[ad_1]

Image: Shutterstock, iHaMoo.
Adam Griffin continues to be in disbelief over how shortly he was robbed of almost $500,000 in cryptocurrencies. A scammer referred to as utilizing an actual Google telephone quantity to warn his Gmail account was being hacked, despatched e mail safety alerts immediately from google.com, and finally seized management over the account by convincing him to click on “yes” to a Google immediate on his cell gadget.
Griffin is a battalion chief firefighter within the Seattle space, and on May 6 he obtained a name from somebody claiming they had been from Google help saying his account was being accessed from Germany. A Google search on the telephone quantity calling him — (650) 203-0000 — revealed it was an official quantity for Google Assistant, an AI-based service that may interact in two-way conversations.
At the identical time, he obtained an e mail that got here from a google.com e mail deal with, warning his Google account was compromised. The message included a “Google Support Case ID number” and details about the Google consultant supposedly speaking to him on the telephone, stating the rep’s title as “Ashton” — the identical title given by the caller.
Griffin didn’t be taught this till a lot later, however the e mail he obtained had an actual google.com deal with as a result of it was despatched through Google Forms, a service out there to all Google Docs customers that makes it simple to ship surveys, quizzes and different communications.
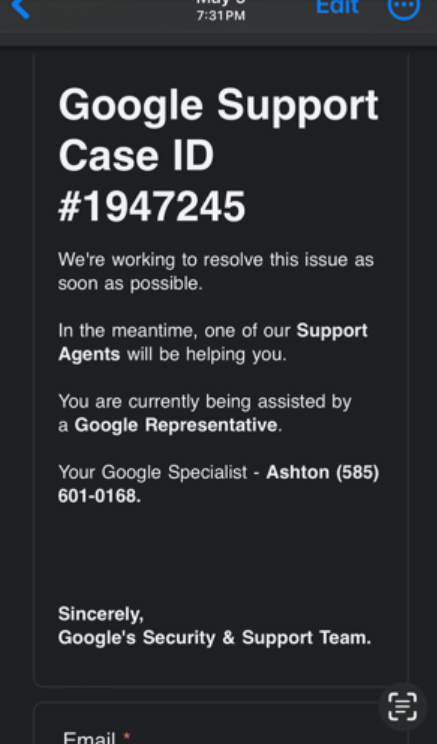
A phony safety alert Griffin obtained previous to his bitcoin heist, through Google Forms.
According to tripwire.com’s Graham Cluely, phishers will use Google Forms to create a safety alert message, after which change the shape’s settings to mechanically ship a duplicate of the finished kind to any e mail deal with entered into the shape. The attacker then sends an invite to finish the shape to themselves, to not their meant sufferer.
“So, the attacker receives the invitation to fill out the form – and when they complete it, they enter their intended victim’s email address into the form, not their own,” Cluely wrote in a December 2023 put up. “The attackers are taking advantage of the fact that the emails are being sent out directly by Google Forms (from the google.com domain). It’s an established legitimate domain that helps to make the email look more legitimate and is less likely to be intercepted en route by email-filtering solutions.”
The faux Google consultant was well mannered, affected person, skilled and reassuring. Ashton advised Griffin he was going to obtain a notification that may enable him to regain management of the account from the hackers. Sure sufficient, a Google immediate immediately appeared on his telephone asking, “Is it you trying to recover your account?”
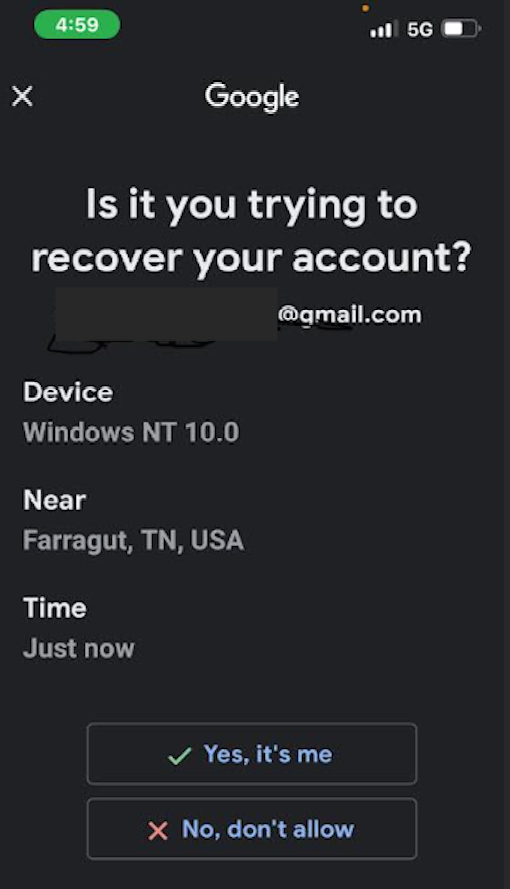
Adam Griffin clicked “yes,” to an account restoration notification just like this one on May 6.
