Reminiscence security bugs are probably the most quite a few class of Chrome safety points and we’re persevering with to examine many options – each in C++ and in new programming languages. The commonest sort of reminiscence security bug is the “use-after-free”. We lately posted about an thrilling collection of applied sciences designed to stop these. These applied sciences (collectively, *Scan, pronounced “star scan”) are very {powerful} however possible require {hardware} assist for enough efficiency.
At the moment we’re going to speak a couple of completely different method to fixing the identical sort of bugs.
It’s onerous, if not unimaginable, to keep away from use-after-frees in a non-trivial codebase. It’s not often a mistake by a single programmer. As an alternative, one programmer makes cheap assumptions about how a little bit of code will work, then a later change invalidates these assumptions. Out of the blue, the info isn’t legitimate so long as the unique programmer anticipated, and an exploitable bug outcomes.
These bugs have actual penalties. For instance, in keeping with Google Risk Evaluation Group, a use-after-free within the ChromeHTML engine was exploited this yr by North Korea.
Half of the identified exploitable bugs in Chrome are use-after-frees:
Diving Deeper: Not All Use-After-Free Bugs Are Equal
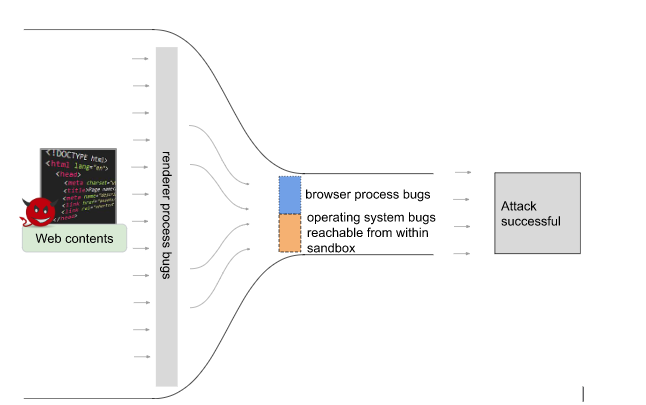
Chrome has a multi-process structure, partly to make sure that net content material is remoted right into a sandboxed “renderer” course of the place little hurt can happen. An attacker due to this fact normally wants to search out and exploit two vulnerabilities – one to attain code execution within the renderer course of, and one other bug to interrupt out of the sandbox.
The primary stage is usually the simpler one. The attacker has numerous affect within the renderer course of. It’s straightforward to rearrange reminiscence in a particular manner, and the renderer course of acts upon many various sorts of net content material, giving a big “assault floor” that would doubtlessly be exploited.
The second stage, escaping the renderer sandbox, is trickier. Attackers have two choices how to do that:
- They will exploit a bug within the underlying working system (OS) by way of the restricted interfaces out there inside Chrome’s sandbox.
- Or, they will exploit a bug in a extra {powerful}, privileged a part of Chrome – just like the “browser” course of. This course of coordinates all the opposite bits of Chrome, so essentially has to be omnipotent.
We think about the attackers squeezing by way of the slender a part of a funnel:
If we are able to scale back the scale of the slender a part of the funnel, we are going to make it as onerous as doable for attackers to assemble a full exploit chain. We are able to scale back the scale of the orange slice by eradicating entry to extra OS interfaces inside the renderer course of sandbox, and we’re constantly engaged on that. The MiraclePtr mission goals to scale back the scale of the blue slice.
Right here’s a pattern of 100 current excessive severity Chrome safety bugs that made it to the secure channel, divided by root trigger and by the method they have an effect on.
You may discover:
- This doesn’t fairly add as much as 100 – that’s as a result of a couple of bugs have been in different processes past the renderer or browser.
- We claimed that the browser course of is the harder half to take advantage of, but there are extra potentially-exploitable bugs! That could be so, however we consider they’re sometimes tougher to take advantage of as a result of the attacker has much less management over reminiscence format.
As you possibly can see, the largest class of bugs in every course of is: V8 within the renderer course of (JavaScript engine logic bugs – work in progress) and use-after-free bugs within the browser course of. If we are able to make that “skinny” bit thinner nonetheless by eradicating a few of these use-after-free bugs, we make the entire job of Chrome exploitation markedly tougher.
MiraclePtr: Stopping Exploitation of Use-After-Free Bugs
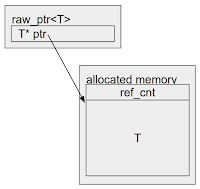
That is the place MiraclePtr is available in. It’s a know-how to stop exploitation of use-after-free bugs. In contrast to aforementioned *Scan applied sciences that provide a non-invasive method to this downside, MiraclePtr depends on rewriting the codebase to make use of a brand new good pointer sort, raw_ptr<T>. There are a number of methods to implement MiraclePtr. We got here up with ~10 algorithms and in contrast the professionals and cons. After analyzing their efficiency overhead, reminiscence overhead, safety safety ensures, developer ergonomics, and many others., we concluded that BackupRefPtr was probably the most promising resolution.
