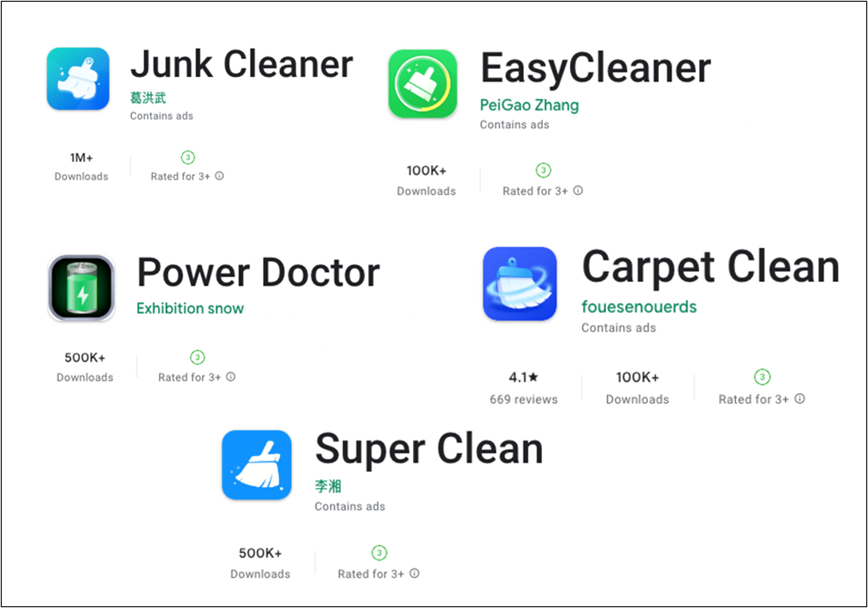
Users could typically suppose putting in the app with out executing it’s secure. But you will have to alter your thoughts due to this malware. When you put in this malware in your machine, it’s executed with out interplay and executes a malicious service.
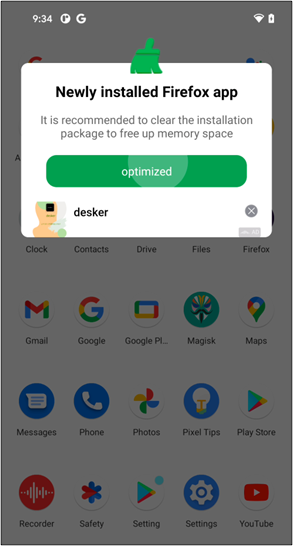
In addition, they attempt to disguise themselves to stop customers from noticing and deleting apps. Change their icon to a Google Play icon that customers are acquainted with and alter its title to ‘Google Play’ or ‘Setting.’

Automatically executed companies consistently show commercials to victims in a wide range of methods.

These companies additionally induce customers to run an app after they set up, uninstall, or replace apps on their gadgets.
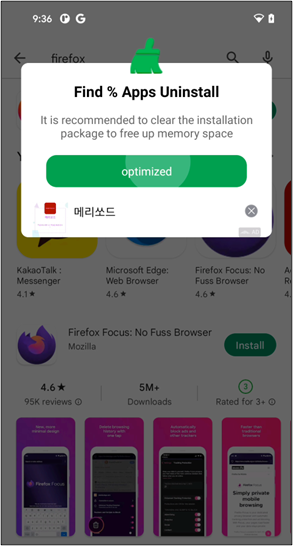
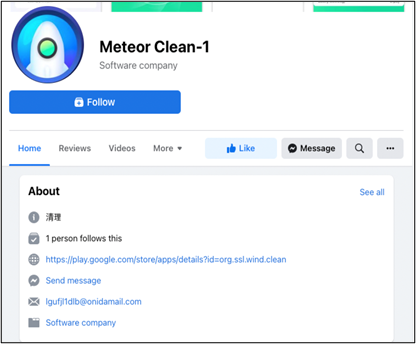
To promote these apps to new customers, the malware authors created promoting pages on Facebook. Because it’s the hyperlink to Google Play distributed by reliable social media, customers will obtain it undoubtedly.

How it really works
This malware makes use of the Contact Provider. The Contact Provider is the supply of knowledge you see within the machine’s contacts software, and it’s also possible to entry its information in your individual software and switch information between the machine and on-line companies. For this, Google offers ContactsContract class. ContactsContract is the contract between the Contacts Provider and purposes. In ContactsContract, there’s a class referred to as Directory. A Directory represents a contacts corpus and is carried out as a Content Provider with its distinctive authority. So, builders can use it in the event that they need to implement a customized listing. The Contact Provider can acknowledge that the app is utilizing a customized listing by checking particular metadata within the manifest file.