Griffin mentioned that after receiving the pop-up immediate from Google on his telephone, he felt extra comfortable that he actually was speaking to somebody at Google. In actuality, the thieves precipitated the alert to seem on his telephone merely by stepping by means of Google’s account restoration course of for Griffin’s Gmail deal with.
“As soon as I clicked yes, I gave them access to my Gmail, which was synched to Google Photos,” Griffin mentioned.
Unfortunately for Griffin, years in the past he used Google Photos to retailer a picture of the key seed phrase that was defending his cryptocurrency pockets. Armed with that phrase, the phishers may drain all of his funds.
“From there they were able to transfer approximately $450,000 out of my Exodus wallet,” Griffin recalled.
Griffin mentioned simply minutes after giving freely entry to his Gmail account he obtained a name from somebody claiming to be with Coinbase, who likewise advised him somebody in Germany was making an attempt to take over his account.
Griffin mentioned a follow-up investigation revealed the attackers had used his Gmail account to achieve entry to his Coinbase account from a VPN connection in California, offering the multi-factor code from his Google Authenticator app. Unbeknownst to him on the time, Google Authenticator by default additionally makes the identical codes out there in a single’s Google account on-line.
But when the thieves tried to maneuver $100,000 value of cryptocurrency out of his account, Coinbase despatched an e mail stating that the account had been locked, and that he must submit further verification paperwork earlier than he may do something with it.
GRAND THEFT AUTOMATED
Just days after Griffin was robbed, a scammer impersonating Google managed to phish 45 bitcoins — roughly $4,725,000 at at present’s worth — from Tony, a 42-year-old skilled from northern California. Tony agreed to discuss his harrowing expertise provided that his final title not be used.
Tony bought into bitcoin again in 2013 and has been investing in it ever since. On the night of May 15, 2024, Tony was placing his three- and one-year-old boys to mattress when he obtained a message from Google about an account safety difficulty, adopted by a telephone name from a “Daniel Alexander” at Google who mentioned his account was compromised by hackers.
Tony mentioned he had simply signed up for Google’s Gemini AI (a man-made intelligence platform previously referred to as “Bard”), and mistakenly believed the decision was a part of that service. Daniel advised Tony his account was being accessed by somebody in Frankfurt, Germany, and that he may evict the hacker and get better entry to the account by clicking “yes” to the immediate that Google was going to ship to his telephone.
The Google immediate arrived seconds later. And to his eternal remorse, Tony clicked the “Yes, it’s me” button.
Then got here one other name, this one allegedly from safety personnel at Trezor, an organization that makes encrypted {hardware} gadgets made to retailer cryptocurrency seed phrases securely offline. The caller mentioned somebody had submitted a request to Trezor to shut his account, they usually forwarded Tony a message despatched from his Gmail account that included his title, Social Security quantity, date of delivery, deal with, telephone quantity and e mail deal with.
Tony mentioned he started to consider then that his Trezor account really was compromised. The caller satisfied him to “recover” his account by coming into his cryptocurrency seed phrase at a phishing web site (verify-trezor[.]io) that mimicked the official Trezor web site.
“At this point I go into fight or flight mode,” Tony recalled. “I’ve got my kids crying, my wife is like what the heck is going on? My brain went haywire. I put my seed phrase into a phishing site, and that was it.”
Almost instantly, all the funds he was planning to save lots of for retirement and for his youngsters’s school fund had been drained from his account.
“I made mistakes due to being so busy and not thinking correctly,” Tony advised KrebsOnSecurity. “I had gotten so far away from the security protocols in bitcoin as life had changed so much since having kids.”
