[ad_1]

Microsoft’s warning on Wednesday that the China-sponsored actor Volt Typhoon attacked U.S. infrastructure put a tough emphasis on shows by cybersecurity and worldwide affairs specialists {that a} international warfare in our on-line world is pitting authoritarian regimes towards democracies.
Jump to:
China’s dedication to cyberwarfare
Microsoft’s notification identified that Volt Typhoon — which hit organizations in sectors spanning IT, communications, manufacturing, utility, transportation, building, maritime, authorities and training — has been pursuing a “living off the land” technique centered on knowledge exfiltration since 2021. The tactic usually makes use of social engineering exploits like phishing to entry networks invisibly by driving on respectable software program. It makes use of a Fortinet exploit to realize entry and makes use of legitimate accounts to persist (Figure A).
Figure A
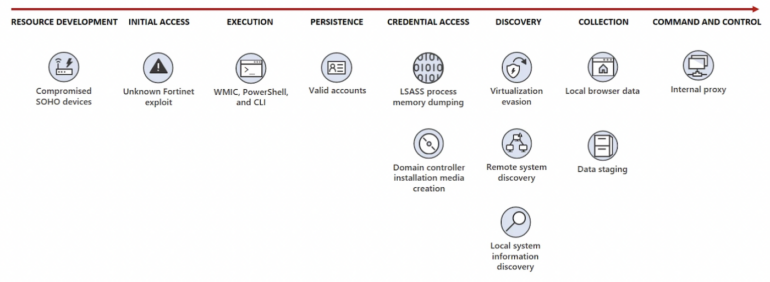
Nadir Izrael, the chief know-how officer and co-founder of the Armis safety agency, identified that China’s protection finances has been rising over time, reaching an estimated $178 billion in 2020. “This growing investment has enabled China to build up its cyber capabilities, with more than 50,000 cyber soldiers and an advanced cyberwarfare unit,” he stated.
He added that China’s funding in offensive cyber capabilities has created “a global weapon in its arsenal to rattle critical infrastructure across nearly every sector — from communications to maritime — and interrupt U.S. citizens’ lives.” He stated, “Cyberwarfare is an incredibly impactful, cost-effective tool for China to disrupt world order.”
According to Armis, he has been predicting these threats since January after discovering that 33% of world organizations usually are not taking the specter of cyberwarfare threats severely. He has been urging governments and companies throughout sectors to start out putting in procedures to counteract these threats.
“As the world becomes increasingly digitized, cyberwarfare is modern warfare,” Armis stated. “This has to be a wake-up call for the U.S. and western nations.”
At the WithSecure Sphere23 convention in Helsinki, Finland, earlier than this safety information had crossed the wires, Jessica Berlin, a Germany-based international coverage analyst and founding father of the consultancy CoStruct, stated the U.S., the European Union and different democracies haven’t woke up to the implications of cyberwarfare by Russia, China and North Korea. She stated these nations are engaged in a cybernetic world warfare — one which autocracies have the higher hand in as a result of they’ve absolutely acknowledged and embraced it and have dedicated to waging it as such.
She advised TechRepublic that tech and safety firms might play a key function in awakening residents and governments to this reality by being extra clear about assaults. She additionally famous the European Union’s General Data Protection Regulation, which has been in impact for 5 years, has been a strong software for oversight of digital data, knowledge provenance and misinformation on social platforms.
Professionalization of cybercrime lowers bar to entry
Stephen Robinson, a senior risk intelligence analyst at WithSecure, stated the cybercriminal ecosystem’s mirroring of respectable enterprise has made it simpler for state actors and fewer subtle teams to purchase what they will’t make. This professionalization of cybercrime has created a proper service sector. “They are outsourcing functions, hiring freelancers, subcontracting; criminal service providers have sprung up, and their existence is industrializing exploitation,” stated Robinson.
The success of the legal as-a-service mannequin is expedited by such frameworks as Tor nameless knowledge switch and cryptocurrency, famous Robinson, who delineated some darkish net service verticals.
- Initial entry brokers: These brokers are key as a result of they thrive within the service-oriented mannequin and are enablers. They use no matter methodology they will to realize entry after which provide that entry.
- Crypter as a service: Crypter is a software to cover a malware payload. And this, stated Robinson, has led to an arms race between malware and antimalware.
- Crypto jackers: These actors break right into a community and drop software program and are sometimes one of many first actors to take advantage of a server vulnerability. They represent a low risk but are a really robust indicator that one thing has occurred or will, in line with Robinson.
- Malware-as-a-service: Highly technical and with superior companies like help and contracts and entry to premium merchandise.
- Nation state actors: Nation state actors use the above instruments, which allow them to spin up campaigns and entry new victims with out being attributed.
