A brand new information leak that seems to have come from certainly one of China’s high non-public cybersecurity companies gives a uncommon glimpse into the industrial facet of China’s many state-sponsored hacking teams. Experts say the leak illustrates how Chinese authorities businesses more and more are contracting out overseas espionage campaigns to the nation’s burgeoning and extremely aggressive cybersecurity trade.
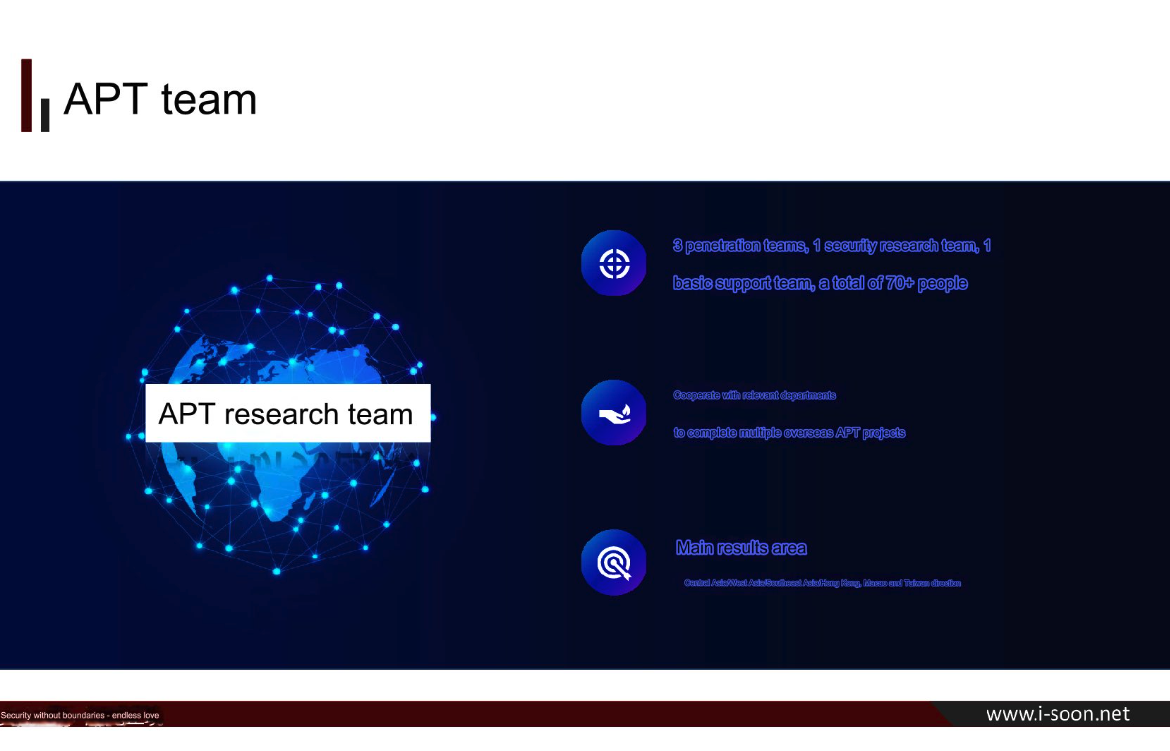
A advertising slide deck selling i-SOON’s Advanced Persistent Threat (APT) capabilities.
A big cache of greater than 500 paperwork revealed to GitHub final week point out the information come from i-SOON, a expertise firm headquartered in Shanghai that’s maybe greatest identified for offering cybersecurity coaching programs all through China. But the leaked paperwork, which embrace candid worker chat conversations and pictures, present a much less public facet of i-SOON, one which continuously initiates and sustains cyberespionage campaigns commissioned by numerous Chinese authorities businesses.
The leaked paperwork counsel i-SOON staff have been chargeable for a raft of cyber intrusions over a few years, infiltrating authorities programs within the United Kingdom and international locations all through Asia. Although the cache doesn’t embrace uncooked information stolen from cyber espionage targets, it options quite a few paperwork itemizing the extent of entry gained and the varieties of information uncovered in every intrusion.
Security consultants who reviewed the leaked information say they consider the knowledge is professional, and that i-SOON works carefully with China’s Ministry of Public Security and the navy. In 2021, the Sichuan provincial authorities named i-SOON as certainly one of “the top 30 information security companies.”
“The leak provides some of the most concrete details seen publicly to date, revealing the maturing nature of China’s cyber espionage ecosystem,” mentioned Dakota Cary, a China-focused advisor on the safety agency SentinelOne. “It shows explicitly how government targeting requirements drive a competitive marketplace of independent contractor hackers-for-hire.”
Mei Danowski is a former intelligence analyst and China skilled who now writes about her analysis in a Substack publication referred to as Natto Thoughts. Danowski mentioned i-SOON has achieved the best secrecy classification {that a} non-state-owned firm can obtain, which qualifies the corporate to conduct labeled analysis and growth associated to state safety.
i-SOON’s “business services” webpage states that the corporate’s choices embrace public safety, anti-fraud, blockchain forensics, enterprise safety options, and coaching. Danowski mentioned that in 2013, i-SOON established a division for analysis on growing new APT community penetration strategies.
