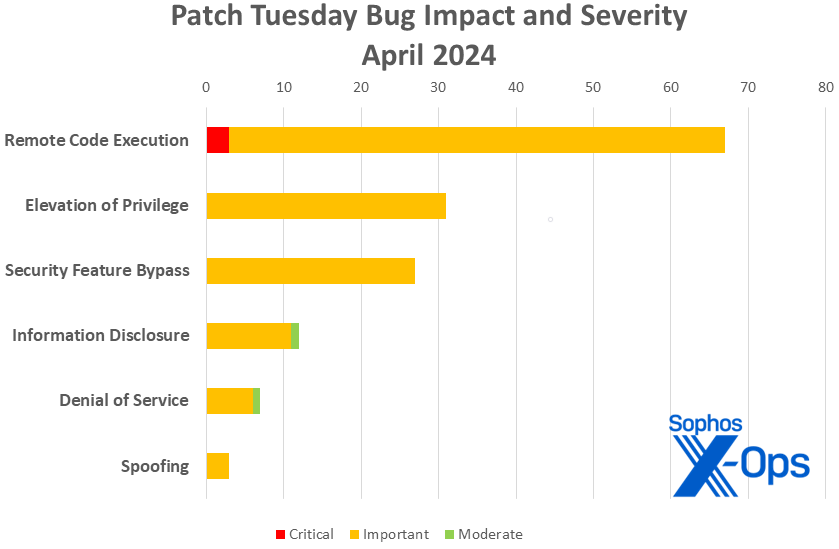
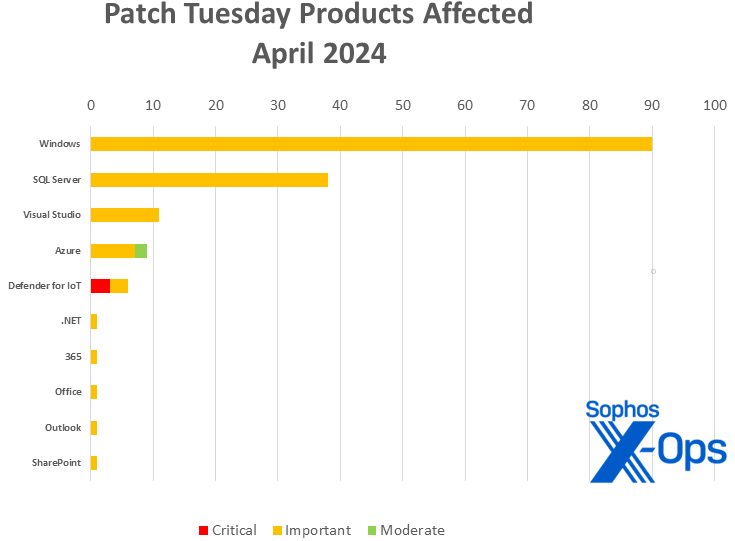
Several months of relative calm are over for Windows directors, as Microsoft on Tuesday launched 147 patches affecting ten product households. Windows takes the lion’s share of patches with 90, with 38 for SQL Server (together with ten shared with Visual Studio). The relaxation are unfold amongst .NET, 365, Azure, Defender for IoT, Office, Outlook, and SharePoint. There are three critical-severity points, all affecting Defender for IoT.
At patch time, three points, all important-severity faults affecting Windows, are recognized to be below lively exploit within the wild. One (CVE-2024-26234, a driver-related problem reported to Microsoft by Sophos) is publicly disclosed, as we’ll focus on beneath. Eleven extra important-severity vulnerabilities in Windows are by the corporate’s estimation extra prone to be exploited within the subsequent 30 days. Six of the problems addressed are amenable to detection by Sophos protections, and we embrace data on these in a desk beneath.
In addition to those patches, the discharge contains advisory data on 5 patches associated to the Edge browser and 5 from Intel, Lenovo, and Red Hat; the usually scheduled servicing stack updates are additionally included in advisory materials this month. We don’t embrace advisories within the CVE counts and graphics beneath, however we offer data on all of them in an appendix on the finish of the article. We are as standard together with on the finish of this submit three different appendices itemizing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product household.