WithSecure has a recent report on multi-point extortion ransomware teams that make use of a number of extortion methods, together with encryption, to strain victims for funds.
The agency’s evaluation of greater than 3,000 knowledge leaks by these teams confirmed that organizations within the U.S. had been essentially the most focused victims, adopted by Canada, the U.Okay., Germany, France and Australia.
In addition, the agency’s analysis confirmed that the development business accounted for 19% of the info leaks; the automotive business accounted for less than 6% of assaults.
“In pursuit of a bigger slice of the huge revenues of the ransomware industry, ransomware groups purchase capabilities from specialist e-crime suppliers in much the same way that legitimate businesses outsource functions to increase their profits,” stated Robinson. “This ready supply of capabilities and information is being taken advantage of by more and more cyberthreat actors, ranging from lone, low-skilled operators right up to nation state APTs. Ransomware didn’t create the cybercrime industry, but it has really thrown fuel on the fire.”
The agency provided an instance that resembled the mass looting of a division retailer after the door had been left ajar. One group was victimized by 5 risk actors, every with completely different aims and representing a distinct sort of cybercrime service: the Monti ransomware group, Qakbot malware-as-a-service, the 8220 crypto-jacking gang, an unnamed preliminary entry dealer and a subset of Lazarus Group related to North Korea.
In these incidents, WithSecure risk intelligence reported encountering six distinct examples of the “as a service” mannequin in use within the kill chains noticed (Figure B).
Figure B
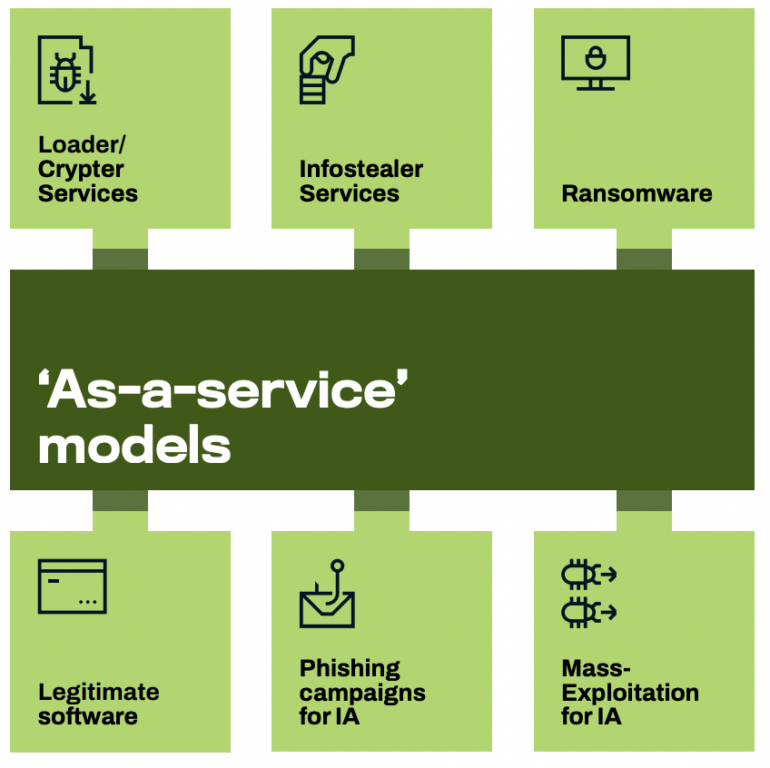
According to the report, this professionalization development makes the experience and assets to assault organizations accessible to lesser-skilled or poorly resourced risk actors. The report predicts it’s possible the variety of attackers and the scale of the cybercrime business will develop within the coming years.
How to mitigate Volt Typhoon
In Microsoft’s report about Volt Typhoon, the corporate stated detecting an exercise that makes use of regular sign-in channels and system binaries requires behavioral monitoring and remediation requires closing or altering credentials for compromised accounts. In these instances, Microsoft means that safety operations groups ought to study the exercise of compromised accounts for any malicious actions or uncovered knowledge.
To preclude this number of assaults, Microsoft urged the following tips:
- Enforce robust multifactor authentication insurance policies through the use of {hardware} safety keys, passwordless sign-in and password expiration guidelines and deactivating unused accounts.
- Turn on assault floor discount guidelines to dam or audit actions related to this risk.
- Enable Protective Process Light for LSASS on Windows 11 units. New enterprise-joined Windows 11 (22H2 replace) installs have this function enabled by default, per the corporate.
- Enable Windows Defender Credential Guard, which is turned on by default for organizations utilizing the Enterprise version of Windows 11.
- Turn on cloud-delivered safety in Microsoft Defender Antivirus.
- Run endpoint detection and response in block mode so Microsoft Defender for Endpoint can block malicious artifacts.
