[ad_1]

Getty Images
Microsoft on Thursday fingered Russia’s army intelligence arm because the possible wrongdoer behind ransomware assaults final month that focused Polish and Ukrainian transportation and logistics organizations.
If the evaluation by members of the Microsoft Security Threat Intelligence Center (MSTIC) is right, it could possibly be trigger for concern for the US authorities and its European counterparts. Poland is a member of NATO and a staunch supporter of Ukraine in its bid to stave off an unprovoked Russian invasion. The hacking group the software program firm linked to the cyberattacks—often known as Sandworm in wider analysis circles and Iridium in Redmond, Washington—is among the world’s most gifted and harmful and is extensively believed to be backed by Russia’s GRU army intelligence company.
Sandworm has been definitively linked to the NotPetya wiper assaults of 2017, a worldwide outbreak {that a} White House evaluation stated brought about $10 billion in damages, making it the most expensive hack in historical past. Sandworm has additionally been definitively tied to hacks on Ukraine’s energy grid that brought about widespread outages in the course of the coldest months of 2016 and once more in 2017.
Enter Prestige
Last month, Microsoft stated that Poland and Ukraine transportation and logistics organizations had been the goal of cyberattacks that used never-before-seen ransomware that introduced itself as Prestige. The menace actors, Microsoft stated, had already gained management over the sufferer networks. Then in a single hour on October 11, the hackers deployed Prestige throughout all its victims.
Once in place, the ransomware traversed all information on the contaminated pc’s system and encrypted the contents of information that resulted in .txt, .png, gpg, and greater than 200 different extensions. Prestige then appended the extension .enc to the prevailing extension of the file. Microsoft attributed the assault to an unknown menace group it dubbed DEV-0960.
On Thursday, Microsoft up to date the report back to say that primarily based on forensic artifacts and overlaps in victimology, tradecraft, capabilities, and infrastructure, researchers decided DEV-0960 was very possible Iridium.
“The Prestige campaign may highlight a measured shift in Iridium’s destructive attack calculus, signaling increased risk to organizations directly supplying or transporting humanitarian or military assistance to Ukraine,” MSTIC members wrote. “More broadly, it may represent an increased risk to organizations in Eastern Europe that may be considered by the Russian state to be providing support relating to the war.”
Thursday’s replace went on to say that the Prestige marketing campaign is distinct from harmful assaults previously two weeks that used malware tracked as AprilAxe (ArguePatch)/CaddyWiper or Foxblade (HermeticWiper) to focus on a number of vital infrastructures in Ukraine. While the researchers stated they nonetheless don’t know what menace group is behind these acts, they now have sufficient proof to finger Iridium because the group behind the Prestige assaults. Microsoft is within the means of notifying clients who’ve been “impacted by Iridium but not yet ransomed,” they wrote.
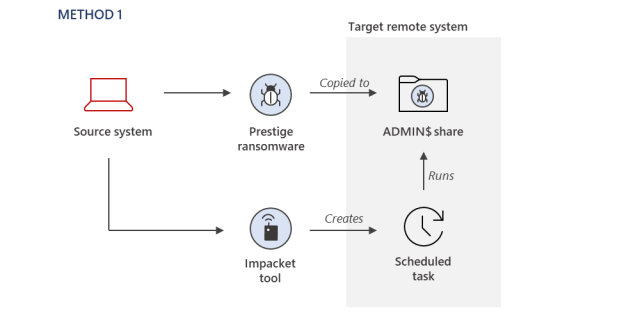
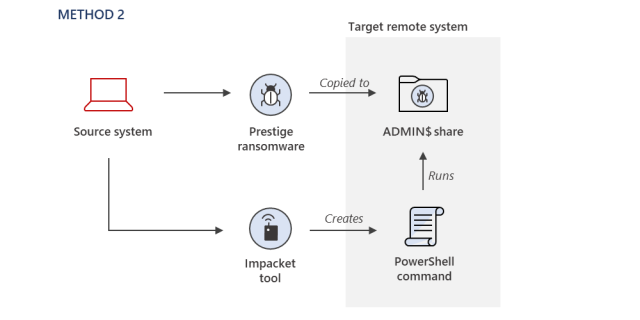
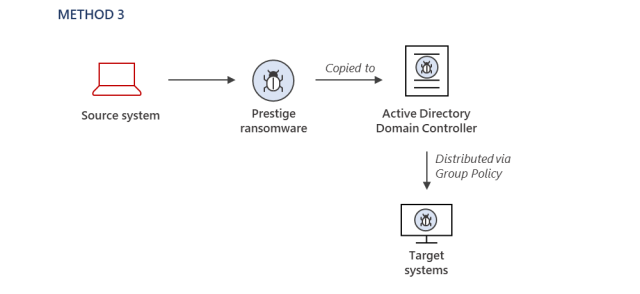
Underscoring the sophistication of the assaults, Iridium members used a number of strategies for deploying Prestige on the focused networks. They included:
Windows scheduled duties
Microsoft
encoded PowerShell instructions, and
Microsoft
Default Domain Group Policy Objects
Microsoft
“Most ransomware operators develop a preferred set of tradecraft for their payload deployment and execution, and this tradecraft tends to be consistent across victims, unless a security configuration prevents their preferred method,” MSTIC members defined. “For this Iridium activity, the methods used to deploy the ransomware varied across the victim environments, but it does not appear to be due to security configurations preventing the attacker from using the same techniques. This is especially notable as the ransomware deployments all occurred within one hour.”
The publish comprises technical indicators that may assist individuals work out if they’ve been focused.