By the numbers
- Total Microsoft CVEs: 147
- Total Edge / Chrome advisory points lined in replace: 5
- Total non-Edge, non-Microsoft advisory points overed in replace: 5
- Publicly disclosed: 1
- Currently exploited: 3
- Severity
- Critical: 3
- Important: 142
- Moderate: 2
- Impact
- Remote Code Execution: 67
- Elevation of Privilege: 31
- Security Feature Bypass: 27
- Information Disclosure: 12
- Denial of Service: 7
- Spoofing: 3
Figure 1: RCEs got here roaring to the forefront this month, however Security Feature Bypass makes a formidable exhibiting (extra on that in a bit)
Products
- Windows: 90
- SQL Server: 38 (together with 10 shared with Visual Studio)
- Visual Studio: 11 (together with 10 shared with SQL Server and one shared with .NET)
- Azure: 9
- Defender for IoT: 6
- .NET: 1 (shared with Visual Studio)
- 365: 1 (shared with Office)
- Office: 1 (shared with 365)
- Outlook: 1
- SharePoint: 1
Figure 2: Windows accounts for slightly below two-thirds of the April 2024 patches, with 9 different product households additionally within the combine (however 5 of these receiving only one patch)
Notable April updates and themes
In addition to the problems mentioned above, a couple of particular objects benefit consideration.
Startup Issues Stack Up
Secure Boot Security Feature Bypass Vulnerability – 24 patches
BitLocker Security Feature Bypass Vulnerability – 1 patch
Lenovo: CVE-2024-23593 Zero Out Boot Manager and drop to UEFI Shell – 1 patch
Lenovo: CVE-2024-23594 Stack Buffer Overflow in LenovoBT.efi – 1 patch
Secure Boot and BitLocker are having an fascinating month. All 25 Microsoft patches are important-severity points. Microsoft says that none of them are at present below lively exploitation and that they imagine exploitation is much less seemingly within the 30 days after launch. The two points from Lenovo are likewise associated as well processes, are characterised by Microsoft as important-severity Security Feature Bypass faults and are considered much less prone to be exploited throughout the subsequent 30 days. (It ought to be famous that Microsoft mentions the Lenovo releases merely as advisory data.)
CVE-2024-26234 – Proxy Driver Spoofing Vulnerability
As talked about above, again in December, Sophos X-Ops opened an investigation of a suspicious-looking executable that claimed to be signed by a legitimate Microsoft Hardware Publisher Certificate. You can examine what occurred subsequent in our writeup of what we found. For Microsoft’s half, the corporate has added the related information to its rolling revocation listing, which is up to date on this patch cycle below this CVE. It is the only real problem this month that’s thought of to be publicly disclosed.
A Tough Month for SQL Server
Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability – 13 patches
Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability – 24 patches
Microsoft WDAC OLE DB Provider for SQL Server Remote Code Execution Vulnerability – 3 patches
Microsoft WDAC SQL Server ODBC Driver Remote Code Execution Vulnerability – 1 patch
These 41 patches are all important-severity points with CVE numbers seemingly assigned from Microsoft’s CAN block (nearly all of them are sequential, which normally signifies that they have been drawn from the identical block at about the identical time). Microsoft says that none of them are at present below lively exploitation and that they imagine exploitation is much less seemingly within the 30 days after launch.
