[ad_1]
Cybercriminals lure content material creators with guarantees of cutting-edge AI wizardry, solely to aim to steal their information or hijack their gadgets as a substitute
17 Apr 2025
•
,
3 min. learn

The craze round generative AI instruments isn’t simply reshaping industries – it additionally gives fertile floor for cybercriminals, who’re at all times fast to piggyback on the attract of the newest huge factor in tech. So what if, as a substitute of downloading an AI‑generated video from CapCut or one other related device, you had your information stolen or gave management of your pc to a stranger?
The menace isn’t hypothetical – safety researchers have beforehand noticed campaigns that exploited CapCut’s recognition to distribute a number of infostealers and different malware. Let’s now look briefly at one other marketing campaign that’s focusing on folks considering AI-powered content material by promising premium variations of well-liked software program reminiscent of CapCut, Adobe Express and Canva.
The artwork of the lure
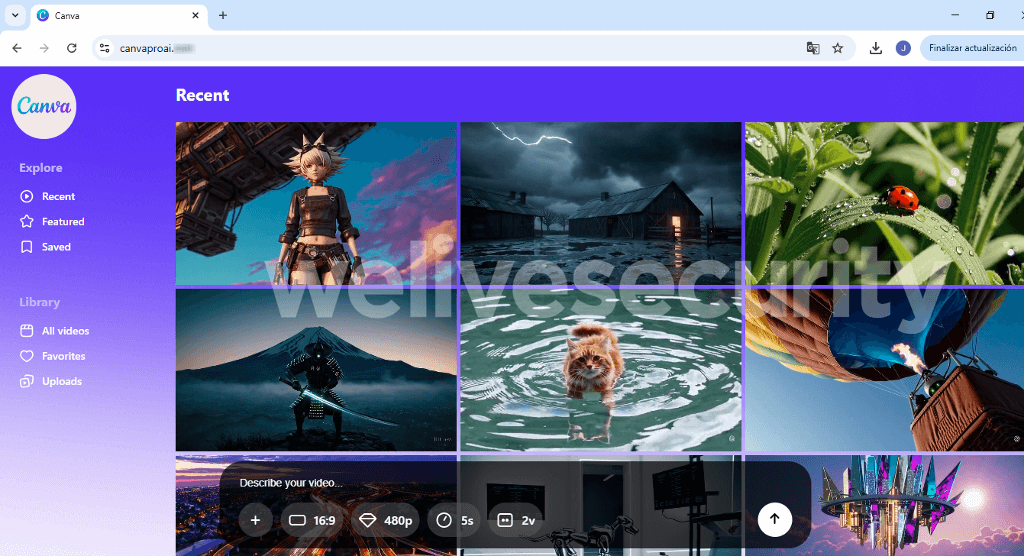
The instance under, noticed by X consumer g0njxa, reveals a web site that impersonates CapCut, a device usually utilized by TikTok creators, and purports to be CapCut’s premium model. (Note that the precise premium model known as “CapCut Pro” or referred to easily as “Pro” on the web site, not “CapCutProAI” as within the screenshot.)
