[ad_1]
Late final 12 months, safety researchers made a startling discovery: Kremlin-backed disinformation campaigns have been bypassing moderation on social media platforms by leveraging the identical malicious promoting know-how that powers a sprawling ecosystem of on-line hucksters and web site hackers. A brand new report on the fallout from that investigation finds this darkish advert tech business is much extra resilient and incestuous than beforehand identified.

Image: Infoblox.
In November 2024, researchers on the safety agency Qurium revealed an investigation into “Doppelganger,” a disinformation community that promotes pro-Russian narratives and infiltrates Europe’s media panorama by pushing faux information by a community of cloned web sites.
Doppelganger campaigns use specialised hyperlinks that bounce the customer’s browser by an extended sequence of domains earlier than the faux information content material is served. Qurium discovered Doppelganger depends on a classy “domain cloaking” service, a know-how that enables web sites to current completely different content material to serps in comparison with what common guests see. The use of cloaking companies helps the disinformation websites stay on-line longer than they in any other case would, whereas guaranteeing that solely the focused viewers will get to view the supposed content material.
Qurium found that Doppelganger’s cloaking service additionally promoted on-line relationship websites, and shared a lot of the identical infrastructure with VexTrio, which is considered the oldest malicious site visitors distribution system (TDS) in existence. While TDSs are generally utilized by professional promoting networks to handle site visitors from disparate sources and to trace who or what’s behind every click on, VexTrio’s TDS largely manages net site visitors from victims of phishing, malware, and social engineering scams.
BREAKING BAD
Digging deeper, Qurium seen Doppelganger’s cloaking service used an Internet supplier in Switzerland as the primary entry level in a sequence of area redirections. They additionally seen the identical infrastructure hosted a pair of co-branded affiliate internet marketing companies that have been driving site visitors to sketchy grownup relationship websites: LosPollos[.]com and TacoLoco[.]co.
The LosPollos advert community incorporates many parts and references from the hit sequence “Breaking Bad,” mirroring the fictional “Los Pollos Hermanos” restaurant chain that served as a cash laundering operation for a violent methamphetamine cartel.

The LosPollos promoting community invokes characters and themes from the hit present Breaking Bad. The brand for LosPollos (higher left) is the picture of Gustavo Fring, the fictional rooster restaurant chain proprietor within the present.
Affiliates who enroll with LosPollos are given JavaScript-heavy “smartlinks” that drive site visitors into the VexTrio TDS, which in flip distributes the site visitors amongst a wide range of promoting companions, together with relationship companies, sweepstakes gives, bait-and-switch cellular apps, monetary scams and malware obtain websites.
LosPollos associates usually sew these sensible hyperlinks into WordPress web sites which were hacked by way of identified vulnerabilities, and people associates will earn a small fee every time an Internet consumer referred by any of their hacked websites falls for certainly one of these lures.
The Los Pollos promoting community selling itself on LinkedIn.
According to Qurium, TacoLoco is a site visitors monetization community that makes use of misleading ways to trick Internet customers into enabling “push notifications,” a cross-platform browser normal that enables web sites to point out pop-up messages which seem exterior of the browser. For instance, on Microsoft Windows methods these notifications usually present up within the backside proper nook of the display screen — simply above the system clock.
In the case of VexTrio and TacoLoco, the notification approval requests themselves are misleading — disguised as “CAPTCHA” challenges designed to differentiate automated bot site visitors from actual guests. For years, VexTrio and its companions have efficiently tricked numerous customers into enabling these web site notifications, that are then used to constantly pepper the sufferer’s system with a wide range of phony virus alerts and deceptive pop-up messages.
