[ad_1]
Microsoft on Tuesday launched 135 patches affecting 19 product households. Ten of the addressed points, all distant code execution points, are thought of by Microsoft to be of Critical severity, and 18 have a CVSS base rating of 8.0 or greater. One, an Important-severity elevation of privilege subject touching the Windows Common Log File system driver, is thought to be underneath energetic exploit within the wild.
At patch time, 11 further CVEs usually tend to be exploited within the subsequent 30 days by the corporate’s estimation. Various of this month’s points are amenable to direct detection by Sophos protections, and we embrace info on these in a desk under.
In addition to those patches, sixteen Important-severity Adobe Reader points affecting ColdFusion are lined within the launch. Those are listed in Appendix D under. In a departure from typical process, we’re together with all Edge CVEs in our numbers this month the place doable, although these patches have been for essentially the most half made accessible individually from in the present day’s launch.
We are as all the time together with on the finish of this submit further appendices itemizing all Microsoft’s patches sorted by severity, by predicted exploitability timeline and CVSS Base rating, and by product household; an appendix overlaying the advisory-style updates; and a breakout of the patches affecting the assorted Windows Server platforms nonetheless in assist.
By the numbers
- Total CVEs: 135
- Publicly disclosed: 0
- Exploit detected: 1
- Severity
- Critical: 10
- Important: 114
- Low: 2
- High / Medium / Low: 9 (Edge-related CVEs issued by Chromium; see Appendix C)
- Impact
- Elevation of Privilege: 48
- Remote Code Execution: 33
- Information Disclosure: 18
- Denial of Service: 14
- Security Feature Bypass: 9
- Spoofing: 4
- Unknown: 9 (Edge-related CVEs issued by Chromium; see Appendix C)
- CVSS rating 9.0 or higher: 0
- CVSS base rating 8.0 or higher: 18
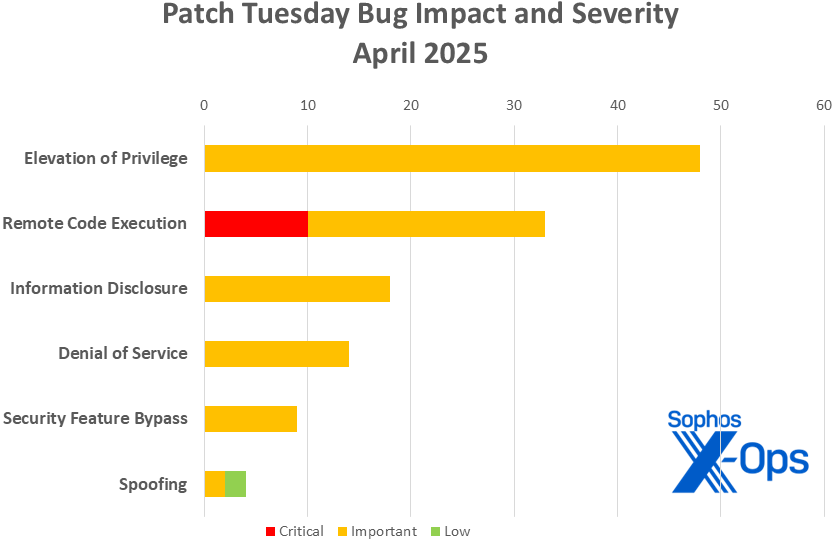
Figure 1: Elevation of privilege accounts for over a 3rd of all April patches, however all of the Critical-severity gadgets are distant code execution. (Please be aware that 9 of the Edge updates lined on this subject aren’t launched with full affect info and observe a special severity schema, and thus don’t seem on this chart; please see Appendix C)
Products
- Windows: 89
- 365: 15
- Office: 15
- Edge: 13
- SharePoint: 6
- Visual Studio: 5
- Azure: 4
- Excel: 3
- Microsoft AutoUpdate (MAU) for Mac: 2
- Word: 2
- Access: 1
- ASP.NET: 1
- Dynamics 365: 1
- OneObserve: 1
- Outlook for Android: 1
- Power Automate for Desktop: 1
- SQL Server: 1
- System Center: 1
- Visual Studio Tools for Applications (VSTA): 1
As is our customized for this listing, CVEs that apply to multiple product household are counted as soon as for every household they have an effect on. It must be famous that CVE names in April don’t all the time replicate affected product households carefully. In specific, some CVEs names within the Office household could point out merchandise that don’t seem within the listing of merchandise affected by the CVE, and vice versa.