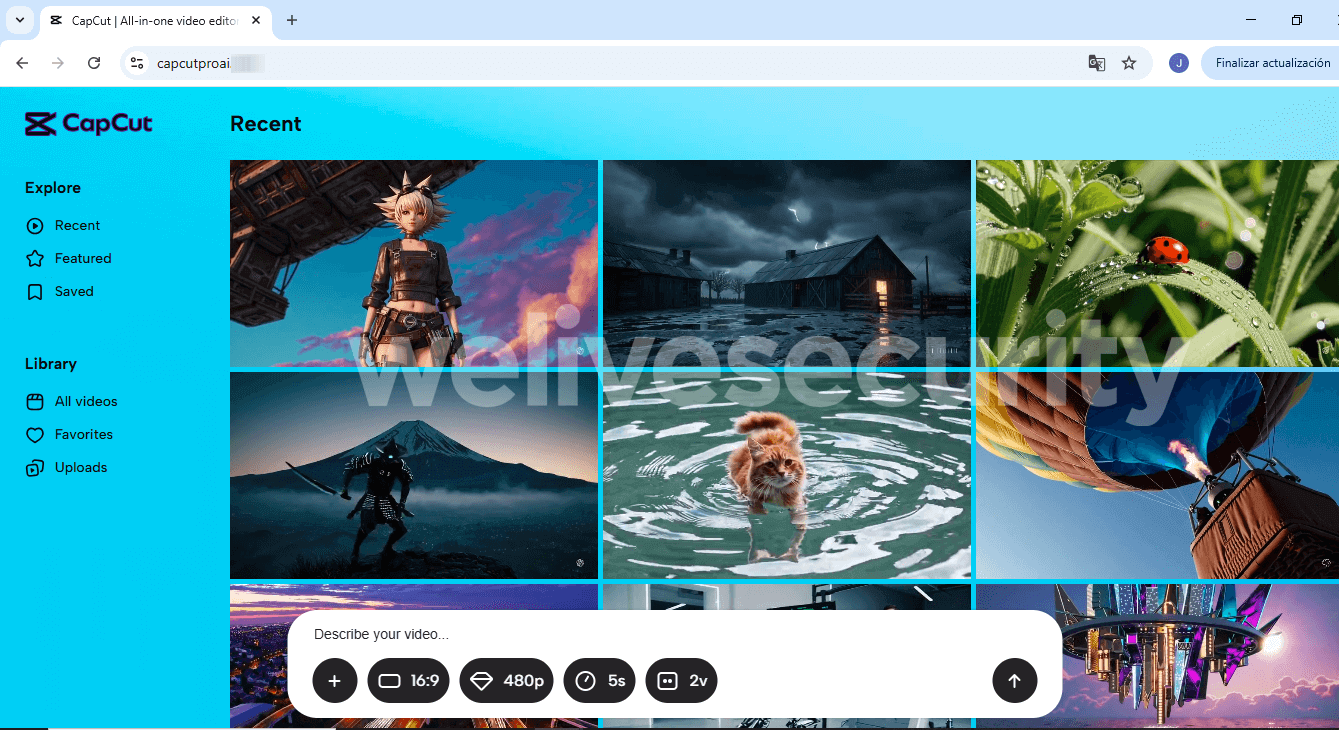
After you land on the pretend website, you’re requested to enter a immediate or add a reference file. If you comply, the positioning will mimic processing the request.
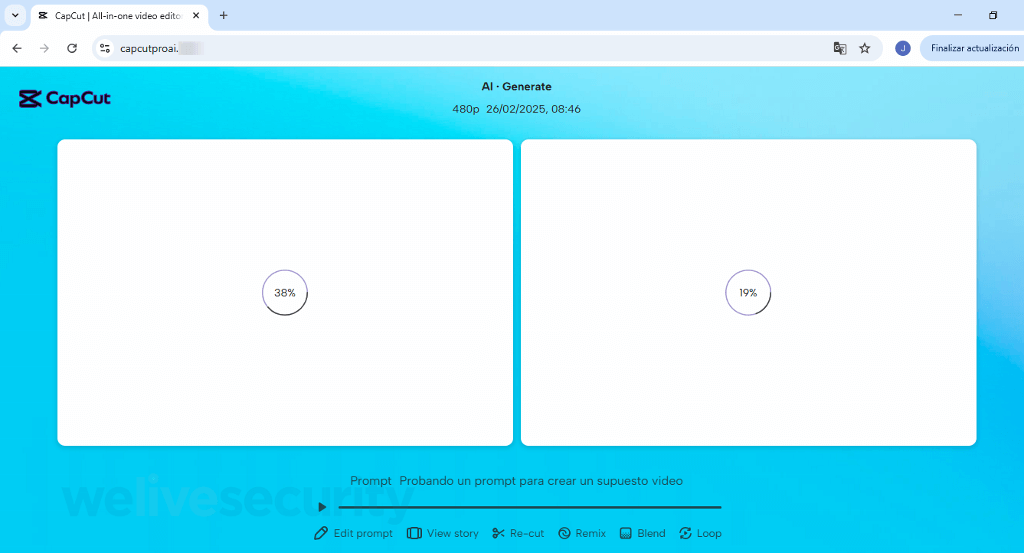
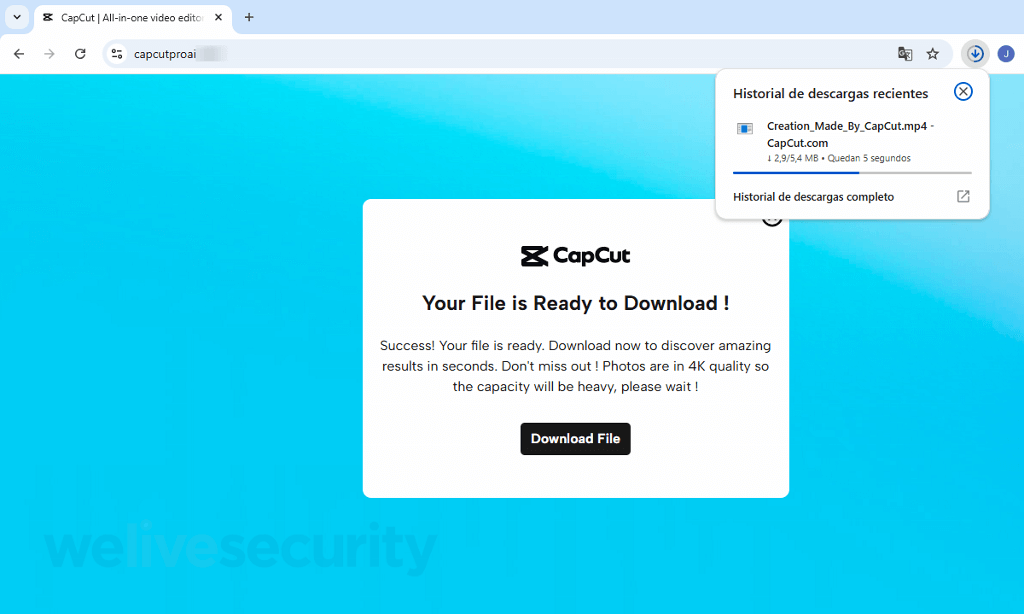
Once the anticipation is constructed and the lure is sprung, you’re prompted to obtain your shiny new “creation”. Needles to say, the file, referred to as Creation_Made_By_CapCut.mp4 – CapCut.com, is way from what it purports to be. In actuality, it’s an executable for distant entry software program. Fast ahead just a few clicks and, except different safeguards kick in, you may be surrendering management of your system to crooks.
Here are two extra websites that masquerade as the true deal and are a part of the identical marketing campaign:
Faraway, so shut
For context, whereas respectable distant entry instruments, reminiscent of ConnectWise ScreenConnect, TeamViewer and AnyDesk, are invaluable for IT professionals offering technical help, within the unsuitable fingers they are often misused to take over management of your pc for malicious ends. These embrace information theft, set up of ransomware or different malware, and utilizing the compromised machine as a launch pad for assaults at different gadgets.
These sorts of threats additionally loom massive on company networks, as menace actors can, for instance, distribute moveable, self-contained executables for respectable distant monitoring and administration (RMM) software program that circumvents admin privileges and obviates the necessity for full software program set up.
