[ad_1]

Mayors’ places of work and courts in Russia are below assault by never-before-seen malware that poses as ransomware however is definitely a wiper that completely destroys information on an contaminated system, in keeping with safety firm Kaspersky and the Izvestia information service.
Kaspersky researchers have named the wiper CryWiper, a nod to the extension .cry that will get appended to destroyed recordsdata. Kaspersky says its group has seen the malware launch “pinpoint attacks” on targets in Russia. Izvestia, in the meantime, reported that the targets are Russian mayors’ places of work and courts. Additional particulars, together with what number of organizations have been hit and whether or not the malware efficiently wiped information, weren’t instantly identified.
Wiper malware has grown more and more widespread over the previous decade. In 2012, a wiper often known as Shamoon wreaked havoc on Saudi Arabia’s Saudi Aramco and Qatar’s RasGas. Four years later, a brand new variant of Shamoon returned and struck a number of organizations in Saudi Arabia. In 2017, self-replicating malware dubbed NotPetya unfold throughout the globe in a matter of hours and precipitated an estimated $10 billion in harm. In the previous yr, a flurry of latest wipers appeared. They embody DoubleZero, IsaacWiper, AirtightWiper, CaddyWiper, WhisperGate, AcidRain, Industroyer2, and RuRansom.
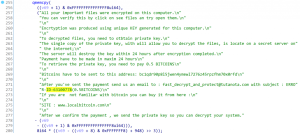
Kaspersky mentioned it found the assault makes an attempt by CryWiper in the previous couple of months. After infecting a goal, the malware left a word demanding, in keeping with Izvestia, 0.5 bitcoin and together with a pockets tackle the place the cost might be made.
Kaspersky
“After examining a sample of malware, we found out that this Trojan, although it masquerades as a ransomware and extorts money from the victim for ‘decrypting’ data, does not actually encrypt, but purposefully destroys data in the affected system,” Kaspersky’s report said. “Moreover, an analysis of the Trojan’s program code showed that this was not a developer’s mistake, but his original intention.”
CryWiper bears some resemblance to IsaacWiper, which focused organizations in Ukraine. Both wipers use the identical algorithm for producing pseudo-random numbers that go on to deprave focused recordsdata by overwriting the information inside them. The identify of the algorithm is the Mersenne Vortex PRNG. The algorithm isn’t used, so the commonality caught out.

Kaspersky
CryWiper shares a separate commonality with ransomware households often known as Trojan-Ransom.Win32.Xorist and Trojan-Ransom.MSIL.Agent. Specifically, the e-mail tackle within the ransom word of all three is similar.
The CryWiper pattern Kaspersky analyzed is a 64-bit executable file for Windows. It was written in C++ and compiled utilizing the MinGW-w64 toolkit and the GCC compiler. That’s an uncommon selection because it’s extra widespread for malware written in C++ to make use of Microsoft’s Visual Studio. One potential motive for this selection is that it offers the builders the choice of porting their code to Linux. Given the variety of particular calls CryWiper makes to Windows programming interfaces, this motive appears unlikely. The extra seemingly motive is that the developer writing the code was utilizing a non-Windows system.
Successful wiper assaults usually make the most of poor community safety. Kaspersky suggested community engineers to take precautions by utilizing:
- Behavioral file evaluation safety options for endpoint safety.
- Managed detection and response and safety operation heart that permit for well timed detection of an intrusion and take motion to reply.
- Dynamic evaluation of mail attachments and blocking of malicious recordsdata and URLs. This will make electronic mail assaults, probably the most widespread vectors, harder.
- Conducting common penetration testing and RedTeam tasks. This will assist to determine vulnerabilities within the group’s infrastructure, shield them, and thereby considerably cut back the assault floor for intruders.
- Threat information monitoring. To detect and block malicious exercise in a well timed method, it’s essential to have up-to-date details about the ways, instruments, and infrastructure of intruders.
Given Russia’s invasion of Ukraine and different geopolitical conflicts raging across the globe, the tempo of wiper malware isn’t prone to sluggish within the coming months.
“In many cases, wiper and ransomware incidents are caused by insufficient network security, and it is the strengthening of protection that should be paid attention to,” Friday’s Kaspersky report said. “We assume that the number of cyberattacks, including those using wipers, will grow, largely due to the unstable situation in the world.”
[ad_2]