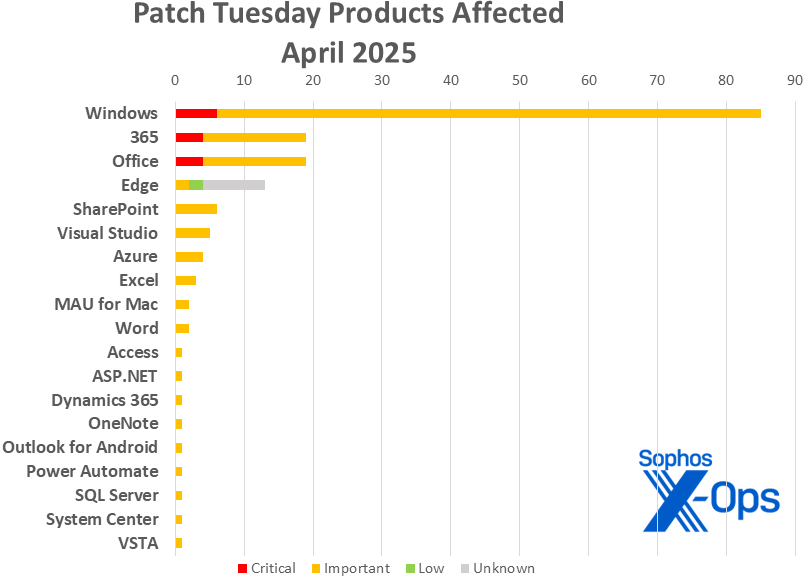
Figure 2: Nineteen product households are affected by April’s patches; as famous above, 9 of the Edge updates lined on this subject aren’t launched with full affect info and observe a special severity schema, and thus seem right here as “unknown” in affect; please see Appendix C
Notable April updates
In addition to the problems mentioned above, a wide range of particular gadgets advantage consideration.
CVE-2025-26642, CVE-2025-27745, CVE-2025-27747, CVE-2025-27748, CVE-2025-27749, CVE-2025-27750, CVE-2025-27751, CVE-2025-2772, CVE-2025-29791, CVE-2025-29816, CVE-2025-29820, CVE-2025-29822 (12 CVEs) – assorted Office points
Office takes a heavy patch load this month, and the information is especially not good for customers of Office LTSC for Mac 2021 and 2024. All twelve CVEs listed above are relevant to these variations, however the replace isn’t prepared but; affected events are suggested to watch these CVEs for replace availability. Worse, 5 of the twelve (CVE-2025-27745, CVE-2025-27748, CVE-2025-27749, CVE-2025-27752, CVE-2025-29791) embrace the Preview Pane as a vector, elevating 4 of them from Important to Critical severity.
CVE-2025-26647 — Windows Kerberos Elevation of Privilege Vulnerability
An Important-severity elevation of privilege subject, this one seems to hinge on the attacker’s capacity to compromise a trusted CA (Certificate Authority). If the attacker can accomplish that after which subject a certificates with a selected Subject Key Identifier (SKI) worth, they might then use that certificates to connect with the system, in the end assuming the id of any account. This one comes with beneficial mitigations, together with updating of all Windows machines and area controllers to the patch launched in the present day, monitoring audit occasions to identify any machine or gadget that escapes that replace, and enabling Enforcement Mode as soon as your atmosphere not makes use of certificates issued by authorities not within the NTAuth retailer. CA compromise is after all a longstanding drawback within the ecosystem; with this CVE marked by Microsoft as extra more likely to be exploited inside the subsequent 30 days, it’s value prioritizing in your property.
CVE-2025-27743 — Microsoft System Center Elevation of Privilege Vulnerability
An Important-severity elevation-of-privilege subject, this CVE touches a constellation of System Center merchandise (Operations Manager, Service Manager, Orchestrator, Data Protection Manager, Virtual Machine Manager) and impacts prospects who re-use present System Center .exe installer recordsdata to deploy new cases of their environments. The drawback stems from an untrusted search path in System Center, which an attacker may, with approved entry and a few facility with DLL hijacking, use to raise their privileges. Microsoft advises affected customers to delete their present installer setup recordsdata (.exe) after which obtain the most recent model of their System Center product (.ZIP).
CVE-2025-29809 — Windows Kerberos Security Feature Bypass Vulnerability
Another subject doubtlessly requiring additional care from directors, this Important-severity safety characteristic bypass requires rollback of a earlier coverage. To quote Microsoft’s steering, “The policy described in Guidance for blocking rollback of Virtualization-based Security (VBS) related security updates has been updated to account for the latest changes. If you deployed this policy, then you’ll need to redeploy using the updated policy.”
Also, for any readers who missed the announcement, opposite to earlier plans Microsoft will not be deprecating driver replace synchronization by way of WSUS (Windows Server Update Services) simply but. Those nonetheless counting on the service to try this work (notably for “disconnected” gadgets) have a reprieve for now, however ought to proceed planning to maneuver to the cloud-based companies Microsoft now prioritizes.
Figure 3: As distant code execution did final month, elevation of privilege points handed the 100-CVE mark with this month’s Patch Tuesday launch
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2025-27482 | Exp/2527482-A | Exp/2527482-A |
| CVE-2025-29792 | Exp/2529792-A | Exp/2529792-A |
| CVE-2025-29812 | Exp/2529812-A | Exp/2529812-A |
| CVE-2025-29812 | Exp/2529812-A | Exp/2529812-A |
As you’ll be able to each month, for those who don’t wish to wait in your system to drag down Microsoft’s updates itself, you’ll be able to obtain them manually from the Windows Update Catalog web site. Run the winver.exe software to find out which construct of Windows 10 or 11 you’re working, then obtain the Cumulative Update bundle in your particular system’s structure and construct quantity.