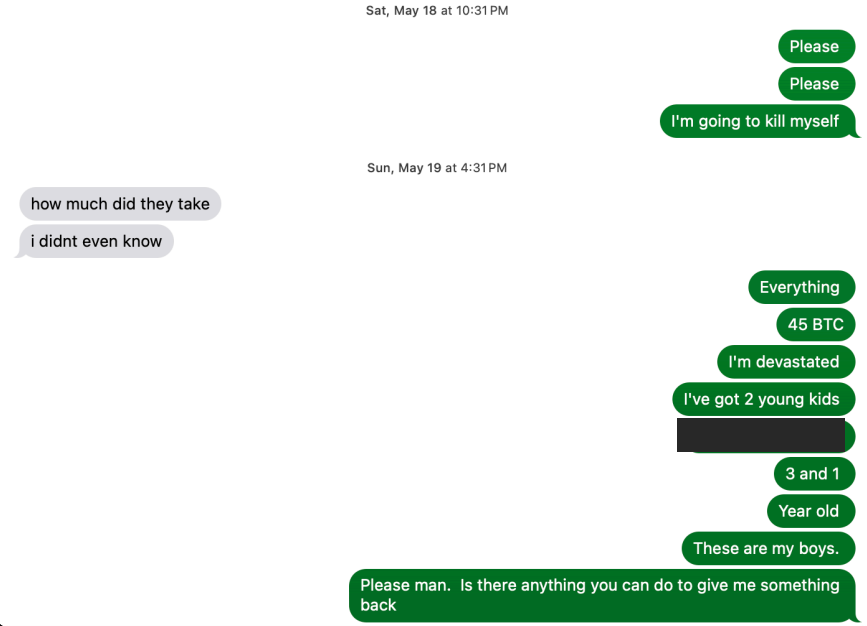
Tony shared this textual content message change of him pleading together with his tormentors after being robbed of 45 bitcoins.
Tony mentioned the theft left him traumatized and indignant for months.
“All I was thinking about was protecting my boys and it ended up costing me everything,” he mentioned. “Needless to say I’m devastated and have had to do serious therapy to get through it.”
MISERY LOVES COMPANY
Tony advised KrebsOnSecurity that within the weeks following the theft of his 45 bitcoins, he turned so consumed with rage and disgrace that he was critically considering suicide. Then sooner or later, whereas scouring the Internet for indicators that others might have been phished by Daniel, he encountered Griffin posting on Reddit concerning the telephone quantity concerned in his latest bitcoin theft.
Griffin mentioned the 2 of them had been initially suspicious of one another — exchanging cautious messages for a couple of week — however he determined Tony was telling the reality after contacting the FBI agent that Tony mentioned was working his case. Comparing notes, they found the faux Google safety alerts they obtained simply previous to their particular person bitcoin thefts referenced the identical phony “Google Support Case ID” quantity.
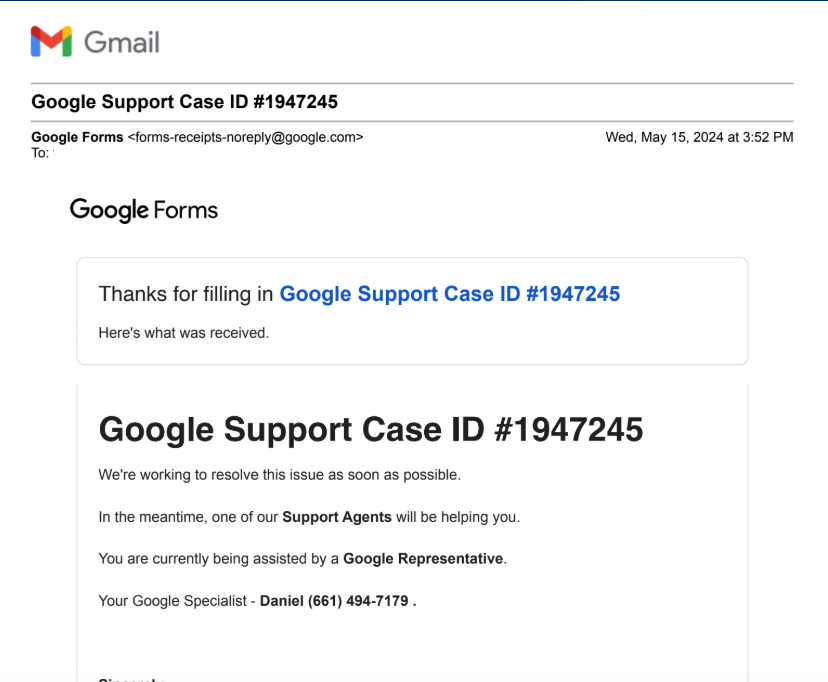
Adam Griffin and Tony mentioned they obtained the identical Google Support Case ID quantity upfront of their thefts. Both had been despatched through Google Forms, which sends immediately from the google.com area title.
