[ad_1]
A monetary cybercrime group calling itself the Disneyland Team has been making liberal use of visually complicated phishing domains that spoof fashionable financial institution manufacturers utilizing Punycode, an Internet commonplace that permits net browsers to render domains with non-Latin alphabets like Cyrillic.
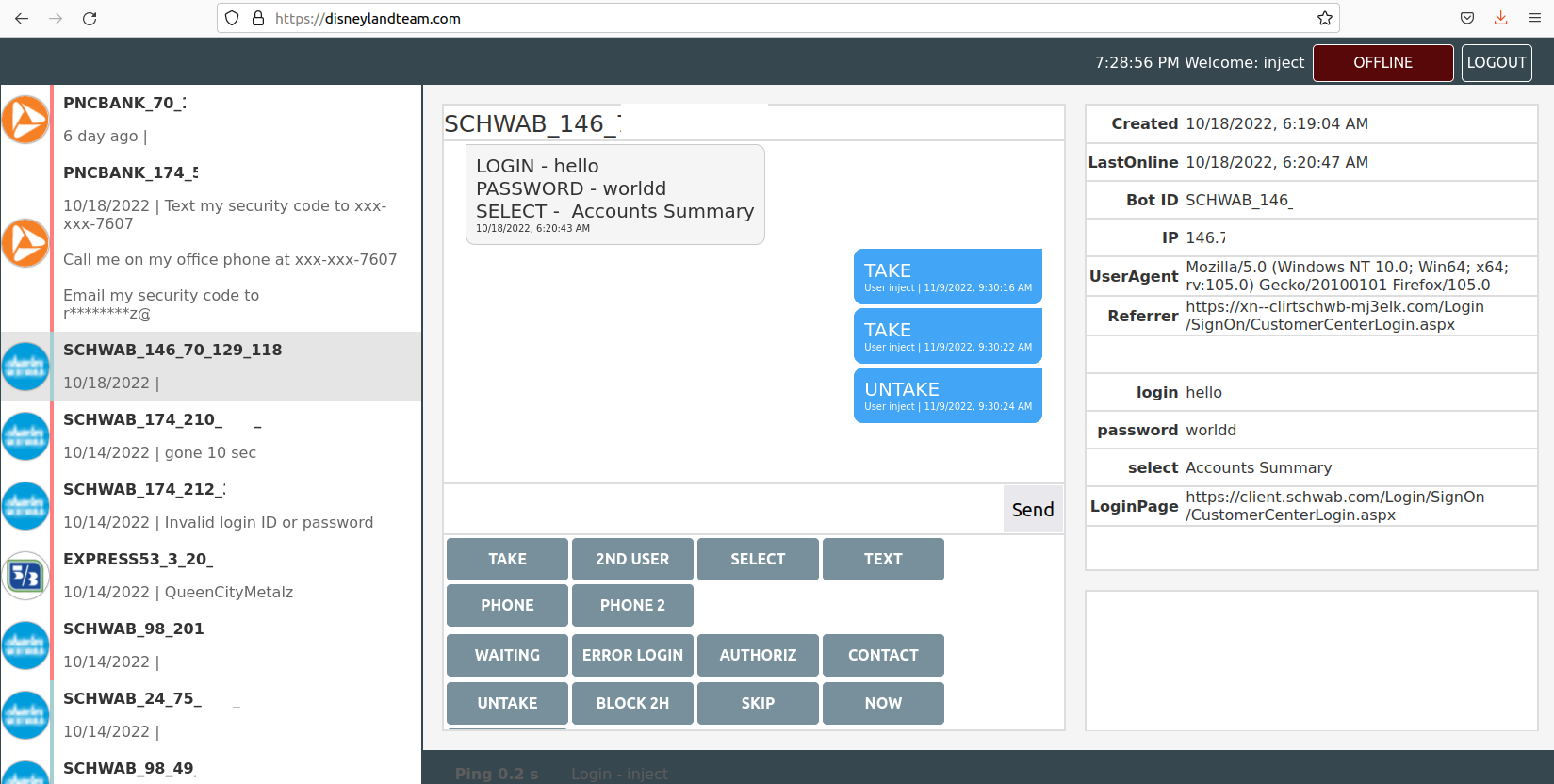
The Disneyland Team’s Web interface, which permits them to work together with malware victims in actual time to phish their login credentials utilizing phony financial institution web sites.
The Disneyland Team makes use of widespread misspellings for high financial institution manufacturers in its domains. For instance, one area the gang has used since March 2022 is ushank[.]com — which was created to phish U.S. Bank prospects.
