In the first weblog on this collection, we mentioned organising IAM correctly. Now we’re shifting on to the second step, avoiding direct web entry to AWS assets.
When AWS assets like EC2 situations or S3 buckets are straight accessible by way of the Internet, they’re weak to assault. For instance, brute power assaults on SSH login, denial of service (DOS) assaults on server assets by way of Layer 3, 4, or 7 flooding, or the inadvertent disclosure of knowledge on an S3 bucket. Thankfully, AWS affords instruments that may just about eradicate every of those threats. Let’s focus on the best way to defend assets which have historically been positioned within the demilitarized zone (DMZ) of a public subnet.
Put all EC2 situations in personal subnets
Despite the appearance of community tackle translation (NAT) (i.e., the mapping of a public IP tackle to a non-public IP tackle), many companies put publicly accessible assets within the DMZ. This permits direct connectivity to assets by assigning public IP addresses to them. In flip, by means of area title system (DNS) decision, web site names are translated to those IP addresses which permits connectivity. Ordinarily, assets positioned in a DMZ are webservers. Although some corporations out of comfort, or lack of safety consciousness, may also place database, utility, and file servers within the DMZ. If satisfactory entry management lists (ACLs) and safety teams are usually not in place to limit entry by IP supply, IP vacation spot, protocol, and port quantity, these assets are weak to assault.
Fortunately, there isn’t a longer a necessity to put EC2 situations in a public subnet. This contains bastion hosts which might be used to entry EC2 situations in personal subnets. Rather than affiliate a public IP tackle with EC2 situations, an elastic load balancer (ELB) can be utilized as an alternative.
The ELB is a digital equipment that terminates webserver sure site visitors by way of a public IP tackle and passes that site visitors to EC2 situations or corresponding containers, if relevant, that reside in a public subnet. Neither the AWS buyer utilizing the load balancer, nor any exterior celebration can straight entry the load balancer, so it’s not weak to assault. Furthermore, relying on whether or not the site visitors being terminated on the ELB is Layer 4 (Transport layer of the OSI) or HTTP (Layer 7), AWS affords two separate ELBs to accommodate the relevant site visitors. These ELB choices are Network Load Balancer (Layer 4) and Application Load Balancer (Layer 7). As the diagram and step-by-step description from AWS beneath reveals, virtualized server assets that reside in personal subnets can’t be straight accessed by the surface world.
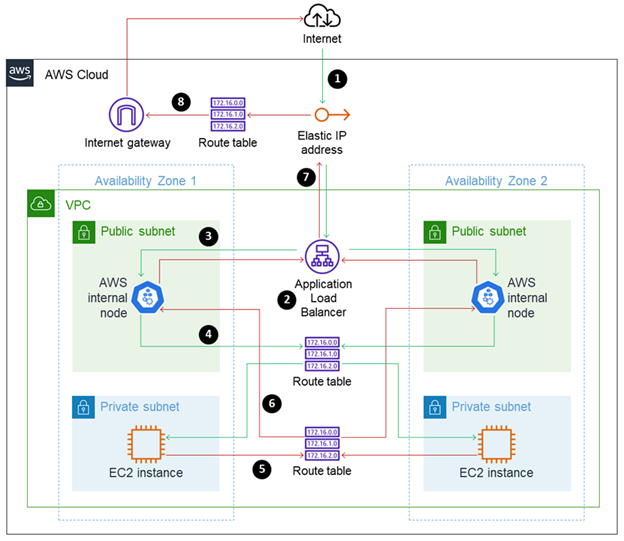
Complete site visitors stream diagram
The following diagram combines the inbound and return site visitors flows to offer an entire illustration of load balancer routing.
- Traffic from the web flows in to the Elastic IP tackle, which is dynamically created once you deploy an internet-facing Application Load Balancer.
- The Application Load Balancer is related to two public subnets within the situation that’s illustrated. The Application Load Balancer makes use of its inside logic to find out which goal group and occasion to route the site visitors to.
- The Application Load Balancer routes the request to the EC2 occasion by means of a node that’s related to the general public subnet in the identical Availability Zone.
- The route desk routes the site visitors regionally throughout the VPC, between the general public subnet and the personal subnet, and to the EC2 occasion.
- The EC2 occasion within the personal subnet routes the outbound site visitors by means of the route desk.
- The route desk has a neighborhood path to the general public subnet. It reaches the Application Load Balancer on the node within the corresponding public subnet, by following the trail again the way in which the site visitors entered.
- The Application Load Balancer routes site visitors out by means of its public Elastic IP tackle.
- The public subnet’s route desk has a default route pointing to an web gateway, which routes the site visitors again out to the web.
Importantly, even with an ELB in place, it’s crucial to configure acceptable ACLs and safety teams. Only legit site visitors needs to be allowed out and in of the digital personal cloud (VPC). If the load balancer improperly permits all site visitors out and in of the personal subnet the place the EC2 situations reside, a lot of the advantage of limiting direct Internet entry to them may be misplaced.
Moreover, EC2 situations behind an ELB can nonetheless be weak to Layer 3, Layer 4, or Layer 7 DoS assaults. An ELB merely eliminates the flexibility for individuals from the Internet to straight entry your situations. To cease Layer 3 and Layer 4 Distributed Denial of Service (DDoS) assaults, AWS affords AWS Shield. This service is obtainable at two ranges – primary and superior. Basic service is free, and it screens and restricts Layer 3 and Layer 4 site visitors. Hence, earlier than site visitors ever hits your ELB, it’s being monitored and filtered with AWS’ DDoS mitigation know-how. For superior protection and options, AWS affords AWS Shield Advanced for an extra value. With Shield Advanced, you’ve got entry to a 24/7 AWS Shield Response Team, superior reporting, and value safety related to the rise of AWS assets used throughout an assault. You can be taught extra about AWS Shield right here: Managed DDoS safety – AWS Shield Features – Amazon Web Services.
