[ad_1]
A brand new evaluation of Raspberry Robin’s assault infrastructure has revealed that it is attainable for different menace actors to repurpose the infections for their very own malicious actions, making it an much more potent menace.
Raspberry Robin (aka QNAP worm), attributed to a menace actor dubbed DEV-0856, is malware that has more and more come underneath the radar for being utilized in assaults geared toward finance, authorities, insurance coverage, and telecom entities.
Given its use a number of menace actors to drop a variety of payloads resembling SocGholish, Bumblebee, TrueBot, IcedID, and LockBit ransomware, it is suspected to be a pay-per-install (PPI) botnet able to serving next-stage payloads.
Raspberry Robin, notably, employs contaminated USB drives as a propagation mechanism and leverages breached QNAP network-attached storage (NAS) gadgets as first-level command-and-control (C2).
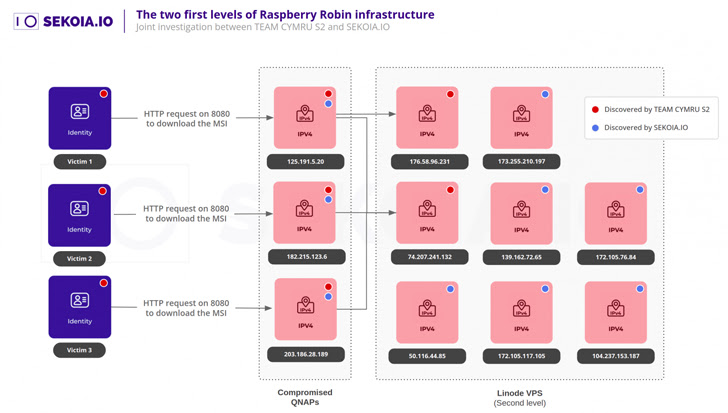
Cybersecurity agency SEKOIA stated it was capable of establish at the least eight digital non-public servers (VPSs) hosted on Linode that perform as a second C2 layer that seemingly act as ahead proxies to the subsequent as-yet-unknown tier.
“Each compromised QNAP appears to behave as a validator and forwarder,” the France-based firm stated. “If the acquired request is legitimate, it’s redirected to an higher stage of infrastructure.”
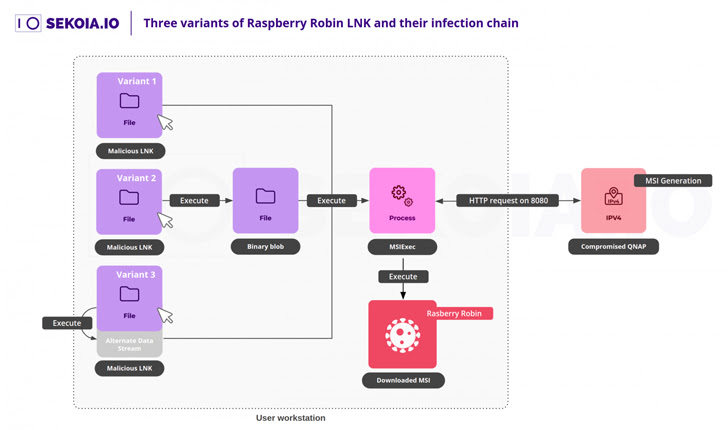
The assault chain thus unfolds as follows: When a person inserts the USB drive and launches a Windows shortcut (.LNK) file, the msiexec utility is launched, which, in flip, downloads the principle obfuscated Raspberry Robin payload from the QNAP occasion.
This reliance on msiexec to ship out HTTP requests to fetch the malware makes it attainable to hijack such requests to obtain one other rogue MSI payload both by DNS hijacking assaults or buying beforehand identified domains after their expiration.
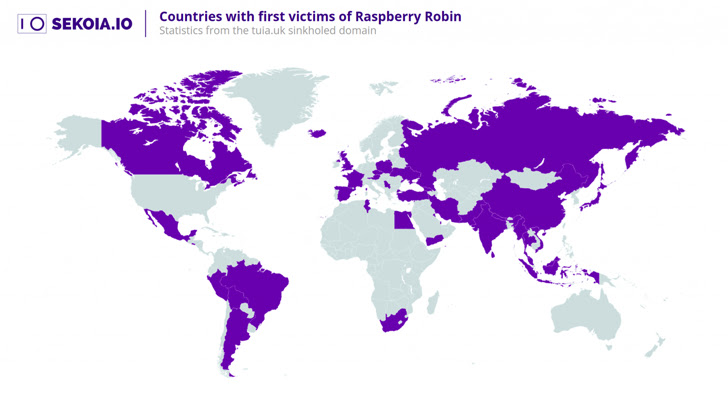
One such area is tiua[.]uk, which was registered within the early days of the marketing campaign in late July 2021 and used as a C2 between September 22, 2021, and November 30, 2022, when it was suspended by the .UK registry.
“By pointing this area to our sinkhole, we had been capable of acquire telemetry from one of many first domains utilized by Raspberry Robin operators,” the corporate stated, including it noticed a number of victims, indicating “it was nonetheless attainable to repurpose a Raspberry Robin area for malicious actions.”
The precise origins of how the primary wave of Raspberry Robin USB infections passed off stay at present unknown, though it is suspected that it might have been achieved by counting on different malware to disseminate the worm.
This speculation is evidenced by the presence of a .NET spreader module that is stated to be liable for distributing Raspberry Robin .LNK information from contaminated hosts to USB drives. These .LNK information subsequently compromise different machines through the aforementioned methodology.
The growth comes days after Google’s Mandiant disclosed that the Russia-linked Turla group reused expired domains related to ANDROMEDA malware to ship reconnaissance and backdoor instruments to targets compromised by the latter in Ukraine.
“Botnets serve a number of functions and could be reused and/or transformed by their operators and even hijacked by different teams over time,” the researcher stated.
[ad_2]