“Most remote control applications come with the option to generate a preconfigured executable to connect to a specific IP address or user. This is useful for remote assistance, but also for attackers. The victim simply has to open the file, and in a couple of clicks, they may unwittingly give control of their computer to a cybercriminal,” says Martina López, a safety researcher with ESET’s lab in Latin America.
Word to the sensible
A few easy steps will go a great distance towards protecting you secure:
- When downloading new software program, be certain to get it from the respectable supply, usually the writer’s official web site
- Avoid clicking on unsolicited hyperlinks in e mail or social media messages that usually declare to result in such web sites – the messages could also be pretend
- The similar goes for adverts – you’re higher off navigating to the web site instantly by typing it in your browser or trying to find it (with a essential eye, although) in your search engine of alternative
- Inspect the web site’s URL – software program makers don’t usually sport varied oddball extensions in URLs or sneaky “alternate” variations (suppose “CapCutProAI”)
- Make certain your working system, browser, and different software program are updated to guard in opposition to identified vulnerabilities
- Use multi-layered safety software program, in addition to stick with different fundamental cybersecurity hygiene practices, reminiscent of robust and distinctive passwords and enabling two-factor authentication on all of your on-line accounts
Needless to say, that is neither the primary nor final time CapCut customers have been focused by cybercriminals, and these examples simply present that cybercriminals are at all times keen to use belief and the newest huge factor in tech.
The excellent news is that that whereas these ploys are sometimes slick, they’re not invincible. Your vigilance is your finest protect in opposition to scammers’ ways.
[ad_2]