Appendix A: Vulnerability Impact and Severity
This is an inventory of April patches sorted by affect, then sub-sorted by severity. Each listing is additional organized by CVE.
Elevation of Privilege (48 CVEs)
| Important severity | |
| CVE-2025-20570 | Visual Studio Code Elevation of Privilege Vulnerability |
| CVE-2025-21191 | Windows Local Security Authority (LSA) Elevation of Privilege Vulnerability |
| CVE-2025-21204 | Windows Process Activation Elevation of Privilege Vulnerability |
| CVE-2025-24058 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-24060 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-24062 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-24073 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-24074 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-26639 | Windows USB Print Driver Elevation of Privilege Vulnerability |
| CVE-2025-26640 | Windows Digital Media Elevation of Privilege Vulnerability |
| CVE-2025-26648 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2025-26649 | Windows Secure Channel Elevation of Privilege Vulnerability |
| CVE-2025-26665 | Windows upnphost.dll Elevation of Privilege Vulnerability |
| CVE-2025-26675 | Windows Subsystem for Linux Elevation of Privilege Vulnerability |
| CVE-2025-26679 | RPC Endpoint Mapper Service Elevation of Privilege Vulnerability |
| CVE-2025-26681 | Win32k Elevation of Privilege Vulnerability |
| CVE-2025-26687 | Win32k Elevation of Privilege Vulnerability |
| CVE-2025-26688 | Microsoft Virtual Hard Disk Elevation of Privilege Vulnerability |
| CVE-2025-27467 | Windows Digital Media Elevation of Privilege Vulnerability |
| CVE-2025-27475 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2025-27476 | Windows Digital Media Elevation of Privilege Vulnerability |
| CVE-2025-27478 | Windows Local Security Authority (LSA) Elevation of Privilege Vulnerability |
| CVE-2025-27483 | NTFS Elevation of Privilege Vulnerability |
| CVE-2025-27484 | Windows Universal Plug and Play (UPnP) Device Host Elevation of Privilege Vulnerability |
| CVE-2025-27489 | Azure Local Elevation of Privilege Vulnerability |
| CVE-2025-27490 | Windows Bluetooth Service Elevation of Privilege Vulnerability |
| CVE-2025-27492 | Windows Secure Channel Elevation of Privilege Vulnerability |
| CVE-2025-27727 | Windows Installer Elevation of Privilege Vulnerability |
| CVE-2025-27728 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2025-27730 | Windows Digital Media Elevation of Privilege Vulnerability |
| CVE-2025-27731 | Microsoft OpenSSH for Windows Elevation of Privilege Vulnerability |
| CVE-2025-27732 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2025-27733 | NTFS Elevation of Privilege Vulnerability |
| CVE-2025-27739 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2025-27740 | Active Directory Certificate Services Elevation of Privilege Vulnerability |
| CVE-2025-27741 | NTFS Elevation of Privilege Vulnerability |
| CVE-2025-27743 | Microsoft System Center Elevation of Privilege Vulnerability |
| CVE-2025-27744 | Microsoft Office Elevation of Privilege Vulnerability |
| CVE-2025-29792 | Microsoft Office Elevation of Privilege Vulnerability |
| CVE-2025-29800 | Microsoft AutoUpdate (MAU) Elevation of Privilege Vulnerability |
| CVE-2025-29801 | Microsoft AutoUpdate (MAU) Elevation of Privilege Vulnerability |
| CVE-2025-29802 | Visual Studio Elevation of Privilege Vulnerability |
| CVE-2025-29803 | Visual Studio Tools for Applications and SQL Server Management Studio Elevation of Privilege Vulnerability |
| CVE-2025-29804 | Visual Studio Elevation of Privilege Vulnerability |
| CVE-2025-29810 | Active Directory Domain Services Elevation of Privilege Vulnerability |
| CVE-2025-29811 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2025-29812 | DirectX Graphics Kernel Elevation of Privilege Vulnerability |
| CVE-2025-29824 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
Remote Code Execution (33 CVEs)
| Critical severity | |
| CVE-2025-26663 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
| CVE-2025-26670 | Lightweight Directory Access Protocol (LDAP) Client Remote Code Execution Vulnerability |
| CVE-2025-26686 | Windows TCP/IP Remote Code Execution Vulnerability |
| CVE-2025-27480 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2025-27482 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2025-27491 | Windows Hyper-V Remote Code Execution Vulnerability |
| CVE-2025-27745 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27748 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27749 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27752 | Microsoft Excel Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2025-21205 | Windows Telephony Service Remote Code Execution Vulnerability |
| CVE-2025-21221 | Windows Telephony Service Remote Code Execution Vulnerability |
| CVE-2025-21222 | Windows Telephony Service Remote Code Execution Vulnerability |
| CVE-2025-25000 | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability |
| CVE-2025-26642 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-26666 | Windows Media Remote Code Execution Vulnerability |
