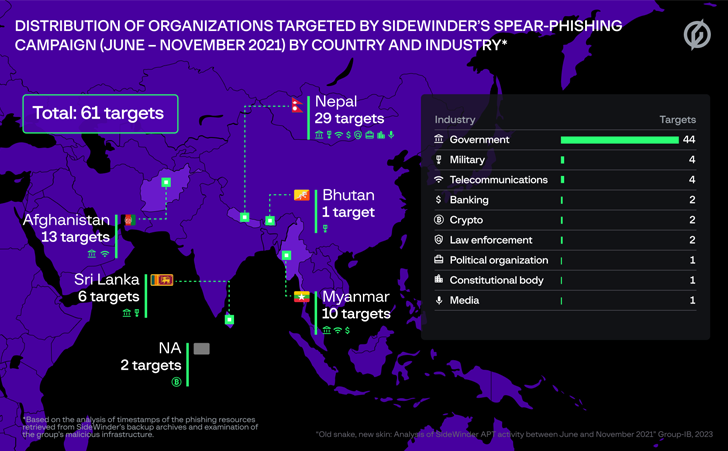
The prolific SideWinder group has been attributed because the nation-state actor behind tried assaults towards 61 entities in Afghanistan, Bhutan, Myanmar, Nepal, and Sri Lanka between June and November 2021.
Targets included authorities, army, legislation enforcement, banks, and different organizations, in line with an exhaustive report revealed by Group-IB, which additionally discovered hyperlinks between the adversary and two different intrusion units tracked as Baby Elephant and DoNot Team.
SideWinder can be known as APT-C-17, Hardcore Nationalist (HN2), Rattlesnake, Razor Tiger, and T-APT4. It’s suspected to be of Indian origin, though Kaspersky in 2022 famous that the attribution is not deterministic.
The group has been linked to at least 1,000 assaults towards authorities organizations within the Asia-Pacific area since April 2020, in line with a report from the Russian cybersecurity agency early final yr.
Of the 61 potential targets compiled by Group-IB, 29 of them are positioned in Nepal, 13 in Afghanistan, 10 in Myanmar, six in Sri Lanka, and one is predicated out of Bhutan.
Typical assault chains mounted by the adversary begin with spear-phishing emails containing an attachment or a booby-trapped URL that directs the victims to an middleman payload that is used to drop the final-stage malware.
SideWinder can be mentioned to have added a slate of latest instruments to its operation, together with a distant entry trojan and an info stealer written in Python that is able to exfiltrating delicate information saved in a sufferer’s pc by way of Telegram.
“Advanced attackers have began preferring Telegram over conventional command and management servers on account of its comfort,” Group-IB mentioned.
The Singapore-headquartered firm additional mentioned it uncovered proof tying the actor to a 2020 assault aimed on the Maldivian authorities, along with establishing infrastructure and tactical overlaps between SideWinder, Baby Elephant, and DoNot Team.
While DoNot Team is thought to have an curiosity in Bangladesh, India, Nepal, Pakistan, and Sri Lanka, Baby Elephant was first documented by Chinese cybersecurity agency Antiy Labs in 2021 as a complicated persistent risk from India focusing on authorities and protection businesses in China and Pakistan.
“Since 2017, the variety of ‘Baby Elephant’ assaults has doubled every year, and the assault strategies and sources have progressively turn out to be richer, and the goal has began to cowl extra areas in South Asia,” the corporate was quoted as saying to Chinese state media outlet Global Times on the time.
Additionally, supply code similarities have been unearthed between SideWinder in addition to these utilized by different teams with a South Asian focus, akin to Transparent Tribe, Patchwork (aka Hangover), and DoNot Team.
“This info means that state-sponsored risk actors are pleased to borrow instruments from each other and modify them for his or her wants,” Group-IB mentioned.
The potential of the risk actor to constantly refine its toolset based mostly on its evolving priorities makes it a very harmful actor working within the espionage space.
“The group clearly has appreciable monetary sources and is most probably state-sponsored, given the truth that SideWinder has been capable of be lively for thus lengthy, develop new instruments, and preserve a pretty big community infrastructure.”