
Imagine you reside in Russia and need to use the Tor browser to anonymise your searching of the online.
There’s an issue. Many individuals in Russia discover their entry to the official Tor web site is blocked by their ISP.
So, what do you do?
Well, you might attempt to discover someplace aside from the official Tor web site to obtain Tor from.
But is the model of Tor you downloaded from a torrent or third-party website reliable?
According to a report from Russian anti-virus outfit Kaspersky, maybe not.
Kaspersky boffins say that they’ve seen malware distributed as copies of Tor, which has stolen roughly US $400,000 value of cryptocurrency from virtually 16,000 customers worldwide.
According to the researchers, boobytrapped installers provide Tor with a collection of regional language packs, together with Russian.
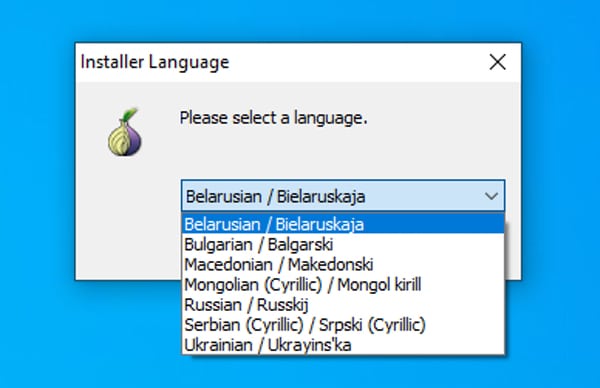
Once put in, the malware snoops in your Windows clipboard.
If it sees in your clipboard what it believes to be an tackle for a cryptocurrency pockets, it replaces it with an tackle controller by the attacker.
The upshot is that you just would possibly assume you’re transferring cryptocurrency into your individual pockets, however in reality you’re placing it into the fingers of a cybercriminal.
Ouch.
I used to be amused to see the crew at Kaspersky counsel a merely technique to examine whether or not you system was compromised:
Type or copy the next “Bitcoin address” in Notepad:
bc1heymalwarehowaboutyoureplacethisaddressNow press Ctrl+C and Ctrl+V. If the tackle modifications to one thing else — the system is probably going compromised by a clipboard-injector sort of malware, and is harmful to make use of.
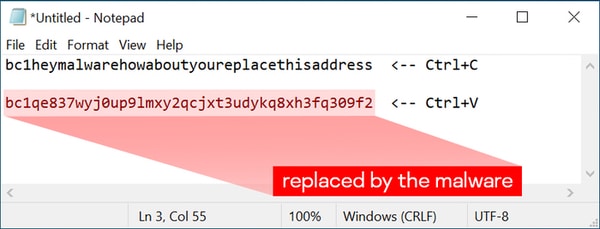
I don’t assume I’d depend on that take a look at alone to inform if my laptop was compromised by the clipboard-injecting malware, nevertheless it’s an attention-grabbing factor to attempt.
If you’re in any doubt, it’s maybe most secure to at all times assume your laptop is compromised.
Found this text attention-grabbing? Follow Graham Cluley on Twitter or Mastodon to learn extra of the unique content material we submit.