| CVE-2025-26668 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2025-26671 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2025-26674 | Windows Media Remote Code Execution Vulnerability |
| CVE-2025-27477 | Windows Telephony Service Remote Code Execution Vulnerability |
| CVE-2025-27481 | Windows Telephony Service Remote Code Execution Vulnerability |
| CVE-2025-27487 | Remote Desktop Client Remote Code Execution Vulnerability |
| CVE-2025-27729 | Windows Shell Remote Code Execution Vulnerability |
| CVE-2025-27746 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27747 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-27750 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-27751 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-29791 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-29793 | Microsoft SharePoint Remote Code Execution Vulnerability |
| CVE-2025-29794 | Microsoft SharePoint Remote Code Execution Vulnerability |
| CVE-2025-29815 | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability |
| CVE-2025-29820 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-29823 | Microsoft Excel Remote Code Execution Vulnerability |
Information Disclosure (18 CVEs)
| Important severity | |
| CVE-2025-21197 | Windows NTFS Information Disclosure Vulnerability |
| CVE-2025-21203 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-25002 | Azure Local Cluster Information Disclosure Vulnerability |
| CVE-2025-26628 | Azure Local Cluster Information Disclosure Vulnerability |
| CVE-2025-26664 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-26667 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-26669 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-26672 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-26676 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-27474 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-27736 | Windows Power Dependency Coordinator Information Disclosure Vulnerability |
| CVE-2025-27738 | Windows Resilient File System (ReFS) Information Disclosure Vulnerability |
| CVE-2025-27742 | NTFS Information Disclosure Vulnerability |
| CVE-2025-29805 | Outlook for Android Information Disclosure Vulnerability |
| CVE-2025-29808 | Windows Cryptographic Services Information Disclosure Vulnerability |
| CVE-2025-29817 | Microsoft Power Automate Desktop Information Disclosure Vulnerability |
| CVE-2025-29819 | Windows Admin Center in Azure Portal Information Disclosure Vulnerability |
| CVE-2025-29821 | Microsoft Dynamics Business Central Information Disclosure Vulnerability |
Denial of Service (14 CVEs)
| Important severity | |
| CVE-2025-21174 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2025-26641 | Microsoft Message Queuing (MSMQ) Denial of Service Vulnerability |
| CVE-2025-26651 | Windows Local Session Manager (LSM) Denial of Service Vulnerability |
| CVE-2025-26652 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2025-26673 | Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability |
| CVE-2025-26680 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2025-26682 | ASP.NET Core and Visual Studio Denial of Service Vulnerability |
| CVE-2025-27469 | Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability |
| CVE-2025-27470 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2025-27471 | Microsoft Streaming Service Denial of Service Vulnerability |
| CVE-2025-27473 | HTTP.sys Denial of Service Vulnerability |
| CVE-2025-27479 | Kerberos Key Distribution Proxy Service Denial of Service Vulnerability |
| CVE-2025-27485 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2025-27486 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
Security Feature Bypass (9 CVEs)
| Important severity | |
| CVE-2025-26635 | Windows Hello Security Feature Bypass Vulnerability |
| CVE-2025-26637 | BitLocker Security Feature Bypass Vulnerability |
| CVE-2025-26678 | Windows Defender Application Control Security Feature Bypass Vulnerability |
| CVE-2025-27472 | Windows Mark of the Web Security Feature Bypass Vulnerability |
| CVE-2025-27735 | Windows Virtualization-Based Security (VBS) Security Feature Bypass Vulnerability |
| CVE-2025-27737 | Windows Security Zone Mapping Security Feature Bypass Vulnerability |
| CVE-2025-29809 | Windows Kerberos Security Feature Bypass Vulnerability |
| CVE-2025-29816 | Microsoft Word Security Feature Bypass Vulnerability |
| CVE-2025-29822 | Microsoft OneObserve Security Feature Bypass Vulnerability |
Spoofing (4 CVE)
| Important severity | |
| CVE-2025-26644 | Windows Hello Spoofing Vulnerability |
| CVE-2025-26647 | Windows Kerberos Elevation of Privilege Vulnerability |
| CVE-2025-25001 | Microsoft Edge for iOS Spoofing Vulnerability |
| CVE-2025-29796 | Microsoft Edge for iOS Spoofing Vulnerability |
Appendix B: Exploitability and CVSS
This is an inventory of the April CVEs judged by Microsoft to be both underneath exploitation within the wild or extra more likely to be exploited within the wild inside the first 30 days post-release. The listing is additional organized by CVE.
