[ad_1]
Cybercriminal teams peddling subtle phishing kits that convert stolen card information into cell wallets have not too long ago shifted their focus to concentrating on prospects of brokerage providers, new analysis reveals. Undeterred by safety controls at these buying and selling platforms that block customers from wiring funds immediately out of accounts, the phishers have pivoted to utilizing a number of compromised brokerage accounts in unison to govern the costs of international shares.
Image: Shutterstock, WhataWin.
This so-called ‘ramp and dump‘ scheme borrows its identify from age-old “pump and dump” scams, whereby fraudsters buy a lot of shares in some penny inventory, after which promote the corporate in a frenzied social media blitz to construct up curiosity from different traders. The fraudsters dump their shares after the value of the penny inventory will increase to some extent, which normally then causes a pointy drop within the worth of the shares for legit traders.
With ramp and dump, the scammers don’t have to depend on ginning up curiosity within the focused inventory on social media. Rather, they are going to preposition themselves within the inventory that they want to inflate, utilizing compromised accounts to buy giant volumes of it after which dumping the shares after the inventory worth reaches a sure worth. In February 2025, the FBI stated it was looking for info from victims of this scheme.
“In this variation, the price manipulation is primarily the result of controlled trading activity conducted by the bad actors behind the scam,” reads an advisory from the Financial Industry Regulatory Authority (FINRA), a personal, non-profit group that regulates member brokerage companies. “Ultimately, the outcome for unsuspecting investors is the same—a catastrophic collapse in share price that leaves investors with unrecoverable losses.”
Ford Merrill is a safety researcher at SecAlliance, a CSIS Security Group firm. Merrill stated he has tracked latest ramp-and-dump exercise to a bustling Chinese-language neighborhood that’s fairly overtly promoting superior cell phishing kits on Telegram.
“They will often coordinate with other actors and will wait until a certain time to buy a particular Chinese IPO [initial public offering] stock or penny stock,” stated Merrill, who has been chronicling the fast maturation and development of the China-based phishing neighborhood over the previous three years.
“They’ll use all these victim brokerage accounts, and if needed they’ll liquidate the account’s current positions, and will preposition themselves in that instrument in some account they control, and then sell everything when the price goes up,” he stated. “The victim will be left with worthless shares of that equity in their account, and the brokerage may not be happy either.”
Merrill stated the early days of those phishing teams — between 2022 and 2024 — had been typified by phishing kits that used textual content messages to spoof the U.S. Postal Service or some native toll highway operator, warning a few delinquent transport or toll charge that wanted paying. Recipients who clicked the hyperlink and offered their fee info at a faux USPS or toll operator web site had been then requested to confirm the transaction by sharing a one-time code despatched by way of textual content message.
In actuality, the sufferer’s financial institution is sending that code to the cell quantity on file for his or her buyer as a result of the fraudsters have simply tried to enroll that sufferer’s card particulars right into a cell pockets. If the customer provides that one-time code, their fee card is then added to a brand new cell pockets on an Apple or Google machine that’s bodily managed by the phishers.