The BackupRefPtr algorithm is predicated on reference counting. It makes use of assist of Chrome’s personal heap allocator, PartitionAlloc, which carves out slightly additional house for a hidden reference depend for every allocation. raw_ptr<T> increments or decrements the reference depend when it’s constructed, destroyed or modified. When the applying calls free/delete and the reference depend is bigger than 0, PartitionAlloc quarantines that reminiscence area as an alternative of instantly releasing it. The reminiscence area is then solely made out there for reuse as soon as the reference depend reaches 0. Quarantined reminiscence is poisoned to additional scale back the chance that use-after-free accesses will lead to exploitable situations, and in hope that future accesses result in an easy-to-debug crash, turning these safety points into less-dangerous ones.
class A { ... };
class B {
B(A* a) : a_(a) {}
void doSomething() { a_->doSomething(); }
raw_ptr<A> a_; // MiraclePtr
};
std::unique_ptr<A> a = std::make_unique<A>();
std::unique_ptr<B> b = std::make_unique<B>(a.get());
[…]
a = nullptr; // The free is delayed as a result of the MiraclePtr continues to be pointing to the thing.
b->doSomething(); // Use-after-free is neutralized.
We efficiently rewrote greater than 15,000 uncooked pointers within the Chrome codebase into raw_ptr<T>, then enabled BackupRefPtr for the browser course of on Home windows and Android (each 64 bit and 32 bit) in Chrome 102 Steady. We anticipate that MiraclePtr meaningfully reduces the browser course of assault floor of Chrome by defending ~50% of use-after-free points towards exploitation. We are actually engaged on enabling BackupRefPtr within the community, utility and GPU processes, and for different platforms. In the long run state, our aim is to allow BackupRefPtr on all platforms as a result of that ensures {that a} given pointer is protected for all customers of Chrome.
Balancing Safety and Efficiency
There is no such thing as a free lunch, nevertheless. This safety safety comes at a price, which we now have rigorously weighed in our determination making.
Unsurprisingly, the primary price is reminiscence. Fortunately, associated investments into PartitionAlloc over the previous yr led to 10-25% complete reminiscence financial savings, relying on utilization patterns and platforms. So we have been capable of spend a few of these financial savings on safety: MiraclePtr elevated the reminiscence utilization of the browser course of 4.5-6.5% on Home windows and three.5-5% on Android1, nonetheless properly beneath their earlier ranges. Whereas we have been frightened about quarantined reminiscence, in observe it is a tiny fraction (0.01%) of the browser course of utilization. By far the larger wrongdoer is the extra reminiscence wanted to retailer the reference depend. One may suppose that including 4 bytes to every allocation wouldn’t be an enormous deal. Nevertheless, there are lots of small allocations in Chrome, so even the 4B overhead will not be negligible. PartitionAlloc additionally makes use of pre-defined bucket sizes, so this additional 4B pushes sure allocations (significantly power-of-2 sized) into a bigger bucket, e.g. 4096B->5120B.
We additionally thought-about the efficiency price. Including an atomic increment/decrement on frequent operations reminiscent of pointer task has unavoidable overhead. Having excluded a lot of performance-critical pointers, we drove this overhead down till we might achieve again the identical margin by way of different efficiency optimizations. On Home windows, no statistically important efficiency regressions have been noticed on most of our top-level efficiency metrics like Largest Contentful Paint, First Enter Delay, and many others. The one adversarial change there1 is a rise of the primary thread rivalry (~7%). On Android1, along with an analogous improve in the primary thread rivalry (~6%), there have been small regressions in First Enter Delay (~1%), Enter Delay (~3%) and First Contentful Paint (~0.5%). We do not anticipate these regressions to have a noticeable influence on consumer expertise, and are assured that they’re strongly outweighed by the extra security for our customers.
We should always emphasize that MiraclePtr at the moment protects solely class/struct pointer fields, to reduce the overhead. As future work, we’re exploring choices to increase the pointer protection to on-stack pointers in order that we are able to defend towards extra use-after-free bugs.
Word that the first aim of MiraclePtr is to stop exploitation of use-after-free bugs. Though it wasn’t designed for diagnosability, it already helped us discover and repair a lot of bugs that have been beforehand undetected. We have now ongoing efforts to make MiraclePtr crash studies much more informative and actionable.
Proceed to Present Us Suggestions
Final however not least, we’d wish to encourage safety researchers to proceed to report points by way of the Chrome Vulnerability Reward Program, even when these points are mitigated by MiraclePtr. We nonetheless have to make MiraclePtr out there to all customers, gather extra knowledge on its influence by way of reported points, and additional refine our processes and tooling. Till that’s executed, we is not going to think about MiraclePtr when figuring out the severity of a bug or the reward quantity.
1 Measured in Chrome 99.