[ad_1]

Two zero-day vulnerabilities affecting Ivanti’s Connect Secure VPN and Policy Secure community entry management (NAC) home equipment are actually below mass exploitation.
As found by menace intelligence firm Volexity, which additionally first noticed the zero-days being utilized in assaults since December, a number of menace teams chain the CVE-2023-46805 authentication bypass and the CVE-2024-21887 command injection vulnerabilities in widespread assaults beginning January 11.
“Victims are globally distributed and differ vastly in measurement, from small companies to among the largest organizations on the planet, together with a number of Fortune 500 corporations throughout a number of business verticals,” Volexity warned right now.
The attackers backdoored their targets’ techniques utilizing a GIFTEDVISITOR webshell variant which was discovered on tons of of home equipment.
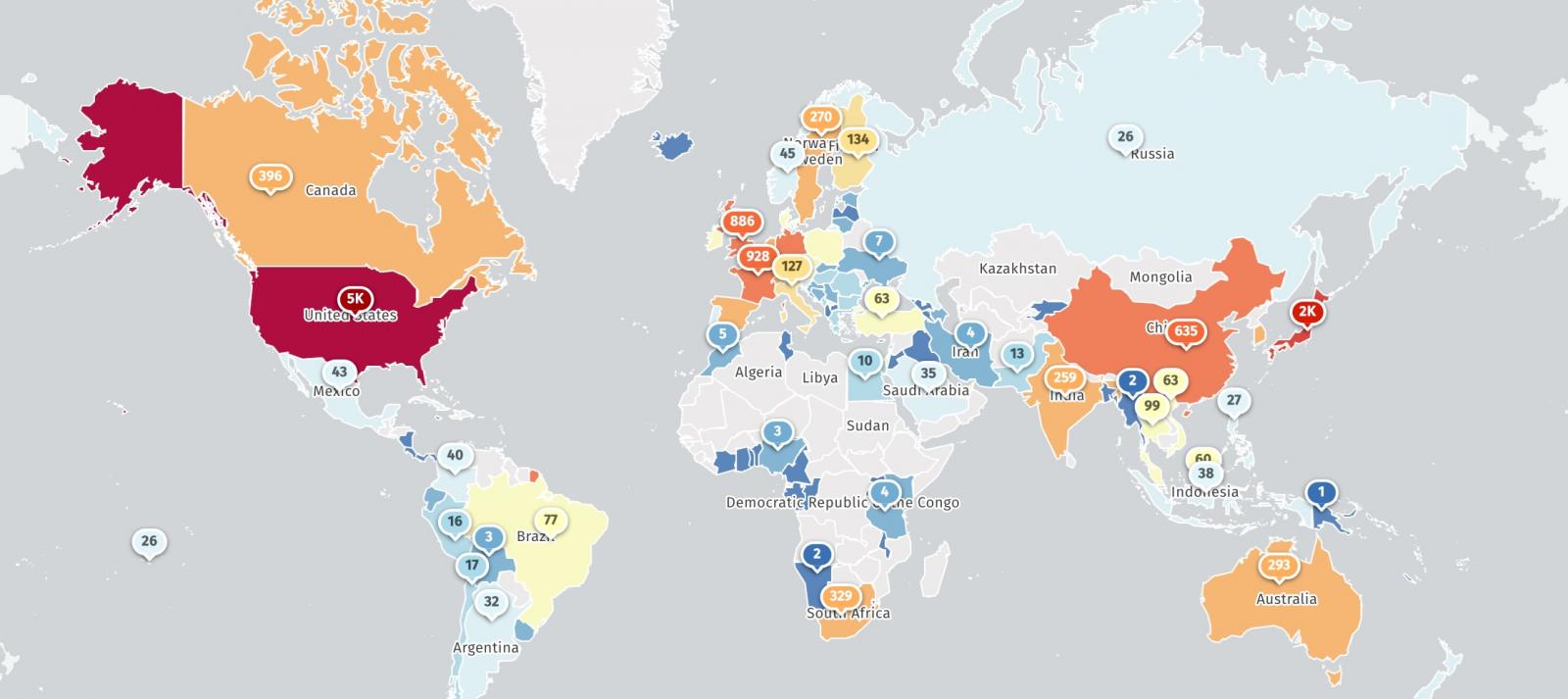
“On Sunday, January 14, 2024, Volexity had recognized over 1,700 ICS VPN home equipment that had been compromised with the GIFFEDVISITOR webshell. These home equipment seem to have been indiscriminately focused, with victims all around the world,” Volexity stated.
The listing of victims found by Volexity thus far contains authorities and navy departments worldwide, nationwide telecommunications corporations, protection contractors, know-how corporations, banking, finance, and accounting organizations, worldwide consulting outfits, and aerospace, aviation, and engineering corporations.
While Ivanti is but to launch patches for these two actively exploited zero-days, admins are suggested to use mitigation measures supplied by the seller on all ICS VPNs on their community.
They must also run Ivanti’s Integrity Checker Tool and think about all information on the ICS VPN equipment (together with passwords and any secrets and techniques) as compromised if indicators of a breach are discovered, as detailed within the ‘Responding to Compromise’ part of Volexity’s earlier weblog submit.
Threat monitoring service Shadowserver presently tracks greater than 16,800 ICS VPN home equipment uncovered on-line, nearly 5,000 within the United States (Shodan additionally sees over 15,000 Internet-exposed Ivanti ICS VPNs).
As Ivanti disclosed final week, attackers can run arbitrary instructions on all supported variations of ICS VPN and IPS home equipment when efficiently chaining the 2 zero days.
Attacks have now escalated from a restricted variety of clients impacted by assaults exploiting these vulnerabilities, with the suspected Chinese state-backed menace actor (tracked as UTA0178 or UNC5221) now being joined by a number of others.
As Mandiant additionally revealed on Friday, its safety consultants discovered 5 customized malware strains deployed on breached clients’ techniques with the tip purpose of dropping webshells, further malicious payloads, and stealing credentials.
The listing of instruments used within the assaults contains:
- Zipline Passive Backdoor: customized malware that may intercept community visitors, helps add/obtain operations, creates reverse shells, proxy servers, server tunneling
- Thinspool Dropper: customized shell script dropper that writes the Lightwire internet shell onto Ivanti CS, securing persistence
- Wirefire internet shell: customized Python-based internet shell supporting unauthenticated arbitrary command execution and payload dropping
- Lightwire internet shell: customized Perl internet shell embedded in a official file, enabling arbitrary command execution
- Warpwire harvester: customized JavaScript-based device for harvesting credentials at login, sending them to a command and management (C2) server
- PySoxy tunneler: facilitates community visitors tunneling for stealthiness
- BusyBox: multi-call binary combining many Unix utilities utilized in numerous system duties
- Thinspool utility (sessionserver.pl): used to remount the filesystem as ‘learn/write’ to allow malware deployment
The most notable is ZIPLINE, a passive backdoor that intercepts incoming community visitors and offers file switch, reverse shell, tunneling, and proxying capabilities.
Suspected Chinese hacking teams used one other ICS zero-day tracked as CVE-2021-22893 two years in the past to breach dozens of U.S. and European authorities, protection, and monetary organizations.
Last yr, beginning in April, two different zero-days (CVE-2023-35078 and CVE-2023-35081) in Ivanti’s Endpoint Manager Mobile (EPMM) had been tagged as actively exploited and later reported as being used to breach a number of Norwegian authorities organizations.
One month later, hackers began utilizing a 3rd zero-day flaw (CVE-2023-38035) in Ivanti’s Sentry software program to bypass API authentication on weak units in restricted and focused assaults.
[ad_2]