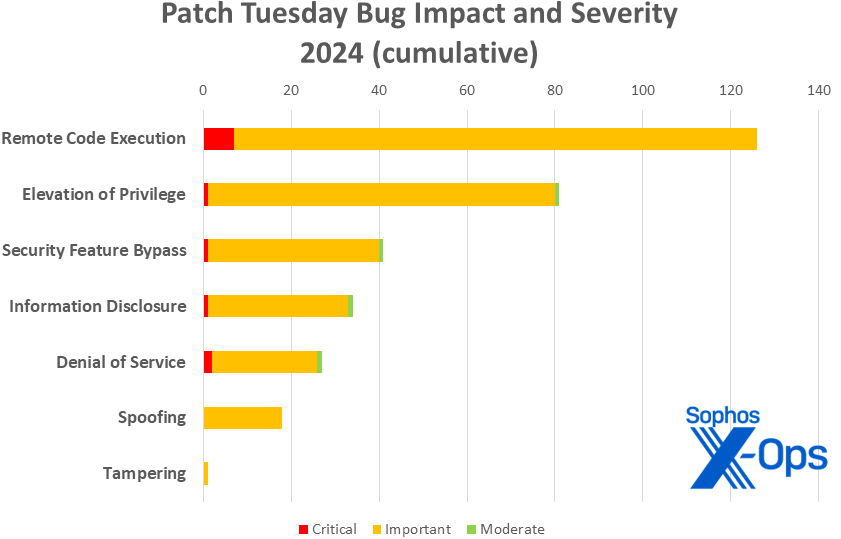
Figure 3: Security Feature Bypass leaps to 3rd place within the cumulative patch totals for 2024, although RCE nonetheless leads the pack
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-26209 | Exp/2426209-A | Exp/2426209-A |
| CVE-2024-26211 | Exp/2426211-A | Exp/2426211-A |
| CVE-2024-26212 | Exp/2426212-A | sid:2309495 |
| CVE-2024-26218 | Exp/2426218-A | Exp/2426218-A |
| CVE-2024-26230 | Exp/2426230-A | Exp/2426230-A |
| CVE-2024-26234 | Mal/Proxcat-A | N/A |
As you’ll be able to each month, in the event you don’t need to wait to your system to tug down Microsoft’s updates itself, you’ll be able to obtain them manually from the Windows Update Catalog web site. Run the winver.exe software to find out which construct of Windows 10 or 11 you’re working, then obtain the Cumulative Update package deal to your particular system’s structure and construct quantity.
Appendix A: Vulnerability Impact and Severity
This is an inventory of April patches sorted by affect, then sub-sorted by severity. Each listing is additional organized by CVE. In an effort to maintain our readers knowledgeable, we additionally present CVSS base and temp scores as these develop into accessible, since these might differ from Microsoft’s self-assessments.
Remote Code Execution (68 CVEs)
| Critical severity | |
| CVE-2024-21322 | Microsoft Defender for IoT Remote Code Execution Vulnerability |
| CVE-2024-21323 | Microsoft Defender for IoT Remote Code Execution Vulnerability |
| CVE-2024-29053 | Microsoft Defender for IoT Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2024-20678 | Remote Procedure Call Runtime Remote Code Execution Vulnerability |
| CVE-2024-21409 | .NET, .NET Framework, and Visual Studio Remote Code Execution Vulnerability |
| CVE-2024-26179 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-26193 | Azure Migrate Remote Code Execution Vulnerability |
| CVE-2024-26195 | DHCP Server Service Remote Code Execution Vulnerability |
| CVE-2024-26200 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-26202 | DHCP Server Service Remote Code Execution Vulnerability |
| CVE-2024-26205 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-26208 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
| CVE-2024-26210 | Microsoft WDAC OLE DB Provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-26214 | Microsoft WDAC SQL Server ODBC Driver Remote Code Execution Vulnerability |
| CVE-2024-26221 | Windows DNS Server Remote Code Execution Vulnerability |
| CVE-2024-26222 | Windows DNS Server Remote Code Execution Vulnerability |
| CVE-2024-26223 | Windows DNS Server Remote Code Execution Vulnerability |
| CVE-2024-26224 | Windows DNS Server Remote Code Execution Vulnerability |
| CVE-2024-26227 | Windows DNS Server Remote Code Execution Vulnerability |
| CVE-2024-26231 | Windows DNS Server Remote Code Execution Vulnerability |
| CVE-2024-26232 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
| CVE-2024-26233 | Windows DNS Server Remote Code Execution Vulnerability |
| CVE-2024-26244 | Microsoft WDAC OLE DB Provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-26252 | Windows rndismp6.sys Remote Code Execution Vulnerability |
| CVE-2024-26253 | Windows rndismp6.sys Remote Code Execution Vulnerability |
| CVE-2024-26256 | libarchive Remote Code Execution Vulnerability |
| CVE-2024-26257 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-28906 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28908 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28909 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28910 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28911 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28912 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28913 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28914 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28915 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28926 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28927 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28929 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28930 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28931 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28932 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28933 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28934 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28935 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28936 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28937 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28938 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28939 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28940 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28941 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28942 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28943 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28944 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28945 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29043 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29044 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29045 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29046 | Microsoft WDAC OLE DB Provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29047 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29048 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29050 | Windows Cryptographic Services Remote Code Execution Vulnerability |
