[ad_1]
An ongoing evaluation of the KmsdBot botnet has raised the likelihood that it is a DDoS-for-hire service provided to different risk actors.
This relies on the completely different industries and geographies that have been attacked, net infrastructure firm Akamai mentioned. Among the notable targets included FiveM and RedM, that are recreation modifications for Grand Theft Auto V and Red Dead Redemption 2, in addition to luxurious manufacturers and safety companies.
KmsdBot is a Go-based malware that leverages SSH to contaminate techniques and perform actions like cryptocurrency mining and launch instructions utilizing TCP and UDP to mount distributed denial-of-service (DDoS) assaults.
However, an absence of an error-checking mechanism within the malware supply code brought about the prison operators to inadvertently crash their very own botnet final month.
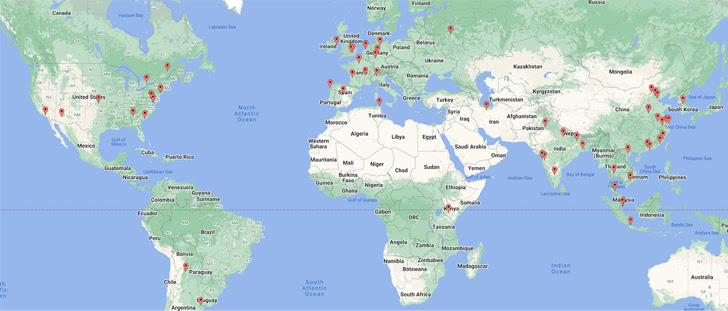
“Based on noticed IPs and domains, nearly all of the victims are situated in Asia, North America, and Europe,” Akamai researchers Larry W. Cashdollar and Allen West mentioned. “The presence of those instructions tracks with earlier observations of focused gaming servers and gives a glimpse into the purchasers of this botnet for rent.”
Akamai, which examined the assault visitors, recognized 18 completely different instructions that KmsdBot accepts from a distant server, one in all which, dubbed “bigdata,” caters to sending junk packets containing massive quantities of information to a goal in an try and exhaust its bandwidth.
Also included are instructions corresponding to “fivem” and “redm” which might be designed to focus on online game mod servers, alongside a “scan” instruction that “seems to focus on particular paths inside the goal setting.”
Charting the an infection makes an attempt of the botnet alerts minimal exercise within the Russian territory and neighboring areas, probably providing a clue as to its origins.
An additional breakdown of the assault instructions noticed over a 30-day time interval reveals “bigdata” main with a frequency of greater than 70. Calls to “fivem” have occurred 45 instances, whereas “redm” has seen lower than 10 calls.
“This tells us that though gaming servers are a selected goal provided, it might not be the one business that’s being hit with these assaults,” the researchers mentioned. “Support for a number of kinds of servers will increase the general usability of this botnet and seems to be efficient in driving in clients.”
The KmsdBot botnet, in its present kind, does not search persistence on a machine, which means its unintentional disruption requires the attackers to rebuild the botnet from scratch. However, there are indications that the botnet could also be attempting to stage a return.
“I did see an infection makes an attempt once more about 24-48 hours after the bot went down after which assault instructions began coming again in once more round 24 hours after that,” Cashdollar instructed The Hacker News. “But presently, the final identified C2 seems to be null routed and the bot has been quiet.”
The findings come per week after Microsoft detailed a cross-platform botnet often known as MCCrash that comes with capabilities to hold out DDoS assaults towards personal Minecraft servers.
[ad_2]