[ad_1]
A brand new malware dubbed HiatusRAT infects routers to spy on its targets, largely in Europe and within the U.S. Learn which router fashions are primarily focused and learn how to defend from this safety menace.

As beforehand uncovered, routers may be utilized by menace actors as environment friendly areas to plant malware, usually for cyberespionage. Routers are continuously much less protected than commonplace units and are sometimes utilizing modified variations of current working programs. Therefore, focusing on routers will be attention-grabbing for attackers however tougher to compromise and use than a regular endpoint or server.
Lumen’s Black Lotus Labs has uncovered new malware focusing on routers in a marketing campaign named Hiatus by the researchers.
Jump to:
What is the Hiatus malware marketing campaign?
The Hiatus marketing campaign primarily targets DrayTek Vigor router fashions 2960 and 3900, which run an i386 structure. These routers are largely utilized by medium-size firms, because the router capabilities assist a couple of hundred of workers’ VPN connections.
The researchers additionally discovered different malicious binaries focusing on MIPS and ARM-based architectures.
The preliminary compromise vector stays unknown, but as soon as the attackers get entry to the focused routers, they drop a bash script. When that bash script is executed, it downloads two extra information: the HiatusRAT malware and a variant of the reliable tcpdump device, which allows community packet seize.
Once these information are run, the attackers are answerable for the router and will obtain information or run arbitrary instructions, intercept the community visitors from the contaminated gadget or use the router as a SOCKS5 proxy gadget, which can be utilized for additional compromises or for focusing on different firms.
HiatusRAT malware
When the RAT is launched, it checks if port 8816 is used. If the port is utilized by a course of, it kills it and opens a brand new listener on the port, guaranteeing that solely a single occasion of the malware is working on the gadget.
It then collects details about the compromised gadget corresponding to system data (corresponding to kernel model, MAC tackle, structure kind and firmware model), networking data (community interfaces configuration and native IP addresses) and file system data (mount factors, listing itemizing, file system kind and digital reminiscence file system). In addition, it collects an inventory of all working processes.
After amassing all that data, the malware sends it to an attacker-controlled heartbeat C2 server.
The malware has extra capabilities, corresponding to updating its configuration file, offering the attacker with a distant shell, studying/deleting/importing information, downloading and executing information, or enabling SOCKS5 packet forwarding or plain TCP packets forwarding.
Network packet seize
Aside from the HiatusRAT, the menace actor additionally deploys a variant of the reliable tcpdump device, which allows capturing community packets on the compromised gadget.
The bash script utilized by the menace actor confirmed a specific curiosity for connections on ports 21, 25, 110 and 143, that are normally devoted to file switch protocol and electronic mail transfers (SMTP, POP3 and IMAP electronic mail protocols).
The script allows extra port sniffing, if obligatory. If used, the packets captured are despatched to an add C2, completely different from the heartbeat C2, after the packet interception reaches a sure size.
This permits the menace actor to passively intercept full information transferred through the FTP protocol or emails that traverse the contaminated gadget.
Campaign focusing on
Black Lotus Labs recognized roughly 100 distinctive IP addresses speaking with the C2 servers managed by the menace actor since July 2022, which might be categorised in two classes:
- Medium-size firms working their very own electronic mail servers, typically proudly owning IP tackle ranges on the web that are capable of determine them. Companies in prescription drugs, IT companies or consulting corporations, and a municipal authorities, amongst others, might be recognized. The researchers suspect that the focusing on of IT corporations is a option to allow downstream entry to prospects’ environments.
- Internet service suppliers’ buyer IP ranges utilized by targets.
The geographic repartition of the targets exhibits a heavy curiosity in U.Ok. firms and another European international locations, along with North America (Figure A).
Figure A
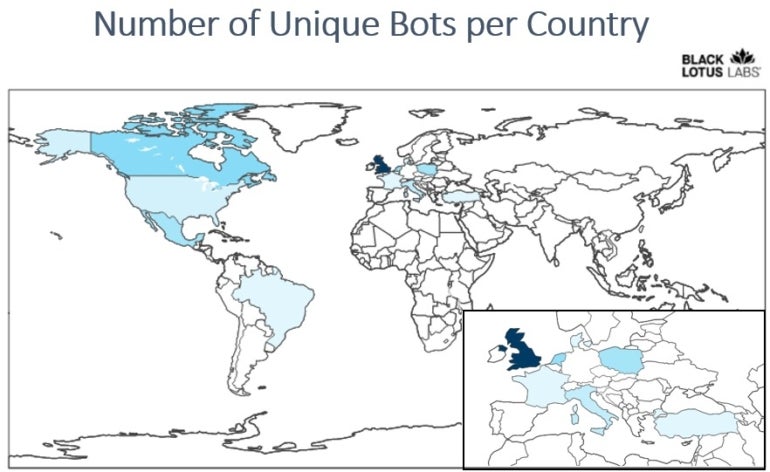
As reported by the researchers, roughly 2,700 DrayTek Vigor 2960 routers and 1,400 DrayTek Vigor 3900 routers are linked to the web. The an infection of solely roughly 100 of these routers makes the marketing campaign small and troublesome to detect; the truth that solely 100 routers out of hundreds are impacted emphasizes the likelihood that the menace actor is barely aiming at explicit targets and never occupied with bigger focusing on.
4 steps to guard from the Hiatus malware menace
1. Regularly reboot routers and maintain their firmware and software program patched to forestall compromise from frequent vulnerabilities.
2. Deploy safety options with capabilities to log and monitor the routers’ conduct.
3. End-of-life units ought to be eliminated and changed with supported fashions that may be up to date for optimum safety.
4. All visitors passing through routers ought to be encrypted in order that even intercepting it doesn’t make it exploitable.
Read subsequent: Intrusion detection coverage (TechRepublic Premium)
Disclosure: I work for Trend Micro, however the views expressed on this article are mine.