| CVE-2024-29066 | Windows Distributed File System (DFS) Remote Code Execution Vulnerability |
| CVE-2024-29982 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29983 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29984 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29985 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
Elevation of Privilege (31 CVEs)
| Important severity | |
| CVE-2024-20693 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21324 | Microsoft Defender for IoT Elevation of Privilege Vulnerability |
| CVE-2024-21424 | Azure Compute Gallery Elevation of Privilege Vulnerability |
| CVE-2024-21447 | Windows Authentication Elevation of Privilege Vulnerability |
| CVE-2024-26158 | Microsoft Install Service Elevation of Privilege Vulnerability |
| CVE-2024-26211 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability |
| CVE-2024-26213 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2024-26216 | Windows File Server Resource Management Service Elevation of Privilege Vulnerability |
| CVE-2024-26218 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26229 | Windows CSC Service Elevation of Privilege Vulnerability |
| CVE-2024-26230 | Windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-26235 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2024-26236 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2024-26237 | Windows Defender Credential Guard Elevation of Privilege Vulnerability |
| CVE-2024-26239 | Windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-26241 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-26242 | Windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-26243 | Windows USB Print Driver Elevation of Privilege Vulnerability |
| CVE-2024-26245 | Windows SMB Elevation of Privilege Vulnerability |
| CVE-2024-26248 | Windows Kerberos Elevation of Privilege Vulnerability |
| CVE-2024-28904 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2024-28905 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2024-28907 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2024-28917 | Azure Arc-enabled Kubernetes Extension Cluster-Scope Elevation of Privilege Vulnerability |
| CVE-2024-29052 | Windows Storage Elevation of Privilege Vulnerability |
| CVE-2024-29054 | Microsoft Defender for IoT Elevation of Privilege Vulnerability |
| CVE-2024-29055 | Microsoft Defender for IoT Elevation of Privilege Vulnerability |
| CVE-2024-29056 | Windows Authentication Elevation of Privilege Vulnerability |
| CVE-2024-29989 | Azure Monitor Agent Elevation of Privilege Vulnerability |
| CVE-2024-29990 | Microsoft Azure Kubernetes Service Confidential Container Elevation of Privilege Vulnerability |
| CVE-2024-29993 | Azure CycleCloud Elevation of Privilege Vulnerability |
Security Feature Bypass (26 CVEs)
| Important severity | |
| CVE-2024-20665 | BitLocker Security Feature Bypass Vulnerability |
| CVE-2024-20669 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-20688 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-20689 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26168 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26171 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26175 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26180 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26189 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26194 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26228 | Windows Cryptographic Services Security Feature Bypass Vulnerability |
| CVE-2024-26240 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26250 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28896 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28897 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28898 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28903 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28919 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28920 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28921 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28922 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28923 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28924 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28925 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-29061 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-29062 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-29988 | Internet Shortcut Files Security Feature Bypass Vulnerability |
Information Disclosure (12 CVEs)
| Important severity | |
| CVE-2024-26172 | Microsoft DWM Core Library Information Disclosure Vulnerability |
| CVE-2024-26207 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-26209 | Microsoft Local Security Authority Subsystem Service Information Disclosure Vulnerability |