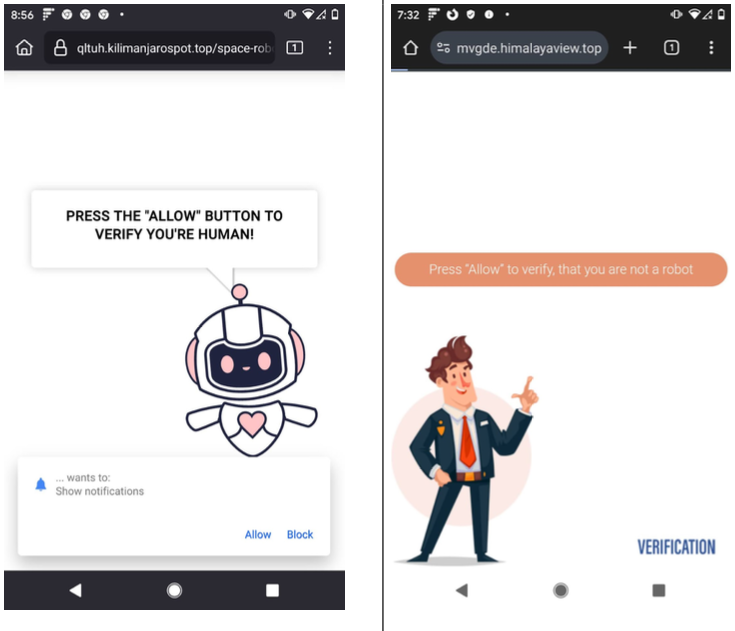
Examples of VexTrio touchdown pages that lead customers to just accept push notifications on their system.
According to a December 2024 annual report from GoDaddy, practically 40 % of compromised web sites in 2024 redirected guests to VexTrio by way of LosPollos smartlinks.
ADSPRO AND TEKNOLOGY
On November 14, 2024, Qurium revealed analysis to assist its findings that LosPollos and TacoLoco have been companies operated by Adspro Group, an organization registered within the Czech Republic and Russia, and that Adspro runs its infrastructure on the Swiss internet hosting suppliers C41 and Teknology SA.
Qurium famous the LosPollos and TacoLoco websites state that their content material is copyrighted by ByteCore AG and SkyForge Digital AG, each Swiss corporations which might be run by the proprietor of Teknology SA, Giulio Vitorrio Leonardo Cerutti. Further investigation revealed LosPollos and TacoLoco have been apps developed by an organization known as Holacode, which lists Cerutti as its CEO.
The apps marketed by Holacode embrace quite a few VPN companies, in addition to one known as Spamshield that claims to cease undesirable push notifications. But in January, Infoblox stated they examined the app on their very own cellular gadgets, and located it hides the consumer’s notifications, after which after 24 hours stops hiding them and calls for cost. Spamshield subsequently modified its developer identify from Holacode to ApLabz, though Infoblox famous that the Terms of Service for a number of of the rebranded ApLabz apps nonetheless referenced Holacode of their phrases of service.
Incredibly, Cerutti threatened to sue me for defamation earlier than I’d even uttered his identify or despatched him a request for remark (Cerutti despatched the unsolicited authorized risk again in January after his firm and my identify have been merely tagged in an Infoblox submit on LinkedIn about VexTrio).
Asked to touch upon the findings by Qurium and Infoblox, Cerutti vehemently denied being related to VexTrio. Cerutti asserted that his corporations all strictly adhere to the rules of the international locations by which they function, and that they’ve been utterly clear about all of their operations.
“We are a group operating in the advertising and marketing space, with an affiliate network program,” Cerutti responded. “I am not [going] to say we are perfect, but I strongly declare we have no connection with VexTrio at all.”
“Unfortunately, as a big player in this space we also get to deal with plenty of publisher fraud, sketchy traffic, fake clicks, bots, hacked, listed and resold publisher accounts, etc, etc.,” Cerutti continued. “We bleed lots of money to such malpractices and conduct regular internal screenings and audits in a constant battle to remove bad traffic sources. It is also a highly competitive space, where some upstarts will often play dirty against more established mainstream players like us.”
Working with Qurium, researchers on the safety agency Infoblox launched particulars about VexTrio’s infrastructure to their business companions. Just 4 days after Qurium revealed its findings, LosPollos introduced it was suspending its push monetization service. Less than a month later, Adspro had rebranded to Aimed Global.