The phishing gangs sometimes load a number of stolen playing cards to digital wallets on a single Apple or Android machine, after which promote these telephones in bulk to scammers who use them for fraudulent e-commerce and tap-to-pay transactions.
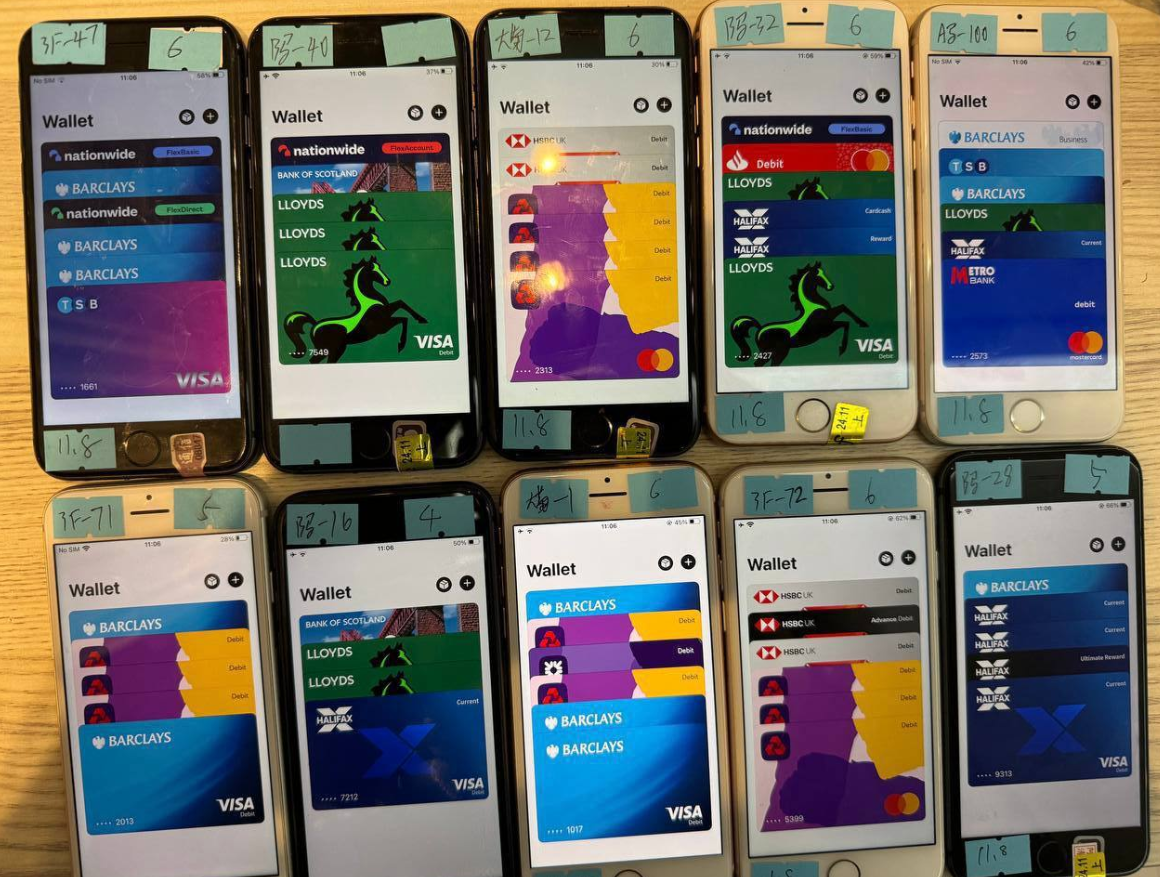
An picture from the Telegram channel for a well-liked Chinese cell phishing package vendor reveals 10 cellphones on the market, every loaded with 4-6 digital wallets from totally different monetary establishments.
This China-based phishing collective uncovered a significant weak point frequent to many U.S.-based monetary establishments that already require multi-factor authentication: The reliance on a single, phishable one-time token for provisioning cell wallets. Happily, Merrill stated many monetary establishments that had been caught flat-footed on this rip-off two years in the past have since strengthened authentication necessities for onboarding new cell wallets (akin to requiring the cardboard to be enrolled by way of the financial institution’s cell app).
But simply as squeezing one a part of a balloon merely forces the air trapped inside to bulge into one other space, fraudsters don’t go away while you make their present enterprise much less worthwhile: They simply shift their focus to a less-guarded space. And currently, that gaze has settled squarely on prospects of the main brokerage platforms, Merrill stated.
THE OUTSIDER
Merrill pointed to a number of Telegram channels operated by a few of the extra completed phishing package sellers, that are filled with movies demonstrating how each characteristic of their kits could be tailor-made to the attacker’s goal. The video snippet under comes from the Telegram channel of “Outsider,” a well-liked Mandarin-speaking phishing package vendor whose newest providing consists of a variety of ready-made templates for utilizing textual content messages to phish brokerage account credentials and one-time codes.
According to Merrill, Outsider is a girl who beforehand glided by the deal with “Chenlun.” KrebsOnSecurity profiled Chenlun’s phishing empire in an October 2023 story a few China-based group that was phishing cell prospects of greater than a dozen postal providers across the globe. In that case, the phishing websites had been utilizing a Telegram bot that despatched stolen credentials to the “@chenlun” Telegram account.
Chenlun’s phishing lures are despatched by way of Apple’s iMessage and Google’s RCS service and spoof one of many main brokerage platforms, warning that the account has been suspended for suspicious exercise and that recipients ought to log in and confirm some info. The missives embrace a hyperlink to a phishing web page that collects the shopper’s username and password, after which asks the person to enter a one-time code that can arrive by way of SMS.
The new phish package movies on Outsider’s Telegram channel solely characteristic templates for Schwab prospects, however Merrill stated the package can simply be tailored to focus on different brokerage platforms. One purpose the fraudsters are selecting on brokerage companies, he stated, has to do with the way in which they deal with multi-factor authentication.
Schwab purchasers are offered with two choices for second issue authentication once they open an account. Users who choose the choice to solely immediate for a code on untrusted gadgets can select to obtain it by way of textual content message, an automatic inbound cellphone name, or an outbound name to Schwab. With the “always at login” choice chosen, customers can select to obtain the code by the Schwab app, a textual content message, or a Symantec VIP cell app.