| Exploitation detected | |
| CVE-2025-29824 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| Exploitation extra doubtless inside the subsequent 30 days | |
| CVE-2025-26663 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
| CVE-2025-26670 | Lightweight Directory Access Protocol (LDAP) Client Remote Code Execution Vulnerability |
| CVE-2025-27472 | Windows Mark of the Web Security Feature Bypass Vulnerability |
| CVE-2025-27480 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2025-27482 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2025-27727 | Windows Installer Elevation of Privilege Vulnerability |
| CVE-2025-29792 | Microsoft Office Elevation of Privilege Vulnerability |
| CVE-2025-29793 | Microsoft SharePoint Remote Code Execution Vulnerability |
| CVE-2025-29794 | Microsoft SharePoint Remote Code Execution Vulnerability |
| CVE-2025-29809 | Windows Kerberos Security Feature Bypass Vulnerability |
| CVE-2025-29812 | DirectX Graphics Kernel Elevation of Privilege Vulnerability |
This is an inventory of April’s CVEs with a Microsoft-assessed CVSS Base rating of 8.0 or greater. They are organized by rating and additional sorted by CVE. For extra info on how CVSS works, please see our sequence on patch prioritization schema.
| CVSS Base | CVSS Temporal | CVE | Title |
| 8.8 | 7.7 | CVE-2025-21205 | Windows Telephony Service Remote Code Execution Vulnerability |
| 8.8 | 7.7 | CVE-2025-21221 | Windows Telephony Service Remote Code Execution Vulnerability |
| 8.8 | 7.7 | CVE-2025-21222 | Windows Telephony Service Remote Code Execution Vulnerability |
| 8.8 | 7.7 | CVE-2025-25000 | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability |
| 8.8 | 7.7 | CVE-2025-26669 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| 8.8 | 7.7 | CVE-2025-27477 | Windows Telephony Service Remote Code Execution Vulnerability |
| 8.8 | 7.7 | CVE-2025-27481 | Windows Telephony Service Remote Code Execution Vulnerability |
| 8.8 | 7.7 | CVE-2025-27740 | Active Directory Certificate Services Elevation of Privilege Vulnerability |
| 8.8 | 7.7 | CVE-2025-29794 | Microsoft SharePoint Remote Code Execution Vulnerability |
| 8.6 | 7.5 | CVE-2025-27737 | Windows Security Zone Mapping Security Feature Bypass Vulnerability |
| 8.4 | 7.3 | CVE-2025-26678 | Windows Defender Application Control Security Feature Bypass Vulnerability |
| 8.1 | 7.1 | CVE-2025-26647 | Windows Kerberos Elevation of Privilege Vulnerability |
| 8.1 | 7.1 | CVE-2025-26663 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
| 8.1 | 7.1 | CVE-2025-26670 | Lightweight Directory Access Protocol (LDAP) Client Remote Code Execution Vulnerability |
| 8.1 | 7.1 | CVE-2025-26671 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| 8.1 | 7.1 | CVE-2025-27480 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| 8.1 | 7.1 | CVE-2025-27482 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| 8.0 | 7.0 | CVE-2025-27487 | Remote Desktop Client Remote Code Execution Vulnerability |
Appendix C: Products Affected
This is an inventory of April’s patches sorted by product household, then sub-sorted by severity. Each listing is additional organized by CVE. Patches which might be shared amongst a number of product households are listed a number of instances, as soon as for every product household. Issues affecting Windows Server are additional sorted in Appendix E.
Windows (89 CVEs)
| Critical severity | |
| CVE-2025-26663 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
| CVE-2025-26670 | Lightweight Directory Access Protocol (LDAP) Client Remote Code Execution Vulnerability |
| CVE-2025-26686 | Windows TCP/IP Remote Code Execution Vulnerability |
| CVE-2025-27480 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2025-27482 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2025-27491 | Windows Hyper-V Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2025-21174 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2025-21191 | Windows Local Security Authority (LSA) Elevation of Privilege Vulnerability |
| CVE-2025-21197 | Windows NTFS Information Disclosure Vulnerability |
| CVE-2025-21203 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-21204 | Windows Process Activation Elevation of Privilege Vulnerability |
| CVE-2025-21205 | Windows Telephony Service Remote Code Execution Vulnerability |
| CVE-2025-21221 | Windows Telephony Service Remote Code Execution Vulnerability |
| CVE-2025-21222 | Windows Telephony Service Remote Code Execution Vulnerability |
| CVE-2025-24058 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-24060 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-24062 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-24073 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-24074 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2025-26635 | Windows Hello Security Feature Bypass Vulnerability |
| CVE-2025-26637 | BitLocker Security Feature Bypass Vulnerability |
| CVE-2025-26639 | Windows USB Print Driver Elevation of Privilege Vulnerability |
| CVE-2025-26640 | Windows Digital Media Elevation of Privilege Vulnerability |
| CVE-2025-26641 | Microsoft Message Queuing (MSMQ) Denial of Service Vulnerability |
| CVE-2025-26644 | Windows Hello Spoofing Vulnerability |
| CVE-2025-26647 | Windows Kerberos Elevation of Privilege Vulnerability |
| CVE-2025-26648 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2025-26649 | Windows Secure Channel Elevation of Privilege Vulnerability |
| CVE-2025-26651 | Windows Local Session Manager (LSM) Denial of Service Vulnerability |