APT stands for Advanced Persistent Threat, a time period that usually refers to state-sponsored hacking teams. Indeed, among the many paperwork apparently leaked from i-SOON is a gross sales pitch slide boldly highlighting the hacking prowess of the corporate’s “APT research team” (see screenshot above).

i-SOON CEO Wu Haibo, in 2011. Image: nattothoughts.substack.com.
The leaked paperwork included a prolonged chat dialog between the corporate’s founders, who repeatedly talk about flagging gross sales and the necessity to safe extra staff and authorities contracts. Danowski mentioned the CEO of i-SOON, Wu Haibo (“Shutdown” within the leaked chats) is a widely known first-generation purple hacker or “Honker,” and an early member of Green Army — the very first Chinese hacktivist group based in 1997. Mr. Haibo has not but responded to a request for remark.
In October 2023, Danowski detailed how i-SOON turned embroiled in a software program growth contract dispute when it was sued by a competing Chinese cybersecurity firm referred to as Chengdu 404. In September 2021, the U.S. Department of Justice unsealed indictments in opposition to a number of Chengdu 404 staff, charging that the corporate was a facade that hid greater than a decade’s price of cyber intrusions attributed to a risk actor group often known as “APT 41.”
Danowski mentioned the existence of this authorized dispute means that Chengdu 404 and i-SOON have or at one time had a enterprise relationship, and that one firm doubtless served as a subcontractor to the opposite.
“From what they chat about we can see this is a very competitive industry, where companies in this space are constantly poaching each others’ employees and tools,” Danowski mentioned. “The infosec industry is always trying to distinguish [the work] of one APT group from another. But that’s getting harder to do.”
It stays unclear if i-SOON’s work has earned it a novel APT designation. But Will Thomas, a cyber risk intelligence researcher at Equinix, discovered an Internet deal with within the leaked information that corresponds to a website flagged in a 2019 Citizen Lab report about one-click cell phone exploits that have been getting used to focus on teams in Tibet. The 2019 report referred to the risk actor behind these assaults as an APT group referred to as Poison Carp.
Several photographs and chat information within the information leak counsel i-SOON’s shoppers periodically gave the corporate a listing of targets they wished to infiltrate, however typically staff confused the directions. One screenshot reveals a dialog during which an worker tells his boss they’ve simply hacked one of many universities on their newest listing, solely to be advised that the sufferer in query was not really listed as a desired goal.
The leaked chats present i-SOON constantly tried to recruit new expertise by internet hosting a collection of hacking competitions throughout China. It additionally carried out charity work, and sought to have interaction staff and maintain morale with numerous team-building occasions.
However, the chats embrace a number of conversations between staff commiserating over lengthy hours and low pay. The general tone of the discussions signifies worker morale was fairly low and that the office atmosphere was pretty poisonous. In a number of of the conversations, i-SOON staff brazenly talk about with their bosses how a lot cash they simply misplaced playing on-line with their cellphones whereas at work.
Danowski believes the i-SOON information was most likely leaked by a type of disgruntled staff.
“This was released the first working day after the Chinese New Year,” Danowski mentioned. “Definitely whoever did this planned it, because you can’t get all this information all at once.”
SentinelOne’s Cary mentioned he got here to the identical conclusion, noting that the Protonmail account tied to the GitHub profile that revealed the information was registered a month earlier than the leak, on January 15, 2024.
China’s a lot vaunted Great Firewall not solely lets the federal government management and restrict what residents can entry on-line, however this distributed spying equipment permits authorities to dam information on Chinese residents and firms from ever leaving the nation.
As a outcome, China enjoys a exceptional info asymmetry vis-a-vis nearly all different industrialized nations. Which is why this obvious information leak from i-SOON is such a uncommon discover for Western safety researchers.
“I was so excited to see this,” Cary mentioned. “Every day I hope for data leaks coming out of China.”
That info asymmetry is on the coronary heart of the Chinese authorities’s cyberwarfare objectives, in accordance with a 2023 evaluation by Margin Research carried out on behalf of the Defense Advanced Research Projects Agency (DARPA).
“In the area of cyberwarfare, the western governments see cyberspace as a ‘fifth domain’ of warfare,” the Margin research noticed. “The Chinese, however, look at cyberspace in the broader context of information space. The ultimate objective is, not ‘control’ of cyberspace, but control of information, a vision that dominates China’s cyber operations.”
The National Cybersecurity Strategy issued by the White House final 12 months singles out China as the largest cyber risk to U.S. pursuits. While the United States authorities does contract sure features of its cyber operations to firms within the non-public sector, it doesn’t observe China’s instance in selling the wholesale theft of state and company secrets and techniques for the industrial good thing about its personal non-public industries.
Dave Aitel, a co-author of the Margin Research report and former pc scientist on the U.S. National Security Agency, mentioned it’s good to see that Chinese cybersecurity companies should cope with all the similar contracting complications going through U.S. firms searching for work with the federal authorities.
“This leak just shows there’s layers of contractors all the way down,” Aitel mentioned. “It’s pretty fun to see the Chinese version of it.”