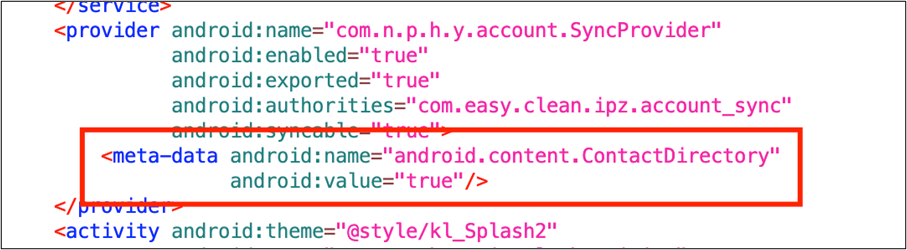
The essential factor is the Contact Provider routinely interrogates newly put in or changed packages. Thus, putting in a bundle containing particular metadata will at all times name the Contact Provider routinely.
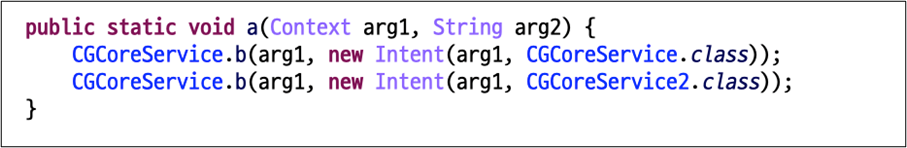
The first exercise outlined within the software tag within the manifest file is executed as quickly as you put in it simply by declaring the metadata. The first exercise of this malware will create a everlasting malicious service for displaying commercials.
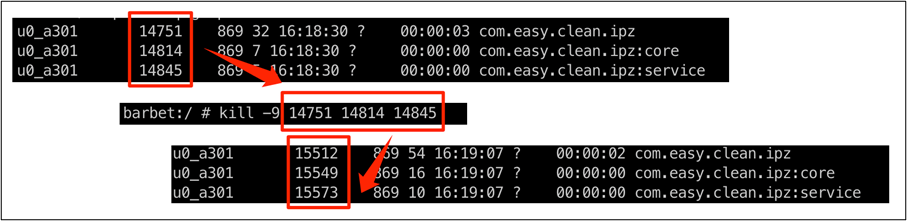
In addition, the service course of will generate instantly even whether it is compelled to kill.
Next, they modify their icons and names utilizing the <activity-alias> tag to cover.
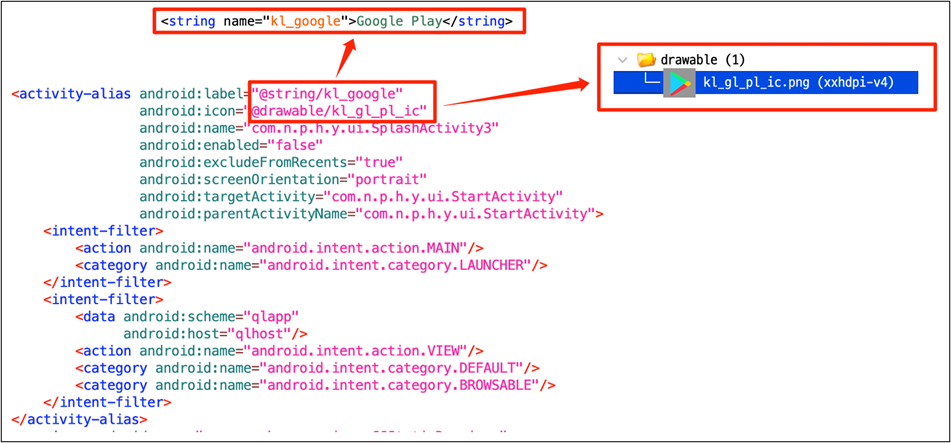
Users contaminated worldwide
It is confirmed that customers have already put in these apps from 100K to 1M+. Considering that the malware works when it’s put in, the put in quantity is mirrored because the sufferer’s quantity. According to McAfee telemetry information, this malware and its variants have an effect on a variety of nations, together with South Korea, Japan, and Brazil:
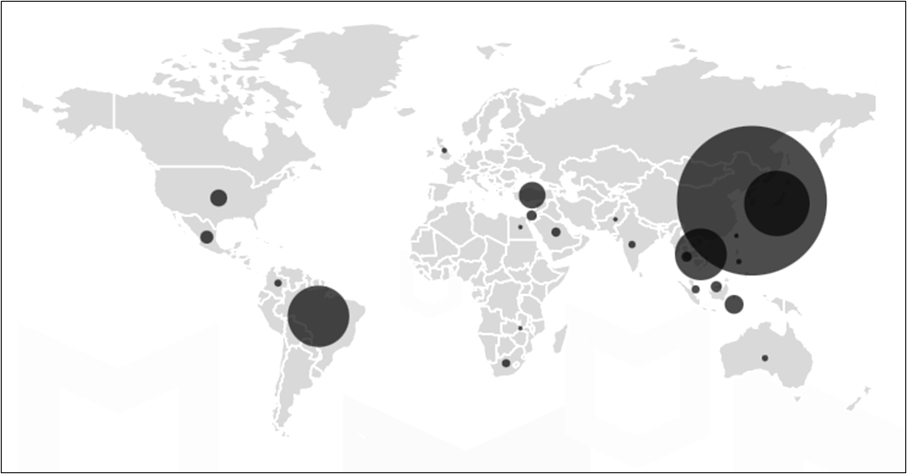
Conclusion
This malware is auto-starting malware, in order quickly because the customers obtain it from Google Play, they’re contaminated instantly. And it’s nonetheless consistently growing variants which can be revealed by completely different developer accounts. Therefore, it isn’t straightforward for customers to note this sort of malware.