But this group additionally often makes use of Punycode to make their phony financial institution domains look extra legit. The U.S. monetary companies agency Ameriprise makes use of the area ameriprise.com; the Disneyland Team’s area for Ameriprise prospects is https://www.xn--meripris-mx0doj[.]com [brackets added to defang the domain], which shows within the browser URL bar as ạmeriprisẹ[.]com.
Look fastidiously, and also you’ll discover small dots beneath the “a” and the second “e”. You may very well be forgiven in case you mistook one or each of these dots for a spec of mud in your laptop display screen or cell machine.
This candid view contained in the Disneyland Team comes from Alex Holden, founding father of the Milwaukee-based cybersecurity consulting agency Hold Security. Holden’s analysts gained entry to a Web-based management panel the crime group has been utilizing to maintain observe of sufferer credentials (see screenshot above). The panel reveals the gang has been working dozens of Punycode-based phishing domains for the higher a part of 2022.
Have a have a look at the Punycode on this Disneyland Team phishing area: https://login2.xn--mirtesnbd-276drj[.]com, which reveals up within the browser URL bar as login2.ẹmirạtesnbd[.]com, a site concentrating on customers of Emirates NBD Bank in Dubai.
Here’s one other area registered this 12 months by the Disneyland Team: https://xn--clientchwb-zxd5678f[.]com, which spoofs the login web page of economic advisor Charles Schwab with the touchdown web page of cliẹntșchwab[.]com. Again, discover the dots below the letters “e” and “s”. Another Punycode area of theirs sends would-be victims to cliẹrtschwạb[.]com, which mixes a model misspelling with Punycode.
We see the identical dynamic with the Disneyland Team Punycode area https://singlepoint.xn--bamk-pxb5435b[.]com, which interprets to singlepoint.ụșbamk[.]com — once more phishing U.S. Bank prospects.
What’s occurring right here? Holden says the Disneyland Team is Russian-speaking — if not additionally primarily based in Russia — however it isn’t a phishing gang per se. Rather, this group makes use of the phony financial institution domains at the side of malicious software program that’s already secretly put in on a sufferer’s laptop.
Holden stated the Disneyland Team domains have been made to assist the group steal cash from victims contaminated with a robust pressure of Microsoft Windows-based banking malware often known as Gozi 2.0/Ursnif. Gozi focuses on accumulating credentials, and is especially used for assaults on client-side on-line banking to facilitate fraudulent financial institution transfers. Gozi additionally permits the attackers to hook up with a financial institution’s web site utilizing the sufferer’s laptop.
In years previous, crooks like these would use custom-made “web injects” to control what Gozi victims see of their Web browser after they go to their financial institution’s website. These net injects allowed malware to rewrite the financial institution’s HTML code on the fly, and replica and/or intercept any knowledge customers would enter right into a web-based kind, corresponding to a username and password.
Most Web browser makers, nevertheless, have spent years including safety protections to dam such nefarious exercise. As a consequence, the Disneyland Team merely tries to make their domains look as very like the actual factor as attainable, after which funnel victims towards interacting with these imposter websites.
“The reason that it is infeasible for them to use in-browser injects include browser and OS protection measures, and difficulties manipulating dynamic pages for banks that require multi-factor authentication,” Holden stated.
In actuality, the pretend financial institution web site overlaid by the Disneyland Team’s malware relays the sufferer’s browser exercise by to the actual financial institution web site, whereas permitting the attackers to ahead any secondary login requests from the financial institution, corresponding to secret questions or multi-factor authentication challenges.
The Disneyland Team included directions for its customers, noting that when the sufferer enters their login credentials, he sees a 10-second spinning wheel, after which the message, “Awaiting back office approval for your request. Please don’t close this window.”
