[ad_1]
Tens of thousands and thousands of credential-based assaults concentrating on two widespread varieties of servers boiled right down to a small fraction of the passwords that shaped a listing of leaked credentials, often called the RockYou2021 record.
Vulnerability administration agency Rapid7, by way of its community of honeypots, recorded each try to compromise these servers over a 12-month interval, discovering that the tried credential assaults resulted in 512,000 permutations. Almost all of these passwords (99.997%) are included in a standard password record — the RockYou2021 file, which has 8.4 billion entries — suggesting that attackers, or the subset of menace actors attacking Rapid7’s honeypots, are sticking to a standard playbook.
The overlap in all of the assaults additionally counsel attackers are taking the straightforward street, says Tod Beardsley, director of analysis at Rapid7.
“We know now, in a provable and demonstrable manner, that no person — 0% of attackers — is making an attempt to be artistic in terms of unfocused, untargeted assaults throughout the Internet,” he says. “Therefore, it’s extremely simple to keep away from this sort of opportunistic assault, and it takes little or no effort to take this menace off the desk totally, with trendy password managers and configuration controls.”
Every 12 months, safety companies current analysis suggesting customers are persevering with to choose unhealthy passwords. In October 2021, for instance, a cybersecurity researcher in Tel Aviv, Israel, discovered he might recuperate the passwords to 70% of the wi-fi networks as he pedaled previous, actually because they used a cellphone quantity because the password. In 2019, an analysis of passwords leaked to the Internet discovered that the highest password was “123456,” adopted by “123456789” and “qwerty,” though it is unclear whether or not these leaks included outdated or not often used accounts with out password insurance policies.
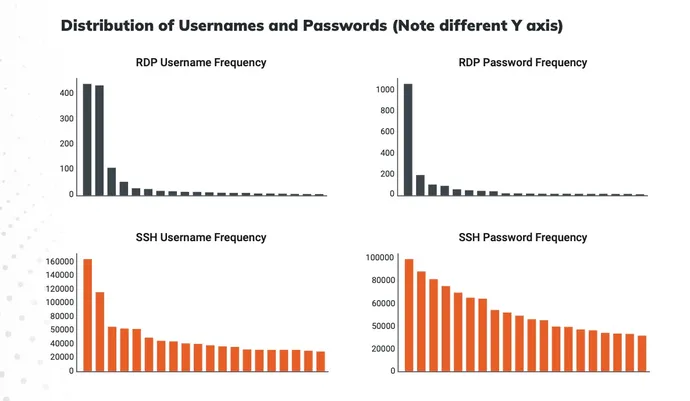
In this case, nevertheless, Rapid7 researchers targeted on the widespread passwords utilized by attackers reasonably than defenders, so the evaluation applies to attackers’ guesses in brute-force assaults. Such assaults have risen dramatically in the course of the COVID-19 pandemic, with password-guessing turning into the preferred methodology of assault in 2021, in keeping with an evaluation by cybersecurity agency ESET.
“With the rising adoption of each distant work and cloud infrastructures, the variety of folks accessing company data methods throughout the web has skyrocketed,” Rapid7 said in its report. “As with so many issues in safety, the addition of comfort and complexity has made the duty of defending these methods far tougher.”
One Year, a Half-Million Passwords
Rapid7’s analysis used credential information gathered from its Remote Desktop Protocol (RDP) and Secure Shell (SSH) honeypots between Sept. 10, 2021, and Sept. 9, 2022, detecting tens of thousands and thousands of makes an attempt to hook up with the corporate’s honeypots. The overwhelming majority of assaults tried to achieve entry to the SSH honeypots, with 97% of the greater than 500,000 distinctive passwords concentrating on the mock SSH servers, in keeping with Rapid7. The assaults concentrating on each SSH and RDP got here from about 216,000 distinctive supply IP addresses.
The half-million passwords signify lower than a a hundredth of a % of the permutations within the RockYou21 information set.
“The visitors we’re seeing is indicating that these are off-the-shelf assaults with primarily no customized configuration,” Beardsley says. “To put it one other manner, if there was any customization that ventured past the inventory set of passwords, we might have seen it in these samples.”
While the info says little about whether or not customers are deciding on poor passwords, the choice does point out that attackers are taking the best path of their assaults. As is obvious from the info, attackers aren’t trying each entry on the RockYou2021 record, however a a lot smaller quantity. In addition, solely a handful of passwords and usernames are the most typical, dominating the distribution of passwords.
Top RDP usernames are “administrator,” “person,” and “admin,” whereas the highest SSH usernames are “root,” “admin,” and “nproc.” Bad passwords — equivalent to “admin,” “password,” “123456,” and an empty string indicating no password — are the preferred passwords tried by attackers.
Attackers Just Assume Users Use “Lame” Passwords
The examine did not mirror poor password creation by customers however reasonably that attackers consider that making an attempt just a few poorly chosen passwords towards their targets are a worthwhile guessing sport, says Rapid7’s Beardsley.
“We cannot say exactly how profitable attackers are with these lists of lame passwords, however primary economics tells us that they have to be getting at the least some worth out of those assaults, or else we would not be seeing thousands and thousands of makes an attempt over the 12 months,” he says. “My suspicion is that whoever is operating these bots are operating these assaults primarily at very low value, and it is worthwhile sufficient to run this sort of assault with solely occasional wins.”
Organizations ought to repeatedly monitor methods for default and simply guessable passwords, which implies operating the RockYou2021 record of stolen credentials towards uncovered and inner methods. Rapid7 additionally recommends paying explicit consideration to external-facing SSH and RDP servers, in addition to Internet of Things methods that will not have easy-to-change passwords.
In addition, firms ought to educate staff to make use of password managers to make robust, distinctive password creation simple, Beardsley says.
“By using a password supervisor, you’ve gotten the power to generate a totally random password — one which definitely isn’t within the RockYou set — and have a unique one for each service you provide,” he says. “It all is determined by being conscious of the menace, however when you cross that hurdle, it is simple to keep away from turning into a sufferer.”
