[ad_1]
An Iranian superior persistent menace (APT) actor referred to as Agrius has been attributed as behind a set of knowledge wiper assaults geared toward diamond industries in South Africa, Israel, and Hong Kong.
The wiper, known as Fantasy by ESET, is believed to have been delivered through a supply-chain assault concentrating on an Israeli software program suite developer as a part of a marketing campaign that started in February 2022.
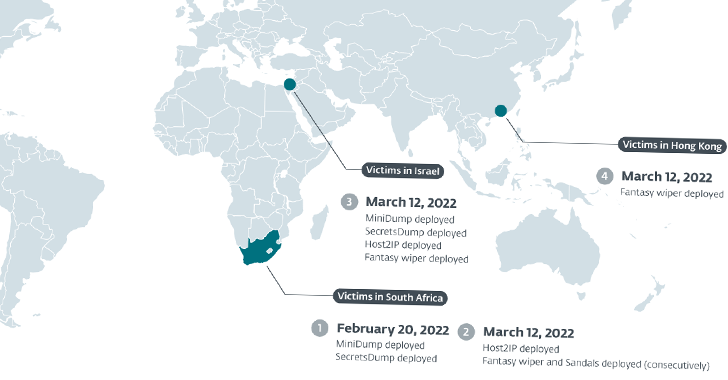
Victims embody HR corporations, IT consulting corporations, and a diamond wholesaler in Israel; a South African entity working within the diamond trade; and a jeweler based mostly in Hong Kong.
“The Fantasy wiper is constructed on the foundations of the beforehand reported Apostle wiper however doesn’t try to masquerade as ransomware, as Apostle initially did, ESET researcher Adam Burgher disclosed in a Wednesday evaluation. “Instead, it goes proper to work wiping information.”
Apostle was first documented by SentinelOne in May 2021 as a wiper-turned-ransomware that was deployed in harmful assaults in opposition to Israeli targets.
Agrius, the Iran-aligned group behind the intrusions, has been energetic since no less than December 2020 and leverages recognized safety flaws in internet-facing functions to drop net shells which are, in flip, used to facilitate reconnaissance, lateral motion, and the supply of final-stage payloads.
The Slovak cybersecurity firm mentioned the primary assault was detected on February 20, 2022, when the actor deployed credential harvesting instruments within the IT community of the South African group.
Agrius subsequently initiated the wiping assault through Fantasy on March 12, 2022, earlier than putting different corporations in Israel and Hong Kong on the identical date.
Fantasy is executed by the use of one other device known as Sandals, a 32-bit Windows executable written in C#/.NET. It’s mentioned to be deployed on the compromised host by a supply-chain assault utilizing the Israeli developer’s software program replace mechanism.
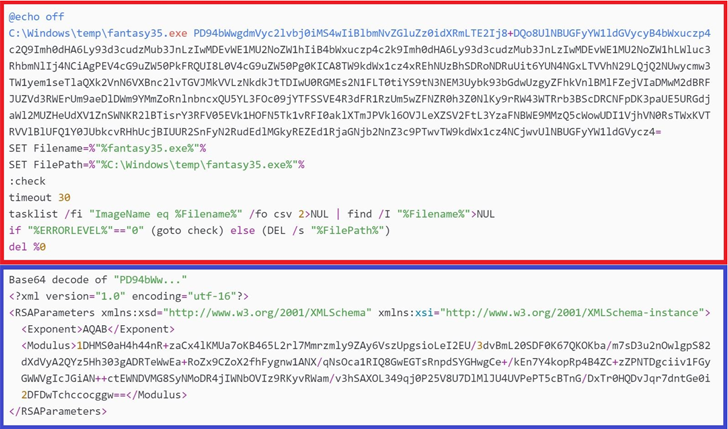
This is substantiated by ESET’s evaluation that every one victims are prospects of the affected software program developer and that the wiper binary follows a naming conference (“fantasy45.exe” and “fantasy35.exe”) just like that of its respectable counterpart.
The wiper, for its half, works by recursively retrieving the listing itemizing for every drive, overwriting each file in these directories with rubbish information, assigning a future timestamp to the information, after which deleting them.
“This is presumably completed to make restoration and forensic evaluation harder,” Burgher defined.
In an extra try to erase all traces of the exercise, Fantasy clears all Windows occasion logs, recursively purges all information within the system drive, overwrites the system’s Master Boot Record, self-deletes itself, and eventually reboots the machine.
The marketing campaign, which lasted not more than three hours, was finally unsuccessful, with ESET stating that it was in a position to block the wiper’s execution. The developer of the software program has since pushed out clear updates to plug the assaults.
The title of the Israeli firm that fell sufferer to the supply-chain assault was not disclosed by ESET, however proof factors to it being Rubinstein Software, which markets an enterprise useful resource planning (ERP) resolution known as Fantasy that is used for jewellery inventory administration.
“Since its discovery in 2021, Agrius has been solely centered on harmful operations,” Burgher concluded.
“To that finish, Agrius operators in all probability executed a supply-chain assault by concentrating on an Israeli software program firm’s software program updating mechanisms to deploy Fantasy, its latest wiper, to victims in Israel, Hong Kong, and South Africa.”
Agrius is way from the primary menace group linked to Iran that has been noticed deploying harmful wiper malware.
The APT33 hacking group (aka Elfin, Holmium, or Refined Kitten), which is suspected of working on the behest of the Iranian authorities, is claimed to have been behind a number of assaults that used the Shamoon wiper in opposition to targets positioned within the Middle East.
Data-wiping malware codenamed ZeroCleare has additionally been employed by Iran-backed menace actors tracked as APT34 (aka OilRig or Helix Kitten) in assaults directed in opposition to organizations from the power and industrial sector within the Middle East.
[ad_2]