[ad_1]
Raccoon Stealer is again on the information once more. US officers arrested Mark Sokolovsky, one of many malware actors behind this program. In July 2022, after a number of months of the shutdown, a Raccoon Stealer V2 went viral. Last week, the Department of Justice’s press launch said that the malware collected 50 million credentials.
This article will give a fast information to the newest information stealer’s model.
What is Raccoon infostealer V2?
Raccoon Stealer is a sort of malware that steals numerous knowledge from an contaminated pc. It’s fairly a fundamental malware, however hackers have made Raccoon well-liked with glorious service and easy navigation.
In 2019, Raccoon infostealer was some of the mentioned malware. In trade for $75 per week and $200 per thirty days, cybercriminals bought this straightforward however versatile information stealer as a MaaS. The malware was profitable in attacking plenty of programs. In March 2022, nonetheless, menace authors ceased to function.
An up to date model of this malware was launched in July 2022. As a outcome, Raccoon Stealer V2 has gone viral and gained a brand new identify – RecordBreaker.
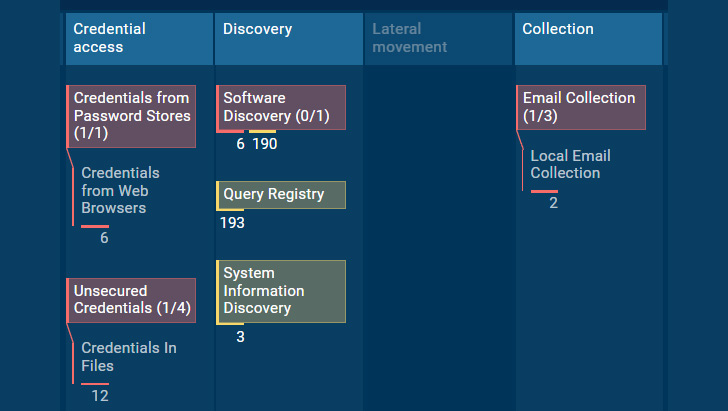 |
| Raccoon v2’s techniques & methods in ANY.RUN Sandbox |
How to investigate Raccoon stealer V2
|
Execution course of |
What Raccoon malware does |
|
Downloads WinAPI libraries |
Uses kernel32.dll!LoadLibraryW |
|
Gets WinAPI capabilities’ addresses |
Uses kernel32.dll!GetProcAddress |
|
Strings and C2 servers encryption |
Encrypts with RC4 or XOR algorithm, might be no encryption in any respect, or mixture of various possibility |
|
Crash triggers |
CIS nations locale, mutex |
|
System/NativeSystem stage privilege verify |
Uses Advapi32.dll!GetTokenInformation and Advapi32.dll!ConvertSidToStringSidW evaluating StringSid with L “S-1-5-18” |
|
Process enumeration |
Uses the TlHelp32 API (kernel32.dll!CreateToolhelp32Snapshot to seize processes and kernel32.dll!Process32First / kernel32.dll!Process32Next). |
|
Connecting to C2 servers |
Creates a string: Then sends a POST request |
|
User and system knowledge assortment |
|
|
Sending of collected knowledge |
POST requests to C2. |
|
Getting a solution from the C2 |
C2 sends “acquired” |
|
Finishing operations |
Takes a screenshot(s), releases the remaining allotted assets, unloads the libraries, and finishes its work |
We have triaged a number of Raccoon stealer V2 samples, collected typical conduct actions, and briefly described its execution course of.
Read deeper and extra detailed Raccoon stealer 2.0 malware evaluation. In the article, you possibly can observe all steps and get a whole image of the data stealer’s conduct. Besides this profound analysis, you get an opportunity to extract malware configuration by yourselves – copy the Python script of Raccoon stealer and unpack reminiscence dumps to extract C&C servers and keys.
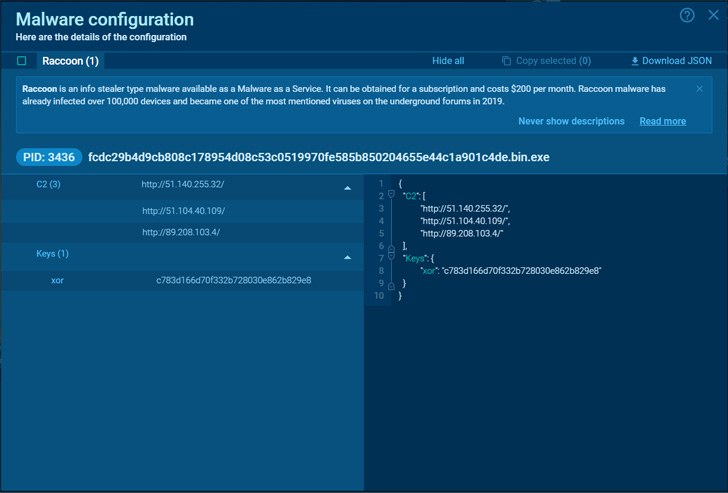 |
| Raccoon v2 malware configuration |
Where to investigate malware
Do you wish to analyze malicious information and hyperlinks? There is a quick and straightforward answer: get ready-made configurations in ANY.RUN on-line malware sandbox and examine suspicious information inside and outside. Try to crack any malware utilizing an interactive strategy:
Write the “HACKERNEWS” promo code at help@any.run utilizing what you are promoting e-mail handle and get 14 days of ANY.RUN premium subscription free of charge!
The ANY.RUN sandbox helps you to analyze malware shortly, navigate by the analysis course of simply, detect even subtle malware, and get detailed experiences. Use good instruments and hunt malware efficiently.
[ad_2]