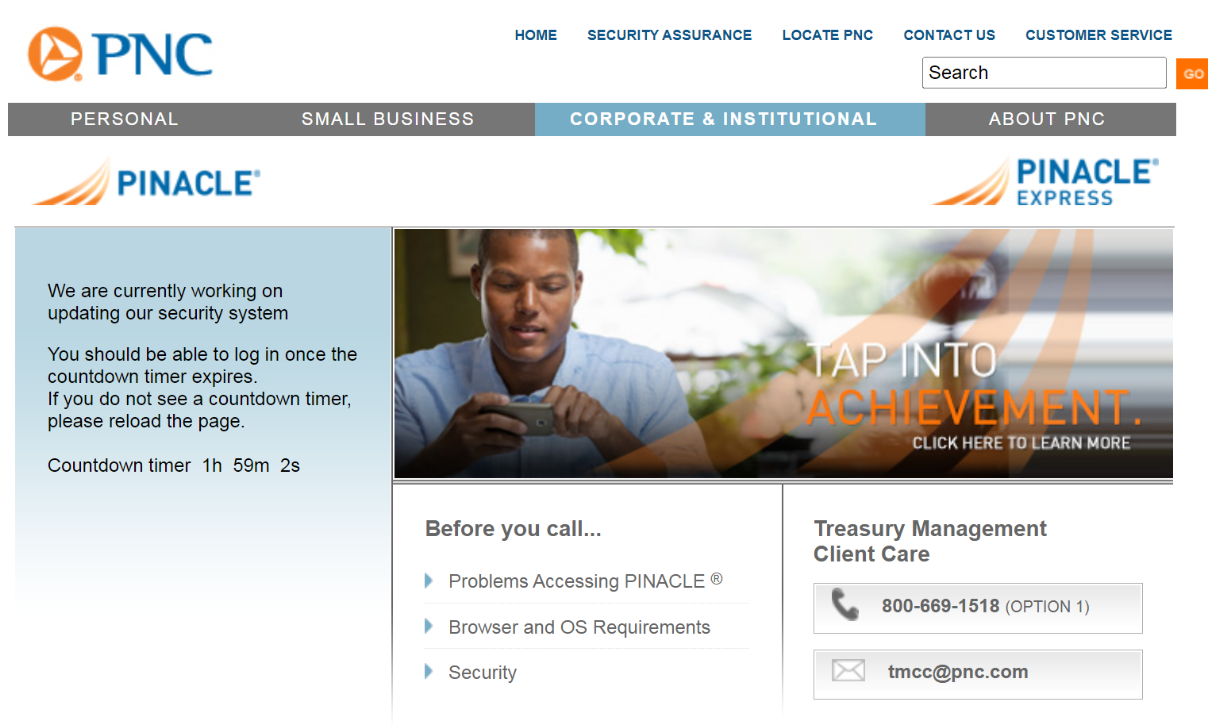
A pretend PNC web site overlay or “web inject” displaying a message meant to quickly forestall the person from accessing their account.
The “SKIP” button within the screenshot above sends the person to the actual financial institution login web page, “in case the account is not interesting to us,” the handbook explains. “Also, this redirect works if none of our operators are working at the time.”
The “TAKE” button within the Disneyland Team management panel permits customers or associates to assert possession over a particular contaminated machine or bot, which then excludes different customers from interacting with that sufferer.
In the occasion that it in some way takes a very long time to get the sufferer (bot) linked to the Disneyland Team management panel, or whether it is essential to delay a transaction, customers can push a button that prompts the next message to seem on the sufferer’s display screen:
“Your case ID number is 875472. An online banking support representative will get in touch shortly. Please provide your case ID number, and DO NOT close this page.”
The Disneyland person handbook explains that the panel can be utilized to pressure the sufferer to log in once more in the event that they transmit invalid credentials. It additionally has different choices for stalling victims while their accounts are drained. Another pretend immediate the panel can produce reveals the sufferer a message saying, “We are currently working on updating our security system. You should be able to log in once the countdown timer expires.”
The person handbook says this selection blocks the person from accessing their account for 2 hours. “It is possible to block for an hour with this button, in this case they get less frustrated, within the hours ddos will kill their network.”
Cybercrime teams will typically launch distributed denial-of-service (DDoS) assaults on the servers of the businesses they’re attempting to rob — which is often meant to distract victims from their fleecing, though Holden stated it’s unclear if the Disneyland Team employs this tactic as nicely.
For a few years, KrebsOnSecurity tracked the day-to-day actions of an identical malware crew that used net injects and bots to steal tens of tens of millions of {dollars} from small- to mid-sized companies throughout the United States.
At the top of every story, I’d shut with a advice that anybody involved about malware snarfing their banking data ought to strongly think about doing their on-line banking from a devoted, security-hardened system which is simply used for that goal. Of course, the devoted system method works provided that you at all times use that devoted system for managing your account on-line.
Those tales additionally noticed that for the reason that overwhelming majority of the malicious software program utilized in cyberheists is designed to run solely on Microsoft Windows computer systems, it made sense to choose a non-Windows laptop for that devoted banking system, corresponding to a Mac or perhaps a model of Linux. I nonetheless stand by this recommendation.
In case anybody is , right here (PDF) is an inventory of all phishing domains at present and beforehand utilized by the Disneyland Team.
[ad_2]