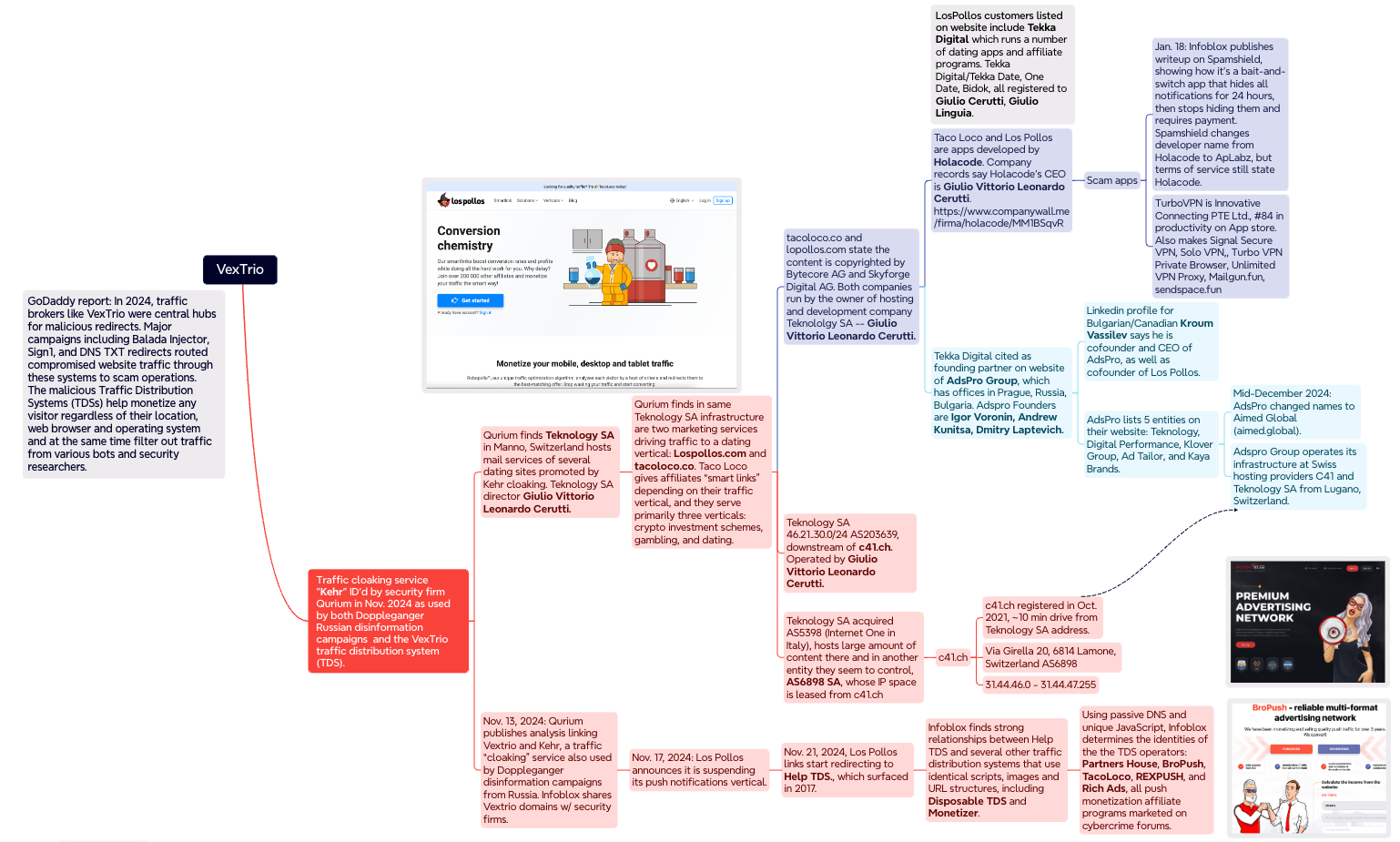
A thoughts map illustrating a number of the key findings and connections within the Infoblox and Qurium investigations. Click to enlarge.
A REVEALING PIVOT
In March 2025, researchers at GoDaddy chronicled how DollyWay — a malware pressure that has persistently redirected victims to VexTrio all through its eight years of exercise — immediately stopped doing that on November 20, 2024. Virtually in a single day, DollyWay and several other different malware households that had beforehand used VexTrio started pushing their site visitors by one other TDS known as Help TDS.