| CVE-2025-26652 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2025-26664 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-26665 | Windows upnphost.dll Elevation of Privilege Vulnerability |
| CVE-2025-26666 | Windows Media Remote Code Execution Vulnerability |
| CVE-2025-26667 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-26668 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2025-26669 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-26671 | Windows Remote Desktop Services Remote Code Execution Vulnerability |
| CVE-2025-26672 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-26673 | Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability |
| CVE-2025-26674 | Windows Media Remote Code Execution Vulnerability |
| CVE-2025-26675 | Windows Subsystem for Linux Elevation of Privilege Vulnerability |
| CVE-2025-26676 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-26678 | Windows Defender Application Control Security Feature Bypass Vulnerability |
| CVE-2025-26679 | RPC Endpoint Mapper Service Elevation of Privilege Vulnerability |
| CVE-2025-26680 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2025-26681 | Win32k Elevation of Privilege Vulnerability |
| CVE-2025-26687 | Win32k Elevation of Privilege Vulnerability |
| CVE-2025-26688 | Microsoft Virtual Hard Disk Elevation of Privilege Vulnerability |
| CVE-2025-27467 | Windows Digital Media Elevation of Privilege Vulnerability |
| CVE-2025-27469 | Windows Lightweight Directory Access Protocol (LDAP) Denial of Service Vulnerability |
| CVE-2025-27470 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2025-27471 | Microsoft Streaming Service Denial of Service Vulnerability |
| CVE-2025-27472 | Windows Mark of the Web Security Feature Bypass Vulnerability |
| CVE-2025-27473 | HTTP.sys Denial of Service Vulnerability |
| CVE-2025-27474 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2025-27475 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2025-27476 | Windows Digital Media Elevation of Privilege Vulnerability |
| CVE-2025-27477 | Windows Telephony Service Remote Code Execution Vulnerability |
| CVE-2025-27478 | Windows Local Security Authority (LSA) Elevation of Privilege Vulnerability |
| CVE-2025-27479 | Kerberos Key Distribution Proxy Service Denial of Service Vulnerability |
| CVE-2025-27481 | Windows Telephony Service Remote Code Execution Vulnerability |
| CVE-2025-27483 | NTFS Elevation of Privilege Vulnerability |
| CVE-2025-27484 | Windows Universal Plug and Play (UPnP) Device Host Elevation of Privilege Vulnerability |
| CVE-2025-27485 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2025-27486 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2025-27487 | Remote Desktop Client Remote Code Execution Vulnerability |
| CVE-2025-27490 | Windows Bluetooth Service Elevation of Privilege Vulnerability |
| CVE-2025-27492 | Windows Secure Channel Elevation of Privilege Vulnerability |
| CVE-2025-27727 | Windows Installer Elevation of Privilege Vulnerability |
| CVE-2025-27728 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2025-27729 | Windows Shell Remote Code Execution Vulnerability |
| CVE-2025-27730 | Windows Digital Media Elevation of Privilege Vulnerability |
| CVE-2025-27731 | Microsoft OpenSSH for Windows Elevation of Privilege Vulnerability |
| CVE-2025-27732 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2025-27733 | NTFS Elevation of Privilege Vulnerability |
| CVE-2025-27735 | Windows Virtualization-Based Security (VBS) Security Feature Bypass Vulnerability |
| CVE-2025-27736 | Windows Power Dependency Coordinator Information Disclosure Vulnerability |
| CVE-2025-27737 | Windows Security Zone Mapping Security Feature Bypass Vulnerability |
| CVE-2025-27738 | Windows Resilient File System (ReFS) Information Disclosure Vulnerability |
| CVE-2025-27739 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2025-27740 | Active Directory Certificate Services Elevation of Privilege Vulnerability |
| CVE-2025-27741 | NTFS Elevation of Privilege Vulnerability |
| CVE-2025-27742 | NTFS Information Disclosure Vulnerability |
| CVE-2025-29808 | Windows Cryptographic Services Information Disclosure Vulnerability |
| CVE-2025-29809 | Windows Kerberos Security Feature Bypass Vulnerability |
| CVE-2025-29810 | Active Directory Domain Services Elevation of Privilege Vulnerability |
| CVE-2025-29811 | Windows Mobile Broadband Driver Elevation of Privilege Vulnerability |
| CVE-2025-29812 | DirectX Graphics Kernel Elevation of Privilege Vulnerability |
| CVE-2025-29824 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
365 (15 CVEs)
| Critical severity | |
| CVE-2025-27745 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27748 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27749 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27752 | Microsoft Excel Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2025-26642 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27746 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27747 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-27750 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-27751 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-29791 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-29792 | Microsoft Office Elevation of Privilege Vulnerability |
| CVE-2025-29816 | Microsoft Word Security Feature Bypass Vulnerability |
| CVE-2025-29820 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-29822 | Microsoft OneObserve Security Feature Bypass Vulnerability |
