[ad_1]
Microsoft has disclosed particulars of a now-patched safety flaw in Apple macOS that could possibly be exploited by an attacker to get round safety protections imposed to forestall the execution of malicious purposes.
The shortcoming, dubbed Achilles (CVE-2022-42821, CVSS rating: 5.5), was addressed by the iPhone maker in macOS Ventura 13, Monterey 12.6.2, and Big Sur 11.7.2, describing it as a logic difficulty that could possibly be weaponized by an app to avoid Gatekeeper checks.
“Gatekeeper bypasses akin to this could possibly be leveraged as a vector for preliminary entry by malware and different threats and will assist enhance the success charge of malicious campaigns and assaults on macOS,” Jonathan Bar Or of the Microsoft 365 Defender Research Team stated.
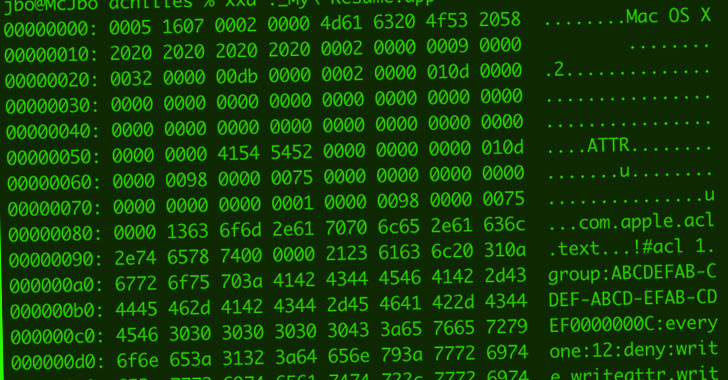
Gatekeeper is a safety mechanism designed to make sure that solely trusted apps run on the working system. This is enforced by the use of an prolonged attribute known as “com.apple.quarantine” that is assigned to recordsdata downloaded from the web. It is analogous to the Mark of the Web (MotW) flag in Windows.
Thus when an unsuspecting person downloads a doubtlessly dangerous app that impersonates a bit of reliable software program, the Gatekeeper function prevents the app from being run as it is not validly signed and notarized by Apple.
Even in situations the place an app is accepted by Apple, customers are displayed a immediate when it is launched for the primary time to hunt their specific consent.
Given the essential function performed by Gatekeeper in macOS, it is laborious to not think about the implications of sidestepping the safety barrier, which might successfully allow menace actors to deploy malware on the machines.
The Achilles vulnerability recognized by Microsoft exploits a permission mannequin known as Access Control Lists (ACLs) so as to add extraordinarily restrictive permissions to a downloaded file (i.e., “everybody deny write,writeattr,writeextattr,writesecurity,chown”), thereby blocking Safari from setting the quarantine prolonged attribute.
In a hypothetical assault situation, an adversary might embrace the approach to craft a rogue app and host it on a server, which might then be delivered to a doable goal by way of social engineering, malicious adverts, or a watering gap.
The methodology additionally circumvents Apple’s newly launched Lockdown Mode in macOS Ventura – an opt-in restrictive setting to counter zero-click exploits – necessitating that customers apply the most recent updates to mitigate threats.
“Fake apps stay one of many high entry vectors on macOS, indicating Gatekeeper bypass strategies are a gorgeous and even a crucial functionality for adversaries to leverage in assaults,” Bar Or stated.
[ad_2]