For Layer 7 DoS mitigation, AWS affords a Web Application Firewall (WAF). Per AWS, this service “lets you create rules to filter web traffic based on conditions that include IP addresses, HTTP headers and body, or custom URIs… In addition, AWS WAF makes it easy to create rules that block common web exploits like SQL injection and cross site scripting.” If your small business makes use of AWS Shield Advanced, AWS WAF is included within the month-to-month value. You can be taught extra about AWS WAF right here: Features – AWS WAF – Amazon Web Services (AWS).
Notably, some DoS occasions are usually not malicious however are relatively the results of an organization’s net companies going viral. If an excessive amount of site visitors hits abruptly, content material may be inaccessible. For each static and dynamic content material, AWS affords a content material supply community (CDN) known as CloudEntrance. Thus, relatively than scale your EC2 situations behind an ELB vertically or horizontally for elevated demand, content material may be offloaded to CloudEntrance the place it’s cached and, if want be, made globally out there. This protects your virtualized server assets and your pockets, too. You can be taught extra about AWS CloudEntrance right here: Low-Latency Content Delivery Network (CDN) – Amazon CloudEntrance – Amazon Web Services.
How to securely entry EC2 situations in personal subnets
Up up to now, we now have mentioned how one can defend your EC2 situations from being accessed from the surface world. Rightfully so, you might be questioning how techniques directors can entry situations to handle them if there isn’t a public IP tackle for SSH or RDP connectivity? Normally, a bastion host could be provisioned in a public subnet for entry to assets in a non-public subnet. However, by provisioning an EC2 occasion in a public subnet as a bastion host, irrespective of how hardened the occasion is, it’s creating an pointless vulnerability.
The easy treatment to gaining access to EC2 situations in personal subnets is AWS Systems Manager. There isn’t any have to open SSH or RDP ports within the personal subnet both. Through the AWS console, AWS can programmatically set up SSH or RDP entry to EC2 situations. Without SSH or RDP ports open, even when an inside EC2 occasion was compromised, it will not be doable for a malicious actor to capitalize on stolen key pairs to entry an occasion or carry out a brute power assault on the basis account both. Accordingly, the one customers permitted to entry the EC2 occasion, could be these customers with the suitable IAM person, group, or position permissions. To be taught extra about AWS Systems Manager, click on right here: Centralized Operations Hub – AWS Systems Manager – Amazon Web Services.
Finally, you may additionally be questioning how EC2 situations in a non-public subnet can entry the Internet for software program downloads, patches, and upkeep if they don’t have a public IP tackle? Previously, for situations in personal subnets to entry the Internet, an EC2 NAT occasion in a public subnet would should be provisioned. Internet sure site visitors from situations within the personal subnet could be routed by means of the NAT occasion.
However, like bastion hosts, EC2 NAT situations pose pointless safety threat. The resolution to routing Internet based mostly site visitors to and from situations in personal subnets is by utilizing AWS NAT Gateways. Like ELBs, NAT Gateways are virtualized home equipment that aren’t accessible to AWS prospects, or exterior events. Unlike NAT situations, they don’t seem to be provisioned with predefined CPU, RAM, and throughput both. Rather, they scale dynamically to deal with no matter workload is thrown at them. Consequently, EC2 situations in personal subnets can securely entry the Internet with out the risk related to a NAT occasion in a public subnet. To be taught extra about AWS NAT Gateways, click on right here: NAT gateways – Amazon Virtual Private Cloud.
Now that we now have discovered the best way to defend EC2 situations and vicariously the companies that leverage them like containers, purposes, and databases, let’s focus on the best way to safe S3 Buckets.
Keep S3 buckets personal or prohibit public entry utilizing CloudEntrance.
Over the years, many information tales have revealed the blunders of corporations that publicly expose their prospects’ knowledge by publishing it in public S3 buckets. As anybody who has just lately provisioned an S3 bucket will know, AWS has made it exceedingly troublesome to repeat this error. With warning prompts and conspicuous crimson, “danger, Will Robinson!” icons, AWS lets you already know when an S3 Bucket is public.
For apparent causes, knowledge that corporations don’t need the entire world to know ought to by no means be positioned in a public S3 bucket. This contains personally identifiable info (PII), well being info, bank card account particulars, commerce secrets and techniques, and every other proprietary knowledge. Even with encryption in place, which we are going to focus on in Step 3, there isn’t a purpose to ever make such a knowledge publicly out there.
For S3 knowledge that’s publicly out there, direct entry to the objects needs to be restricted. There are a number of the explanation why. First, entities could not need their prospects to entry objects with the AWS S3 URL. Instead, they could need their prospects to entry objects utilizing their customized area. Second, entities could not need their prospects to have limitless entry to S3 objects. Instead, they could favor to make use of pre-signed URLs to restrict how lengthy finish customers can entry objects. Finally, entities could not need to pay pointless prices for finish customers studying or downloading S3 objects straight from a bucket. The treatment to those issues is to make public S3 buckets accessible solely by way of CloudEntrance.
This is achieved by configuring S3 to solely settle for GET or POST requests from CloudEntrance. Hence, objects in a public S3 bucket are inaccessible to the surface world. To be taught extra about AWS CloudEntrance and S3 Bucket integration, click on right here: Restricting entry to an Amazon S3 origin – Amazon CloudEntrance.
Now that we all know the best way to correctly safe EC2 situations and S3 buckets by limiting direct entry by way of the Internet, the following, and final weblog on this collection will focus on our last step – encryption.