We already disclosed this risk to Google and all reported purposes had been faraway from the Play Store. Also, McAfee Mobile Security detects this risk as Android/HiddenAds and protects you from this sort of malware. For extra details about McAfee Mobile Security, go to https://www.mcafeemobilesecurity.com
Indicators of Compromise
Applications:
| App Name | Package Name | Downloads |
| Junk Cleaner | cn.junk.clear.plp | 1M+ |
| SimpleCleaner | com.straightforward.clear.ipz | 100K+ |
| Power Doctor | com.energy.physician.mnb | 500K+ |
| Super Clean | com.tremendous.clear.zaz | 500K+ |
| Full Clean -Clean Cache | org.stemp.fll.clear | 1M+ |
| Fingertip Cleaner | com.fingertip.clear.cvb | 500K+ |
| Quick Cleaner | org.qck.cle.oyo | 1M+ |
| Keep Clean | org.clear.sys.lunch | 1M+ |
| Windy Clean | in.cellphone.clear.www | 500K+ |
| Carpet Clean | og.crp.cln.zda | 100K+ |
| Cool Clean | syn.clear.cool.zbc | 500K+ |
| Strong Clean | in.reminiscence.sys.clear | 500K+ |
| Meteor Clean | org.ssl.wind.clear | 100K+ |
SHA256:
- 4b9a5de6f8d919a6c534bc8595826b9948e555b12bc0e12bbcf0099069e7df90
- 4d8472f0f60d433ffa8e90cc42f642dcb6509166cfff94472a3c1d7dcc814227
- 5ca2004cfd2b3080ac4958185323573a391dafa75f77246a00f7d0f3b42a4ca3
- 5f54177a293f9678797e831e76fd0336b0c3a4154dd0b2175f46c5a6f5782e24
- 7a502695e1cab885aee1a452cd29ce67bb1a92b37eed53d4f2f77de0ab93df9b
- 64d8bd033b4fc7e4f7fd747b2e35bce83527aa5d6396aab49c37f1ac238af4bd
- 97bd1c98ddf5b59a765ba662d72e933baab0a3310c4cdbc50791a9fe9881c775
- 268a98f359f2d56497be63a31b172bfbdc599316fb7dec086a937765af42176f
- 690d658acb9022765e1cf034306a1547847ca4adc0d48ac8a9bbdf1e6351c0f7
- 75259246f2b9f2d5b1da9e35cab254f71d82169809e5793ee9c0523f6fc19e4b
- a5cbead4c9868f83dd9b4dc49ca6baedffc841772e081a4334efc005d3a87314
- c75f99732d4e4a3ec8c19674e99d14722d8909c82830cd5ad399ce6695856666
Domains:
- http[://]hw.sdk.functionads.com:8100