In response to questions, Schwab stated it frequently updates purchasers on rising fraud developments, together with this particular kind, which the corporate addressed in communications despatched to purchasers earlier this yr.
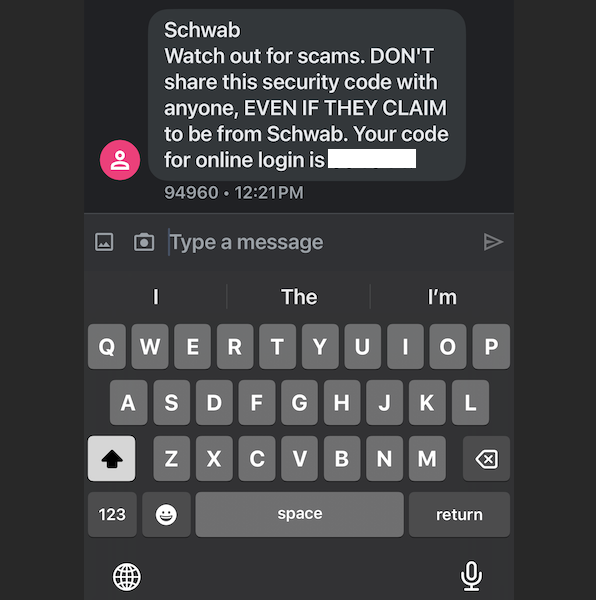
The 2FA textual content message from Schwab warns recipients in opposition to making a gift of their one-time code.
“That message focused on trading-related fraud, highlighting both account intrusions and scams conducted through social media or messaging apps that deceive individuals into executing trades themselves,” Schwab stated in a written assertion. “We are aware and tracking this trend across several channels, as well as others like it, which attempt to exploit SMS-based verification with stolen credentials. We actively monitor for suspicious patterns and take steps to disrupt them. This activity is part of a broader, industry-wide threat, and we take a multi-layered approach to address and mitigate it.”
Other well-liked brokerage platforms permit comparable strategies for multi-factor authentication. Fidelity requires a username and password on preliminary login, and affords the flexibility to obtain a one-time token by way of SMS, an automatic cellphone name, or by approving a push notification despatched by the Fidelity cell app. However, all three of those strategies for sending one-time tokens are phishable; even with the brokerage agency’s app, the phishers might immediate the person to approve a login request that they initiated within the app with the phished credentials.
Vanguard affords prospects a spread of multi-factor authentication decisions, together with the choice to require a bodily safety key along with one’s credentials on every login. A safety key implements a strong type of multi-factor authentication referred to as Universal 2nd Factor (U2F), which permits the person to finish the login course of just by connecting an enrolled USB or Bluetooth machine and urgent a button. The key works with out the necessity for any particular software program drivers, and the great factor about it’s your second issue can’t be phished.
THE PERFECT CRIME?
Merrill stated that in some ways the ramp-and-dump scheme is the right crime as a result of it leaves treasured few connections between the sufferer brokerage accounts and the fraudsters.
“It’s really genius because it decouples so many things,” he stated. “They can buy shares [in the stock to be pumped] in their personal account on the Chinese exchanges, and the price happens to go up. The Chinese or Hong Kong brokerages aren’t going to see anything funky.”
Merrill stated it’s unclear precisely how these perpetrating these ramp-and-dump schemes coordinate their actions, akin to whether or not the accounts are phished properly prematurely or shortly earlier than getting used to inflate the inventory worth of Chinese corporations. The latter risk would match properly with the prevailing human infrastructure these prison teams have already got in place.
For instance, KrebsOnSecurity not too long ago wrote about analysis from Merrill and different researchers displaying the phishers behind these slick cell phishing kits employed individuals to sit down for hours at a time in entrance of huge banks of cellphones getting used to ship the textual content message lures. These technicians had been wanted to reply in actual time to victims who had been supplying the one-time code despatched from their monetary establishment.

The ashtray says: You’ve been phishing all evening.
“You can get access to a victim’s brokerage with a one-time passcode, but then you sort of have to use it right away if you can’t set new security settings so you can come back to that account later,” Merrill stated.
The fast tempo of improvements produced by these China-based phishing distributors is due partially to their use of synthetic intelligence and huge language fashions to assist develop the cell phishing kits, he added.
“These guys are vibe coding stuff together and using LLMs to translate things or help put the user interface together,” Merrill stated. “It’s only a matter of time before they start to integrate the LLMs into their development cycle to make it more rapid. The technologies they are building definitely have helped lower the barrier of entry for everyone.”
[ad_2]