| CVE-2025-29823 | Microsoft Excel Remote Code Execution Vulnerability |
Office (15 CVEs)
| Critical severity | |
| CVE-2025-27745 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27748 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27749 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27752 | Microsoft Excel Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2025-26642 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-26687 | Win32k Elevation of Privilege Vulnerability |
| CVE-2025-27744 | Microsoft Office Elevation of Privilege Vulnerability |
| CVE-2025-27746 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27747 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-27750 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-27751 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-29792 | Microsoft Office Elevation of Privilege Vulnerability |
| CVE-2025-29816 | Microsoft Word Security Feature Bypass Vulnerability |
| CVE-2025-29820 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-29822 | Microsoft OneObserve Security Feature Bypass Vulnerability |
Edge (13 CVEs)
| Important severity | |
| CVE-2025-25000 | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability |
| CVE-2025-29815 | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability |
| Low severity | |
| CVE-2025-25001 | Microsoft Edge for iOS Spoofing Vulnerability |
| CVE-2025-29796 | Microsoft Edge for iOS Spoofing Vulnerability |
| Chromium severity schema | |
| High severity | |
| CVE-2025-3066 | Chromium: CVE-2025-3066 Use after free in Navigations |
| Medium severity | |
| CVE-2025-3067 | Chromium: CVE-2025-3067 Inappropriate implementation in Custom Tabs |
| CVE-2025-3068 | Chromium: CVE-2025-3068 Inappropriate implementation in Intents |
| CVE-2025-3069 | Chromium: CVE-2025-3069 Inappropriate implementation in Extensions |
| CVE-2025-3070 | Chromium: CVE-2025-3070 Insufficient validation of untrusted enter in Extensions |
| Low severity | |
| CVE-2025-3071 | Chromium: CVE-2025-3071 Inappropriate implementation in Navigations |
| CVE-2025-3072 | Chromium: CVE-2025-3072 Inappropriate implementation in Custom Tabs |
| CVE-2025-3073 | Chromium: CVE-2025-3073 Inappropriate implementation in Autofill |
| CVE-2025-3074 | Chromium: CVE-2025-3074 Inappropriate implementation in Downloads |
SharePoint (6 CVEs)
| Important severity | |
| CVE-2025-26642 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27746 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27747 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-29793 | Microsoft SharePoint Remote Code Execution Vulnerability |
| CVE-2025-29794 | Microsoft SharePoint Remote Code Execution Vulnerability |
| CVE-2025-29820 | Microsoft Word Remote Code Execution Vulnerability |
Visual Studio (5 CVEs)
| Important severity | |
| CVE-2025-20570 | Visual Studio Code Elevation of Privilege Vulnerability |
| CVE-2025-26682 | ASP.NET Core and Visual Studio Denial of Service Vulnerability |
| CVE-2025-29802 | Visual Studio Elevation of Privilege Vulnerability |
| CVE-2025-29804 | Visual Studio Elevation of Privilege Vulnerability |
Azure (4 CVEs)
| Important severity | |
| CVE-2025-25002 | Azure Local Cluster Information Disclosure Vulnerability |
| CVE-2025-26628 | Azure Local Cluster Information Disclosure Vulnerability |
| CVE-2025-27489 | Azure Local Elevation of Privilege Vulnerability |
| CVE-2025-29819 | Windows Admin Center in Azure Portal Information Disclosure Vulnerability |
Excel (3 CVEs)
| Important severity | |
| CVE-2025-26642 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-27750 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-27751 | Microsoft Excel Remote Code Execution Vulnerability |
Microsoft AutoUpdater for Mac (2 CVEs)
| Important severity | |
| CVE-2025-29800 | Microsoft AutoUpdate (MAU) Elevation of Privilege Vulnerability |
| CVE-2025-29801 | Microsoft AutoUpdate (MAU) Elevation of Privilege Vulnerability |
Word (2 CVEs)
| Important severity | |
| CVE-2025-27747 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2025-29816 | Microsoft Word Security Feature Bypass Vulnerability |
Access (1 CVE)
| Important severity | |
| CVE-2025-26642 | Microsoft Office Remote Code Execution Vulnerability |
ASP.NET (1 CVE)
| Important severity | |
| CVE-2025-26682 | ASP.NET Core and Visual Studio Denial of Service Vulnerability |
Dynamics 365 (1 CVE)
| Important severity | |
| CVE-2025-29821 | Microsoft Dynamics Business Central Information Disclosure Vulnerability |
OneObserve (1 CVE)
| Important severity | |
| CVE-2025-29822 | Microsoft OneObserve Security Feature Bypass Vulnerability |
Outlook for Android (1 CVE)
| Important severity | |
| CVE-2025-29805 | Outlook for Android Information Disclosure Vulnerability |
Power Automate Desktop (1 CVE)
| Important severity | |
| CVE-2025-29817 | Microsoft Power Automate Desktop Information Disclosure Vulnerability |
SQL Server (1 CVE)
| Important severity | |
| CVE-2025-29803 | Visual Studio Tools for Applications and SQL Server Management Studio Elevation of Privilege Vulnerability |
System Center (1 CVE)
| Important severity | |
| CVE-2025-27743 | Microsoft System Center Elevation of Privilege Vulnerability |
VSTA (1 CVE)
| Important severity | |
| CVE-2025-29803 | Visual Studio Tools for Applications and SQL Server Management Studio Elevation of Privilege Vulnerability |
Appendix D: Advisories and Other Products
There are 16 Adobe advisories on this month’s launch.
