[ad_1]
Until earlier this week, the help web site for networking tools vendor Juniper Networks was exposing doubtlessly delicate info tied to buyer merchandise, together with which units clients purchased, in addition to every product’s guarantee standing, service contracts and serial numbers. Juniper mentioned it has since fastened the issue, and that the inadvertent knowledge publicity stemmed from a current improve to its help portal.

Sunnyvale, Calif. based mostly Juniper Networks makes high-powered Internet routers and switches, and its merchandise are utilized in a number of the world’s largest organizations. Earlier this week KrebsOnSecurity heard from a reader accountable for managing a number of Juniper units, who discovered he might use Juniper’s buyer help portal to seek out system and help contract info for different Juniper clients.
Logan George is a 17-year-old intern working for a corporation that makes use of Juniper merchandise. George mentioned he discovered the information publicity earlier this week by chance whereas looking for help info on a selected Juniper product.
George found that after logging in with an everyday buyer account, Juniper’s help web site allowed him to listing detailed details about nearly any Juniper system bought by different clients. Searching on Amazon.com within the Juniper portal, for instance, returned tens of hundreds of information. Each file included the system’s mannequin and serial quantity, the approximate location the place it’s put in, in addition to the system’s standing and related help contract info.
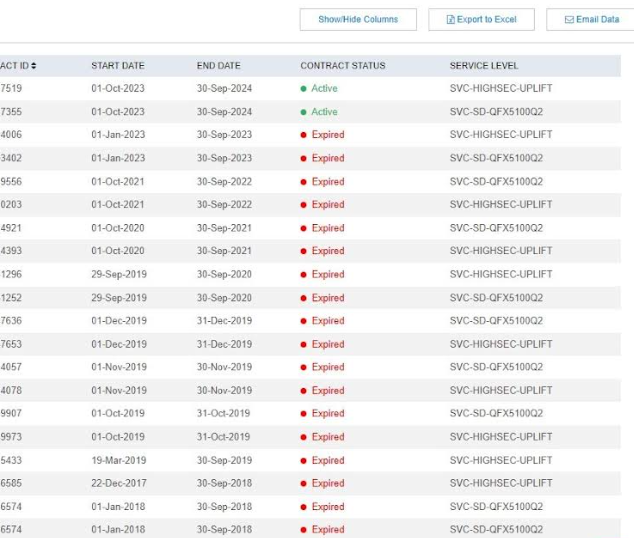
Information uncovered by the Juniper help portal. Columns not pictured embrace Serial Number, Software Support Reference quantity, Product, Warranty Expiration Date and Contract ID.
George mentioned the uncovered help contract info is doubtlessly delicate as a result of it exhibits which Juniper merchandise are probably to be missing crucial safety updates.
“If you don’t have a support contract you don’t get updates, it’s as simple as that,” George mentioned. “Using serial numbers, I could see which products aren’t under support contracts. And then I could narrow down where each device was sent through their serial number tracking system, and potentially see all of what was sent to the same location. A lot of companies don’t update their switches very often, and knowing what they use allows someone to know what attack vectors are possible.”
In a written assertion, Juniper mentioned the information publicity was the results of a current improve to its help portal.
“We were made aware of an inadvertent issue that allowed registered users to our system to access serial numbers that were not associated with their account,” the assertion reads. “We acted promptly to resolve this issue and have no reason to believe at this time that any identifiable or personal customer data was exposed in any way. We take these matters seriously and always use these experiences to prevent further similar incidents. We are actively working to determine the root cause of this defect and thank the researcher for bringing this to our attention.”
The firm has not but responded to requests for details about precisely when these overly permissive consumer rights had been launched. However, the modifications might date again to September 2023, when Juniper introduced it had rebuilt its buyer help portal.
George instructed KrebsOnSecurity the back-end for Juniper’s help web site seems to be supported by Salesforce, and that Juniper seemingly didn’t have the right consumer permissions established on its Salesforce property. In April 2023, KrebsOnSecurity revealed analysis exhibiting {that a} stunning variety of organizations — together with banks, healthcare suppliers and state and native governments — had been leaking personal and delicate knowledge because of misconfigured Salesforce installations.
Nicholas Weaver, a researcher at University of California, Berkeley’s International Computer Science Institute (ICSI) and lecturer at UC Davis, mentioned the complexity layered into fashionable tech help portals leaves a lot room for error.
“This is a reminder of how hard it is to build these large systems like support portals, where you need to be able to manage gazillions of users with distinct access roles,” Weaver mentioned. “One minor screw up there can produce hilarious results.”
Last month, pc maker Hewlett Packard Enterprise introduced it could purchase Juniper Networks for $14 billion, reportedly to assist beef up the 100-year-old know-how firm’s synthetic intelligence choices.
Update, 11:01 a.m. ET: An earlier model of this story quoted George as saying he was capable of see help info for the U.S. Department of Defense. George has since clarified that whereas one block of system information he discovered was labeled “Department of Defense,” that file seems to belong to a special nation.
[ad_2]
