
This weekend, Cloudflare blocked what it describes as the most important volumetric distributed denial-of-service (DDoS) assault thus far.
The firm stated it detected and mitigated not only one however a wave of dozens of hyper-volumetric DDoS assaults concentrating on its clients over the weekend.
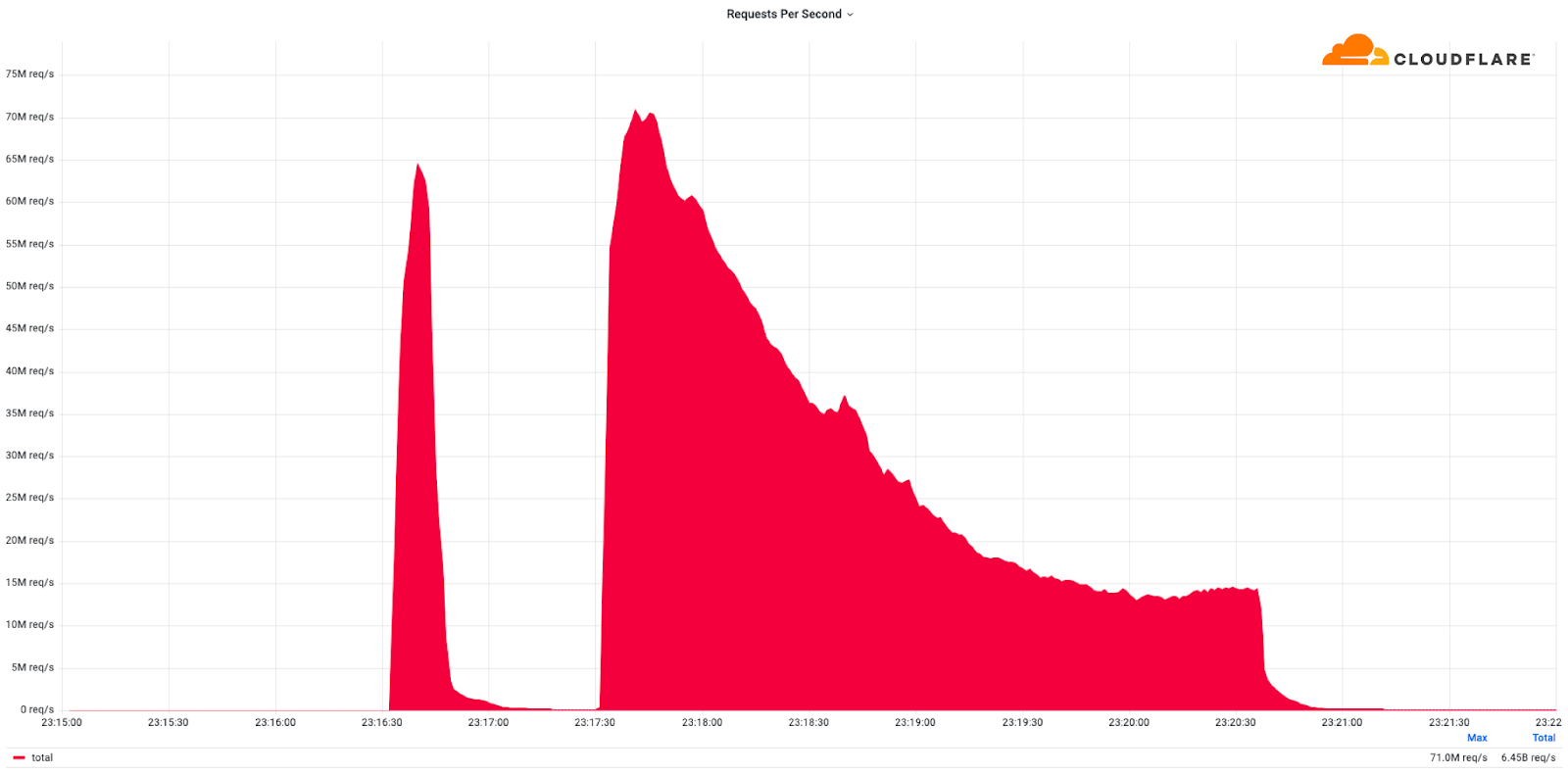
“The majority of assaults peaked within the ballpark of 50-70 million requests per second (rps) with the most important exceeding 71 million rps,” Cloudflare’s Omer Yoachimik, Julien Desgats, and Alex Forster stated.
“This is the most important reported HTTP DDoS assault on document, greater than 35% larger than the earlier reported document of 46M rps in June 2022.”
The assaults had been launched utilizing over 30,000 IP addresses from a number of cloud suppliers towards numerous targets, together with gaming suppliers, cloud computing platforms, cryptocurrency companies, and internet hosting suppliers.
Increasingly highly effective and extra frequent DDoS assaults align with Cloudflare’s current DDoS menace report that paints a grim image:
- the quantity of HTTP DDoS assaults elevated by 79% year-over-year
- the variety of volumetric assaults exceeding 100 Gbps grew by 67% quarter-over-quarter (QoQ)
- the variety of assaults lasting greater than three hours elevated by 87% QoQ
Today’s information comes after Google’s announcement in August 2022 that it blocked a document DDoS assault over the HTTPS protocol towards a Google Cloud Armor buyer that had reached 46 million RPS.
That was a rise of roughly 80% greater than the earlier document, an HTTPS DDoS of 26 million RPS mitigated by Cloudflare in June.
Volumetric DDoS assaults had slowly grown in dimension since 2021 when a number of botnets started leveraging highly effective units to hit targets with tens of millions of requests per second.
For occasion, in September 2021, the Mēris botnet hit Yandex with a 21.8 million RPS assault and beforehand hammered a Cloudflare buyer with 17.2 million RPS.
In response to this stream of ever-increasing assaults, the FBI seized dozens of Internet domains and charged six suspects for his or her involvement in operating ‘Booter’ or ‘Stresser’ platforms that anybody can use to launch DDoS assaults.
The transfer was a part of a extra intensive coordinated worldwide legislation enforcement operation concentrating on DDoS-for-hire companies dubbed Operation PowerOFF.
Besides seizing such platforms’ domains and taking management of their infrastructure (the place doable), the FBI can also be working with the UK’s National Crime Agency and the Netherlands Police to point out advertisements in serps to individuals looking for DDoS companies.
For occasion, when looking for ‘booter service,’ Google would present an commercial stating, “Looking for DDoS instruments? Booting is illegitimate.”