| CVE-2025-24446 | APSB25-15 | Improper Input Validation |
| CVE-2025-24447 | APSB25-15 | Deserialization of Untrusted Data |
| CVE-2025-30281 | APSB25-15 | Improper Access Control |
| CVE-2025-30282 | APSB25-15 | Improper Authentication |
| CVE-2025-30283 | APSB25-15 | Improper Input Validation |
| CVE-2025-30284 | APSB25-15 | Deserialization of Untrusted Data |
| CVE-2025-30285 | APSB25-15 | Deserialization of Untrusted Data |
| CVE-2025-30286 | APSB25-15 | Improper Neutralization of Special Elements utilized in an OS Command (‘OS Command Injection’) |
| CVE-2025-30287 | APSB25-15 | Improper Authentication |
| CVE-2025-30288 | APSB25-15 | Improper Access Control |
| CVE-2025-30289 | APSB25-15 | Improper Neutralization of Special Elements utilized in an OS Command (‘OS Command Injection’) |
| CVE-2025-30290 | APSB25-15 | Improper Limitation of a Pathname to a Restricted Directory (‘Path Traversal’) |
| CVE-2025-30291 | APSB25-15 | Information Exposure |
| CVE-2025-30292 | APSB25-15 | Cross-site Scripting (Reflected XSS) |
| CVE-2025-30293 | APSB25-15 | Improper Input Validation |
| CVE-2025-30294 | APSB25-15 | Improper Input Validation |
Appendix E: Affected Windows Server variations
This is a desk of the CVEs within the April launch affecting 9 Windows Server variations, 2008 by means of 2025. The desk differentiates amongst main variations of the platform however doesn’t go into deeper element (eg., Server Core). Critical-severity points are marked in pink; an “x” signifies that the CVE doesn’t apply to that model. Administrators are inspired to make use of this appendix as a place to begin to determine their particular publicity, as every reader’s scenario, particularly because it issues merchandise out of mainstream assist, will differ. For particular Knowledge Base numbers, please seek the advice of Microsoft. Please be aware that CVE-2025-27475 is a client-only Windows subject and thus seems on this chart, however with no server variations marked.
| 2008 | 2008-R2 | 2012 | 2012-R2 | 2016 | 2019 | 2022 | 2022 23H2 | 2025 | |
| CVE-2025-21174 | × | × | × | ■ | ■ | ■ | ■ | × | ■ |
| CVE-2025-21191 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-21197 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-21203 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-21204 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-21205 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-21221 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-21222 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-24058 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-24060 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-24062 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2025-24073 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-24074 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-26635 | × | × | × | × | × | ■ | ■ | ■ | × |
| CVE-2025-26637 | × | × | × | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26639 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2025-26640 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2025-26641 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26644 | × | × | × | × | × | ■ | × | × | ■ |
| CVE-2025-26647 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26648 | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26649 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2025-26651 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2025-26652 | × | × | × | ■ | ■ | ■ | ■ | × | ■ |
| CVE-2025-26663 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26664 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26665 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26666 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-26667 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26668 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26669 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26670 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26671 | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26672 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26673 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26674 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-26675 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2025-26676 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26678 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-26679 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26680 | × | × | × | ■ | ■ | ■ | ■ | × | ■ |
| CVE-2025-26681 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2025-26686 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26687 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-26688 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27467 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2025-27469 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27470 | × | × | × | ■ | ■ | ■ | ■ | × | ■ |
| CVE-2025-27471 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27472 | × | × | ■ | ■ | × | × | × | × | × |
| CVE-2025-27473 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27474 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27475 | × | × | × | × | × | × | × | × | × |
| CVE-2025-27476 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2025-27477 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27478 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27479 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27480 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27481 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27482 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27483 | × | × | × | ■ | ■ | ■ | × | × | × |
| CVE-2025-27484 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27485 | × | × | × | ■ | ■ | ■ | ■ | × | ■ |
| CVE-2025-27486 | × | × | × | ■ | ■ | ■ | ■ | × | ■ |
| CVE-2025-27487 | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27490 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2025-27491 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27492 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2025-27727 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27728 | × | × | × | × | × | × | × | × | ■ |
| CVE-2025-27729 | × | × | × | × | × | × | × | × | ■ |
| CVE-2025-27730 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2025-27731 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-27732 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27733 | ■ | ■ | ■ | ■ | ■ | ■ | × | × | × |
| CVE-2025-27735 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27736 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27737 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27738 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27739 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-27740 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-27741 | ■ | ■ | ■ | ■ | ■ | × | × | × | × |
| CVE-2025-27742 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-29808 | × | × | × | × | × | × | ■ | × | × |
| CVE-2025-29809 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-29810 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-29811 | × | × | × | × | × | × | × | ■ | ■ |
| CVE-2025-29812 | × | × | × | × | × | × | ■ | ■ | ■ |
| CVE-2025-29824 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
[ad_2]