Digging additional into historic DNS information and the distinctive code scripts utilized by the Help TDS, Infoblox decided it has lengthy loved an unique relationship with VexTrio (a minimum of till LosPollos ended its push monetization service in November).
In a report launched right now, Infoblox stated an exhaustive evaluation of the JavaScript code, web site lures, smartlinks and DNS patterns utilized by VexTrio and Help TDS linked them with a minimum of 4 different TDS operators (not counting TacoLoco). Those 4 entities — Partners House, BroPush, RichAds and RexPush — are all Russia-based push monetization packages that pay associates to drive signups for a wide range of schemes, however principally on-line relationship companies.
“As Los Pollos push monetization ended, we’ve seen an increase in fake CAPTCHAs that drive user acceptance of push notifications, particularly from Partners House,” the Infoblox report reads. “The relationship of these commercial entities remains a mystery; while they are certainly long-time partners redirecting traffic to one another, and they all have a Russian nexus, there is no overt common ownership.”
Renee Burton, vice chairman of risk intelligence at Infoblox, stated the safety business usually treats the misleading strategies utilized by VexTrio and different malicious TDSs as a sort of legally gray space that’s principally related to much less harmful safety threats, comparable to adware and scareware.
But Burton argues that this view is myopic, and helps perpetuate a darkish adtech business that additionally pushes loads of straight-up malware, noting that tons of of hundreds of compromised web sites around the globe yearly redirect victims to the tangled net of VexTrio and VexTrio-affiliate TDSs.
“These TDSs are a nefarious threat, because they’re the ones you can connect to the delivery of things like information stealers and scams that cost consumers billions of dollars a year,” Burton stated. “From a larger strategic perspective, my takeaway is that Russian organized crime has control of malicious adtech, and these are just some of the many groups involved.”
