A brand new report from Mandiant, a part of Google Cloud, reveals {that a} financially motivated risk actor named UNC5537 collected and exfiltrated information from about 165 organizations’ Snowflake buyer cases. Snowflake is a cloud information platform used for storing and analyzing massive volumes of information.
The risk actor managed to get entry to those information by triggering credentials that have been beforehand stolen by infostealer malware or bought from different cybercriminals.
According to Mandiant, the risk actor UNC5537 advertises sufferer information on the market on cybercrime boards and makes an attempt to extort most of the victims. When the info is bought, any cybercriminal may purchase this info for various functions comparable to cyber espionage, aggressive intelligence or extra financially-oriented fraud.
How have been some Snowflake customers focused for this information theft and extortion?
A joint assertion offered by Snowflake, Mandiant and cybersecurity firm CrowdStrike signifies there is no such thing as a proof suggesting the fraudulent exercise could be attributable to a vulnerability, misconfiguration or breach of Snowflake’s platform. There can be no proof the exercise would have been attributable to compromised credentials from present or previous Snowflake staff.
Instead, proof reveals the attackers obtained credentials from a number of infostealer malware campaigns that contaminated non-Snowflake owned programs. The risk actor then gained entry to the affected accounts, which allowed the exfiltration of a big quantity of buyer information from the respective Snowflake buyer cases.
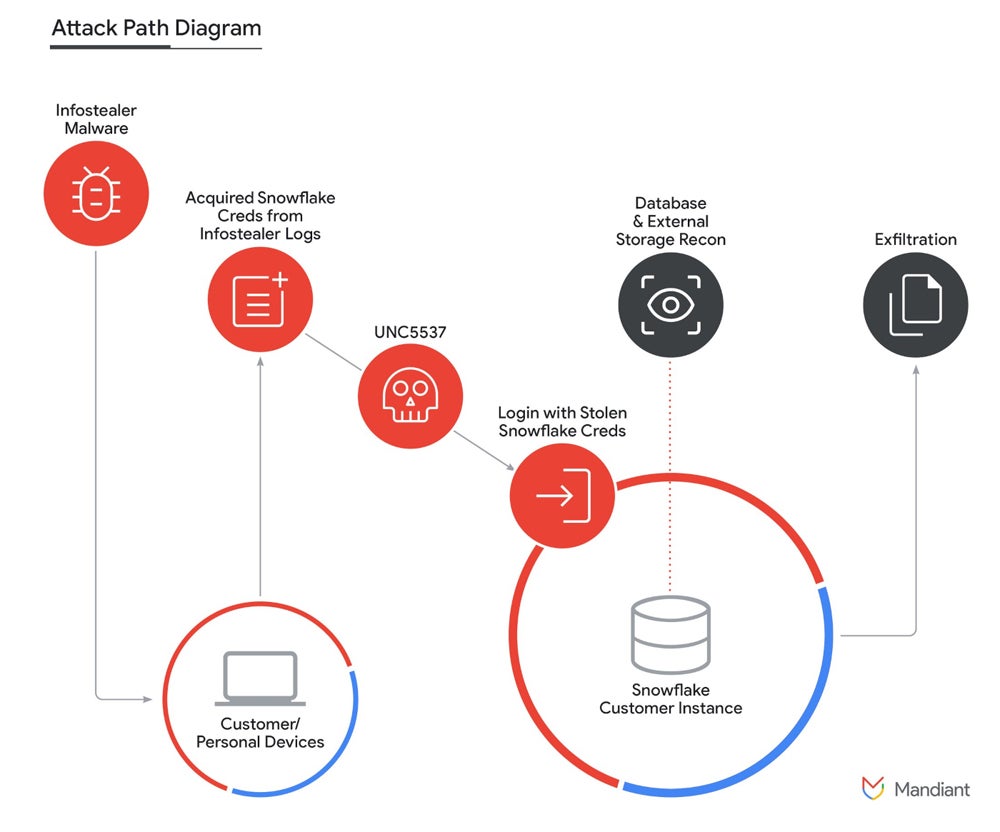
Mandiant researchers acknowledged nearly all of the credentials utilized by UNC5537 have been obtainable from historic infostealer malware; a few of these credentials date again to November 2020 however have been nonetheless usable. Different infostealer malware households have been answerable for the credentials theft — essentially the most used ones being Vidar, Risepro, Redline, Racoon Stealer, Lumma and Metastealer.
