[ad_1]
The elevated use of data expertise in our on a regular basis life and enterprise has led to cyber-attacks changing into extra subtle and large-scale. For organizations to thrive on this period of expertise, they need to develop strong safety methods to detect and mitigate assaults. Defense in depth is a technique during which firms use a number of layers of safety measures to safeguard property. A well-implemented protection in depth can assist organizations forestall and mitigate ongoing assaults.
Defense in depth makes use of varied cutting-edge safety instruments to safeguard a enterprise’s endpoints, information, functions, and networks. The goal is to stop cyber threats, however a strong defense-in-depth strategy additionally thwarts ongoing assaults and prevents additional injury.
How organizations can implement protection in depth
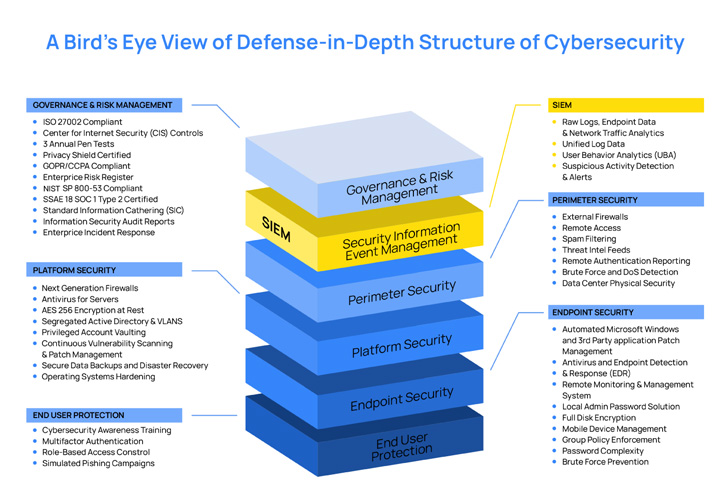 |
| The picture above exhibits the varied layers of safety that organizations should implement. Below we describe concepts that firms ought to take into account for every layer. |
Governance and danger administration
Governance and danger administration in cybersecurity revolves round three main components; governance, danger, and compliance (GRC). The overarching objective of GRC is to make sure that each member of a company works collectively to attain set targets. They should do that whereas adhering to authorized and moral tips, processes, and compliance requirements. Such requirements embrace NIST, PCI-DSS, HIPAA, and GDPR. Establishments should establish the requirements that apply to them and use instruments to automate and simplify the compliance course of. These instruments ought to have the ability to detect violations and supply reviews and easy-to-follow documentation to resolve the violations.
Platform safety
There are some ways organizations can make sure the safety of the gadgets of their enterprise community. Two important strategies are vulnerability administration and working system hardening. Vulnerability administration provides a layer of safety that ensures that firms tackle weaknesses in software program earlier than attackers can exploit them. On the opposite hand, OS hardening ensures that safety groups implement extra measures to guard the integrity of information and configurations utilized in an working system. They can do that by defining and implementing insurance policies for endpoints of their community. Other components to make sure platform safety are firewalls and implementing applicable community segmentation.
SIEM
A safety data and occasion administration (SIEM) answer is crucial to a company’s safety technique. A SIEM aggregates and correlates logs from totally different sources and generates alerts primarily based on detection guidelines. It additionally supplies a central administration portal for triaging and investigating incidents, and with the ability to gather and normalize logs from totally different instruments and methods is among the important options of a very good SIEM.
Perimeter safety (menace intelligence)
Successful implementation of protection in depth shouldn’t be targeted solely on the group’s inner infrastructure but additionally on menace actor actions. Institutions will need to have a method of gathering and analyzing menace intelligence and utilizing the info to supply safety for his or her property. Security groups should additionally use firewalls and community segmentation to guard essential infrastructure.
Endpoint safety
The endpoints in a company are essential to its operations, particularly within the twenty first century. Endpoint safety is significant as a result of attackers often search to compromise information saved on endpoints. Endpoint safety has developed over time from anti-virus options to full-blown antimalware options, and now we’re within the period of prolonged detection and response (XDR) options. XDRs transcend the constraints of conventional antimalware options by correlating alerts from varied sources to supply extra correct detections. They additionally leverage SIEM and SOAR (Security Orchestration, Automation, and Response) functionalities to detect threats in a number of endpoints and reply uniformly and successfully to any compromised endpoints.
Wazuh, the free and open supply answer
Wazuh is a free, open supply safety platform that gives unified SIEM and XDR safety. It protects workloads throughout on-premises, virtualized, containerized, and cloud-based environments. Wazuh supplies assist to safety operations with straightforward integration to menace intelligence feeds.
In implementing protection in depth, no single software can cowl all layers of safety. However, Wazuh gives many options that organizations can use to strengthen their safety infrastructure. For GRC, Wazuh supplies devoted dashboards that monitor and examine occasions triggered by PCI-DSS, HIPAA, and GDPR violations. The answer additionally has a vulnerability detector module with out-of-the-box integration with vulnerability feeds, which scans working methods and functions for identified vulnerabilities.
Wazuh additionally supplies a Security Configuration Assessment (SCA) module that allows customers to create insurance policies that the Wazuh server applies to each endpoint of their surroundings. Companies can use vulnerability detector and SCA modules to strengthen the safety of the working methods and functions deployed on their endpoints.
As an XDR, Wazuh correlates safety information from a number of sources to detect threats in a company’s surroundings. Also, it might probably actively mitigate threats through the use of its lively response functionality.
Wazuh is among the fastest-growing open supply safety options, with over 10 million downloads per yr. Wazuh additionally supplies communities the place customers can interact Wazuh builders, share experiences, and ask questions associated to the platform. Check out this documentation on the way to get began with Wazuh.

