[ad_1]
Google has eliminated two new malicious dropper apps which were detected on the Play Store for Android, one in all which posed as a way of life app and was caught distributing the Xenomorph banking malware.
“Xenomorph is a trojan that steals credentials from banking functions on customers’ units,” Zscaler ThreatLabz researchers Himanshu Sharma and Viral Gandhi mentioned in an evaluation printed Thursday.
“It can be able to intercepting customers’ SMS messages and notifications, enabling it to steal one-time passwords and multi-factor authentication requests.”
The cybersecurity agency mentioned it additionally discovered an expense tracker app that exhibited related habits, however famous that it could not extract the URL used to fetch the malware artifact.
The two malicious apps are as follows –
- Todo: Day supervisor (com.todo.daymanager)
- 経費キーパー (com.setprice.bills)
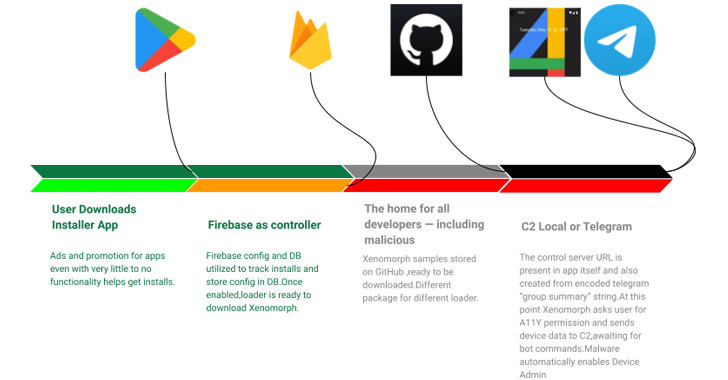
Both the apps operate as a dropper, that means the apps themselves are innocent and are a conduit to retrieve the precise payload, which, within the case of Todo, is hosted on GitHub.
Xenomorph, first documented by ThreatFabric earlier this February, is thought to abuse Android’s accessibility permissions to conduct overlay assaults, whereby faux login screens are introduced atop legit financial institution apps to steal sufferer’s credentials.
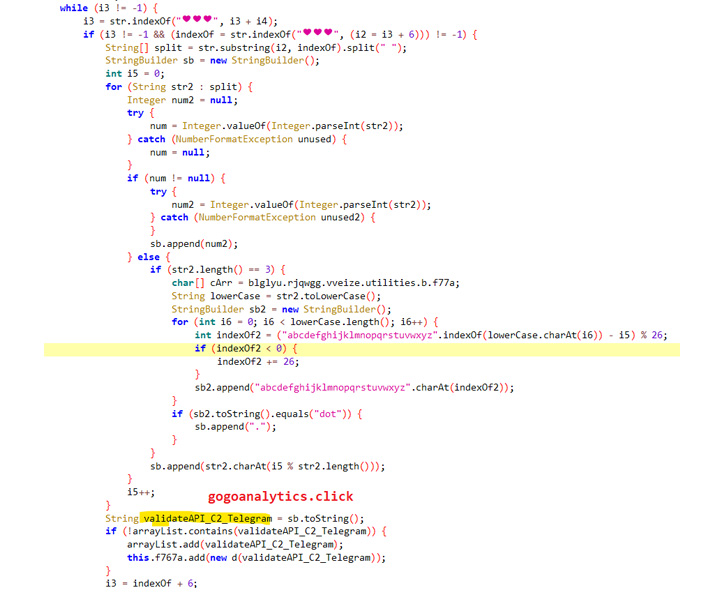
What’s extra, the malware leverages a Telegram channel’s description to decode and assemble the command-and-control (C2) area used to obtain extra instructions.
The growth follows the discovery of 4 rogue apps on Google Play that had been discovered directing victims to malicious web sites as a part of an adware and information-stealing marketing campaign. Google advised The Hacker News that it has since banned the developer.