According to Mandiant and Snowflake, no less than 79.7% of the accounts leveraged by the risk actor had prior credential publicity.
Mandiant additionally reported the preliminary compromise of infostealer malware occurred on contractor programs that have been additionally used for private actions, together with gaming and downloads of pirated software program, which is a robust vector for spreading infostealers.
How did UNC5537 get hold of the stolen credentials?
As reported, the risk actor obtained credentials from quite a lot of infostealer malware, but UNC5537 additionally leveraged credentials that have been beforehand bought.
While no further info is offered by Mandiant, it’s affordable to assume these credentials have been purchased in a single or a number of cybercriminal underground marketplaces on to so-called Initial Access Brokers, that are a class of cybercriminals who promote stolen company entry to different fraudsters.
As written by Mandiant in its report, “the underground infostealer economy is also extremely robust, and large lists of stolen credentials exist both for free and for purchase inside and outside of the dark web.” Mandiant additionally reported that, in 2023, 10% of total intrusions started with stolen credentials, representing the fourth most notable preliminary intrusion vector.
What was the preliminary entry and information exfiltration strategies on this Snowflake assault?
In this assault marketing campaign, the preliminary entry to Snowflake buyer cases usually occurred by way of the native consumer interface accessible from the online (Snowflake SnowSight) or from the command-line interface software offered by Snowflake (SnowSQL). An further attacker-named software referred to as “rapeflake” and tracked below FROSTBITE by Mandiant has been used to carry out reconnaissance towards Snowflake cases.
FROSTBITE exists in no less than two variations: one utilizing .NET to work together with the Snowflake .NET driver, and one model utilizing Java to work together with the Snowflake JDBC driver. The software permits the attackers to carry out SQL actions comparable to itemizing customers, present roles, present IP addresses, session IDs and organizations’ names.
A public software for managing databases, DBeaver Ultimate, has additionally been utilized by the risk actor to run queries on the Snowflake cases.
Using SQL queries, the risk actor was in a position to exfiltrate info from databases. Once attention-grabbing information was discovered, it was compressed as GZIP utilizing the “COPY INTO” command to scale back the scale of the info to be exfiltrated.
The attacker primarily used Mullvad and Private Internet Access VPN companies to entry the victims’ Snowflake cases. A moldovan VPS supplier, ALEXHOST SRL, was additionally used for information exfiltration. The risk actor saved sufferer information on a number of worldwide VPS suppliers, in addition to on the cloud storage supplier MEGA.
What organizations are in danger?
The assault marketing campaign seems to be a focused marketing campaign aimed toward Snowflake customers with single-factor authentication. All customers with multifactor authentication are protected from this assault marketing campaign and weren’t focused.
In addition, the impacted Snowflake buyer cases didn’t have permit lists in place to solely permit connections from trusted areas.
Tips from Snowflake on the best way to shield your corporation from this cybersecurity risk
Snowflake revealed info on detecting and stopping unauthorized consumer entry.
The firm offered a listing of virtually 300 suspicious IP addresses utilized by the risk actor and shared a question to determine entry from the suspect IP addresses. The firm additionally offered a question to determine the utilization of the “rapeflake” and “DBeaver Ultimate” instruments. Any consumer account returning outcomes from these queries should instantly be disabled.
Security hardening is extremely really helpful by Snowflake:
- Enforce MFA for customers.
- Set up account-level and user-level community insurance policies for extremely credentialed customers/companies accounts.
- Review account parameters to limit information exportation from Snowflake accounts.
- Monitor Snowflake accounts for unauthorized privilege escalation or configuration modifications and examine any of these occasions.
Additionally, it’s strongly really helpful to have all software program and working programs updated and patched to keep away from being compromised by a standard vulnerability, which could result in credentials leak.
Security options should be deployed on each endpoint to forestall infostealer an infection.
It can be suggested to lift consciousness on pc safety and prepare workers to detect and report suspicious cybersecurity occasions.
Disclosure: I work for Trend Micro, however the views expressed on this article are mine.