| CVE-2024-26217 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-26220 | Windows Mobile Hotspot Information Disclosure Vulnerability |
| CVE-2024-26226 | Windows Distributed File System (DFS) Information Disclosure Vulnerability |
| CVE-2024-26255 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-28900 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-28901 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-28902 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-29063 | Azure AI Search Information Disclosure Vulnerability |
| CVE-2024-29992 | Azure Identity Library for .NET Information Disclosure Vulnerability |
Denial of Service (7 CVEs)
| Important severity | |
| CVE-2024-26183 | Windows Kerberos Denial of Service Vulnerability |
| CVE-2024-26212 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2024-26215 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2024-26219 | HTTP.sys Denial of Service Vulnerability |
| CVE-2024-26254 | Microsoft Virtual Machine Bus (VMBus) Denial of Service Vulnerability |
| CVE-2024-29064 | Windows Hyper-V Denial of Service Vulnerability |
| Moderate severity | |
| CVE-2024-20685 | Azure Private 5G Core Denial of Service Vulnerability |
Spoofing (3 CVEs)
| Important severity | |
| CVE-2024-20670 | Outlook for Windows Spoofing Vulnerability |
| CVE-2024-26234 | Proxy Driver Spoofing Vulnerability |
| CVE-2024-26251 | Microsoft SharePoint Server Spoofing Vulnerability |
Appendix B: Exploitability
This is an inventory of the April CVEs already below exploit within the wild, and people judged by Microsoft to be extra prone to be exploited within the wild throughout the first 30 days post-release. The listing is organized by CVE.
| Exploitation detected | |
| CVE-2024-26234 | Proxy Driver Spoofing Vulnerability |
| CVE-2024-28903 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28921 | Secure Boot Security Feature Bypass Vulnerability |
| Exploitation extra seemingly throughout the subsequent 30 days | |
| CVE-2024-26158 | Microsoft Install Service Elevation of Privilege Vulnerability |
| CVE-2024-26209 | Microsoft Local Security Authority Subsystem Service Information Disclosure Vulnerability |
| CVE-2024-26211 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability |
| CVE-2024-26212 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2024-26218 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26230 | Windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-26239 | Windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-26241 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-26256 | libarchive Remote Code Execution Vulnerability |
| CVE-2024-29056 | Windows Authentication Elevation of Privilege Vulnerability |
| CVE-2024-29988 | Internet Shortcut Files Security Feature Bypass Vulnerability |
Appendix C: Products Affected
This is an inventory of April’s patches sorted by product household, then sub-sorted by severity. Each listing is additional organized by CVE. Patches which are shared amongst a number of product households are listed a number of occasions, as soon as for every product household.
Windows (90 CVEs)
| Important severity | |
| CVE-2024-20665 | BitLocker Security Feature Bypass Vulnerability |
| CVE-2024-20669 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-20678 | Remote Procedure Call Runtime Remote Code Execution Vulnerability |
| CVE-2024-20688 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-20689 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-20693 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21447 | Windows Authentication Elevation of Privilege Vulnerability |
| CVE-2024-26158 | Microsoft Install Service Elevation of Privilege Vulnerability |
| CVE-2024-26168 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26171 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26172 | Microsoft DWM Core Library Information Disclosure Vulnerability |
| CVE-2024-26175 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26179 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-26180 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26183 | Windows Kerberos Denial of Service Vulnerability |
| CVE-2024-26189 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26194 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26195 | DHCP Server Service Remote Code Execution Vulnerability |
| CVE-2024-26200 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-26202 | DHCP Server Service Remote Code Execution Vulnerability |
| CVE-2024-26205 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-26207 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-26208 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
| CVE-2024-26209 | Microsoft Local Security Authority Subsystem Service Information Disclosure Vulnerability |
| CVE-2024-26210 | Microsoft WDAC OLE DB Provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-26211 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability |
| CVE-2024-26212 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2024-26213 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2024-26214 | Microsoft WDAC SQL Server ODBC Driver Remote Code Execution Vulnerability |