WHAT CAN YOU DO?
As KrebsOnSecurity warned means again in 2020, it’s a good suggestion to be very sparing in approving notifications when shopping the Web. In many circumstances these notifications are benign, however as we’ve seen there are quite a few dodgy corporations which might be paying web site house owners to put in their notification scripts, after which reselling that communications pathway to scammers and on-line hucksters.
If you’d like to stop websites from ever presenting notification requests, all the main browser makers allow you to do that — both throughout the board or on a per-website foundation. While it’s true that blocking notifications totally can break the performance of some web sites, doing this for any gadgets you handle on behalf of your much less tech-savvy pals or relations may find yourself saving everybody lots of headache down the street.
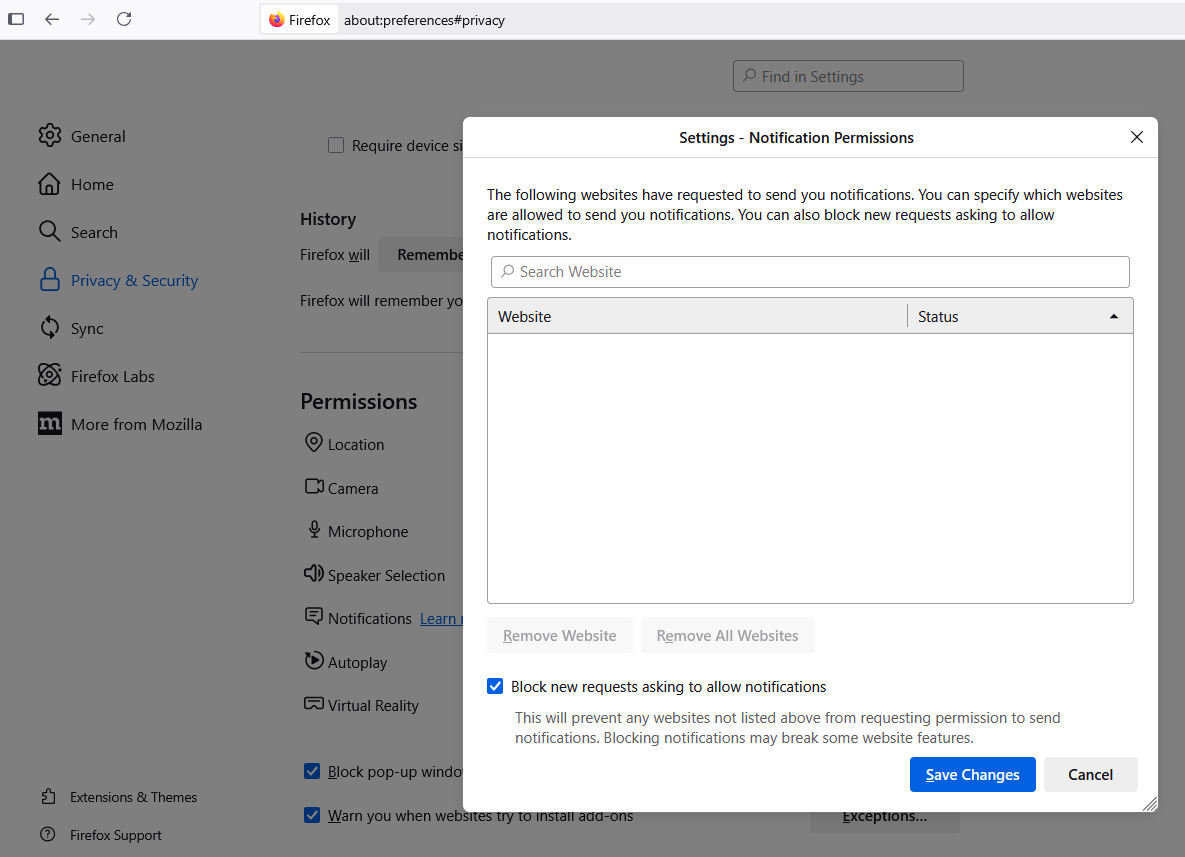
To modify web site notification settings in Mozilla Firefox, navigate to Settings, Privacy & Security, Permissions, and click on the “Settings” tab subsequent to “Notifications.” That web page will show any notifications already permitted and let you edit or delete any entries. Tick the field subsequent to “Block new requests asking to allow notifications” to cease them altogether.
In Google Chrome, click on the icon with the three dots to the precise of the deal with bar, scroll all the best way right down to Settings, Privacy and Security, Site Settings, and Notifications. Select the “Don’t allow sites to send notifications” button if you wish to banish notification requests endlessly.
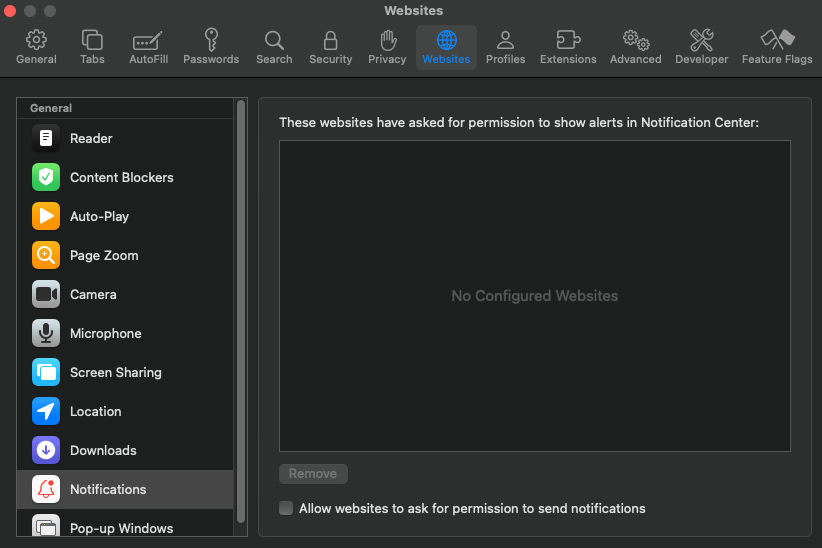
In Apple’s Safari browser, go to Settings, Websites, and click on on Notifications within the sidebar. Uncheck the choice to “allow websites to ask for permission to send notifications” in case you want to flip off notification requests totally.
[ad_2]