| CVE-2024-26215 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2024-26216 | Windows File Server Resource Management Service Elevation of Privilege Vulnerability |
| CVE-2024-26217 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-26218 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-26219 | HTTP.sys Denial of Service Vulnerability |
| CVE-2024-26220 | Windows Mobile Hotspot Information Disclosure Vulnerability |
| CVE-2024-26221 | Windows DNS Server Remote Code Execution Vulnerability |
| CVE-2024-26222 | Windows DNS Server Remote Code Execution Vulnerability |
| CVE-2024-26223 | Windows DNS Server Remote Code Execution Vulnerability |
| CVE-2024-26224 | Windows DNS Server Remote Code Execution Vulnerability |
| CVE-2024-26226 | Windows Distributed File System (DFS) Information Disclosure Vulnerability |
| CVE-2024-26227 | Windows DNS Server Remote Code Execution Vulnerability |
| CVE-2024-26228 | Windows Cryptographic Services Security Feature Bypass Vulnerability |
| CVE-2024-26229 | Windows CSC Service Elevation of Privilege Vulnerability |
| CVE-2024-26230 | Windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-26231 | Windows DNS Server Remote Code Execution Vulnerability |
| CVE-2024-26232 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
| CVE-2024-26233 | Windows DNS Server Remote Code Execution Vulnerability |
| CVE-2024-26234 | Proxy Driver Spoofing Vulnerability |
| CVE-2024-26235 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2024-26236 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2024-26237 | Windows Defender Credential Guard Elevation of Privilege Vulnerability |
| CVE-2024-26239 | Windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-26240 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26241 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-26242 | Windows Telephony Server Elevation of Privilege Vulnerability |
| CVE-2024-26243 | Windows USB Print Driver Elevation of Privilege Vulnerability |
| CVE-2024-26244 | Microsoft WDAC OLE DB Provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-26245 | Windows SMB Elevation of Privilege Vulnerability |
| CVE-2024-26248 | Windows Kerberos Elevation of Privilege Vulnerability |
| CVE-2024-26250 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-26252 | Windows rndismp6.sys Remote Code Execution Vulnerability |
| CVE-2024-26253 | Windows rndismp6.sys Remote Code Execution Vulnerability |
| CVE-2024-26254 | Microsoft Virtual Machine Bus (VMBus) Denial of Service Vulnerability |
| CVE-2024-26255 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-26256 | libarchive Remote Code Execution Vulnerability |
| CVE-2024-28896 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28897 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28898 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28900 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-28901 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-28902 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-28903 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28904 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2024-28905 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2024-28907 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2024-28919 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28920 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28921 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28922 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28923 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28924 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-28925 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-29050 | Windows Cryptographic Services Remote Code Execution Vulnerability |
| CVE-2024-29052 | Windows Storage Elevation of Privilege Vulnerability |
| CVE-2024-29056 | Windows Authentication Elevation of Privilege Vulnerability |
| CVE-2024-29061 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-29062 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2024-29064 | Windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-29066 | Windows Distributed File System (DFS) Remote Code Execution Vulnerability |
| CVE-2024-29988 | Internet Shortcut Files Security Feature Bypass Vulnerability |
SQL Server (38 CVEs)
| Important severity | |
| CVE-2024-28906 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28908 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28909 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28910 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28911 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28912 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28913 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28914 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28915 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28926 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28927 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28929 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28930 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28931 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28932 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28933 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28934 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28935 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28936 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28937 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28938 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28939 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28940 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28941 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28942 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28943 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28944 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28945 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29043 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29044 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29045 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29046 | Microsoft WDAC OLE DB Provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29047 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29048 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29982 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29983 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29984 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-29985 | Microsoft OLE DB Driver for SQL Server Remote Code Execution Vulnerability |
Visual Studio (11 CVEs)
| Important severity | |
| CVE-2024-21409 | .NET, .NET Framework, and Visual Studio Remote Code Execution Vulnerability |
| CVE-2024-28929 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28930 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28931 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28932 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28933 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28934 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28935 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28936 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28937 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-28938 | Microsoft ODBC Driver for SQL Server Remote Code Execution Vulnerability |
Azure (9 CVEs)
| Important severity | |
| CVE-2024-21424 | Azure Compute Gallery Elevation of Privilege Vulnerability |
| CVE-2024-26193 | Azure Migrate Remote Code Execution Vulnerability |
| CVE-2024-28917 | Azure Arc-enabled Kubernetes Extension Cluster-Scope Elevation of Privilege Vulnerability |
| CVE-2024-29063 | Azure AI Search Information Disclosure Vulnerability |
| CVE-2024-29989 | Azure Monitor Agent Elevation of Privilege Vulnerability |
| CVE-2024-29990 | Microsoft Azure Kubernetes Service Confidential Container Elevation of Privilege Vulnerability |
| CVE-2024-29993 | Azure CycleCloud Elevation of Privilege Vulnerability |
| Moderate severity | |
| CVE-2024-20685 | Azure Private 5G Core Denial of Service Vulnerability |
| CVE-2024-29992 | Azure Identity Library for .NET Information Disclosure Vulnerability |
Defender (6 CVEs)
| Critical severity | |
| CVE-2024-21322 | Microsoft Defender for IoT Remote Code Execution Vulnerability |
| CVE-2024-21323 | Microsoft Defender for IoT Remote Code Execution Vulnerability |
| CVE-2024-29053 | Microsoft Defender for IoT Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2024-21324 | Microsoft Defender for IoT Elevation of Privilege Vulnerability |
| CVE-2024-29054 | Microsoft Defender for IoT Elevation of Privilege Vulnerability |
| CVE-2024-29055 | Microsoft Defender for IoT Elevation of Privilege Vulnerability |
.NET (1 CVE)
| Important severity | |
| CVE-2024-21409 | .NET, .NET Framework, and Visual Studio Remote Code Execution Vulnerability |
365 (1 CVE)
| Important severity | |
| CVE-2024-26257 | Microsoft Excel Remote Code Execution Vulnerability |
Office (1 CVE)
| Important severity | |
| CVE-2024-26257 | Microsoft Excel Remote Code Execution Vulnerability |
Outlook (1 CVE)
| Important severity | |
| CVE-2024-20670 | Outlook for Windows Spoofing Vulnerability |
SharePoint (1 CVE)
| Important severity | |
| CVE-2024-26251 | Microsoft SharePoint Server Spoofing Vulnerability |
Appendix D: Advisories and Other Products
This is an inventory of advisories and knowledge on different related CVEs within the April Microsoft launch, sorted by product.
Relevant to Edge / Chromium (5 CVEs)
| CVE-2024-3156 | Chromium: CVE-2024-3156 Inappropriate implementation in V8 |
| CVE-2024-3158 | Chromium: CVE-2024-3158 Use after free in Bookmarks |
| CVE-2024-3159 | Chromium: CVE-2024-3159 Out of bounds reminiscence entry in V8 |
| CVE-2024-29049 | Microsoft Edge (Chromium-based) Webview2 Spoofing Vulnerability |
| CVE-2024-29981 | Microsoft Edge (Chromium-based) Spoofing Vulnerability |
Relevant to Windows (non-Microsoft launch) (5 CVEs)
| CVE-2019-3816 | Red Hat: <unnamed CBL Mariner path transversal problem> |
| CVE-2019-3833 | Red Hat: <unnamed CBL Mariner infinite loop problem> |
| CVE-2024-2201 | Intel: CVE-2024-2201 Side Channel Execution |
| CVE-2024-23593 | Lenovo: CVE-2024-23593 Zero Out Boot Manager and drop to UEFI Shell |
| CVE-2024-23594 | Lenovo: CVE-2024-23594 Stack Buffer Overflow in LenovoBT.efi |
Other
| ADV990001 | Latest Servicing Stack Updates |