More importantly, Tony acknowledged the voice of “Daniel from Google” when it was featured in an interview by Junseth, a podcaster who covers cryptocurrency scams. The identical voice that had coaxed Tony out of his appreciable cryptocurrency holdings simply days earlier additionally had tried to phish Junseth, who performed alongside for a number of minutes earlier than revealing he knew it was a rip-off.
Daniel advised Junseth he was an adolescent and labored with different rip-off callers who had all met years in the past on the sport Minecraft, and that he lately loved a run of back-to-back Gmail account compromises that led to crypto theft paydays.
“No one gets arrested,” Daniel enthused to Junseth within the May 7 podcast, which shortly went viral on social media. “It’s almost like there’s no consequences. I have small legal side hustles, like businesses and shit that I can funnel everything through. If you were to see me in real life, I look like a regular child going to school with my backpack and shit, you’d never expect this kid is stealing all this shit.”
Daniel defined that they typically use an automatic bot that initiates calls to targets warning that their account is experiencing suspicious exercise, and that they need to press “1” to talk with a consultant. This course of, he defined, primarily self-selects people who find themselves extra more likely to be vulnerable to their social engineering schemes. [It is possible — but not certain — that this bot Daniel referenced explains the incoming call to Griffin from Google Assistant that precipitated his bitcoin heist].
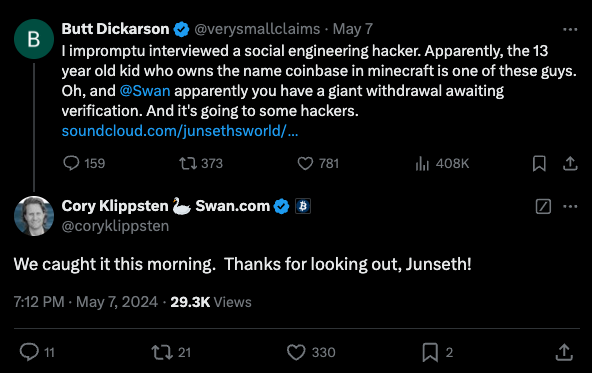
Daniel advised Junseth he and his co-conspirators had simply scored a $1.2 million theft that was nonetheless pending on the bitcoin funding platform SwanBitcoin. In response, Junseth tagged SwanBitcoin in a put up about his podcast on Twitter/X, and the CEO of Swan shortly replied that they caught the $1.2 million transaction that morning.
Apparently, Daniel didn’t admire having his voice broadcast to the world (or his $1.2 million bitcoin heist disrupted) as a result of in line with Junseth somebody submitted a baseless copyright infringement declare about it to Soundcloud, which was internet hosting the recording.
The grievance alleged the recording included a copyrighted track, however that wasn’t true: Junseth later posted a uncooked model of the recording to Telegram, and it clearly had no music within the background. Nevertheless, Soundcloud eliminated the audio file.
“All these companies are very afraid of copyright,” Junseth defined in a May 2024 interview with the podcast whatbitcoindid.com, which options a number of the highlights from his recorded name with Daniel.
“It’s interesting because copyright infringement really is an act that you’re claiming against the publisher, but for some reason these companies have taken a very hard line against it, so if you even claim there’s copyrighted material in it they just take it down and then they leave it to you to prove that you’re innocent,” Junseth mentioned. “In Soundcloud’s instance, part of declaring your innocence is you have to give them your home address and everything else, and it says right on there, ‘this will be provided to the person making the copyright claim.’”
AFTERMATH
When Junseth requested how potential victims may shield themselves, Daniel defined that if the goal doesn’t have their Google Authenticator synced to their Google cloud account, the scammers can’t simply pivot into the sufferer’s accounts at cryptocurrency exchanges, as they did with Griffin.
By default, Google Authenticator syncs all one-time codes with a Gmail consumer’s account, that means if somebody positive aspects entry to your Google account, they will then entry all the one-time codes handed out by your Google Authenticator app.
To change this setting, open Authenticator in your cell gadget, choose your profile image, after which select “Use without an Account” from the menu. If you disable this, it’s a good suggestion to maintain a printed copy of one-time backup codes, and to retailer these in a safe place.
You may additionally want to obtain Google Authenticator to a different cell gadget that you simply management. Otherwise, in case you flip off cloud synching and lose that sole cell gadget together with your Google Authenticator app, it could possibly be troublesome or unimaginable to get better entry to your account in case you someway get locked out.
Griffin advised KrebsOnSecurity he had no thought it was really easy for thieves to take over his account, and to abuse so many alternative Google companies within the course of.
“I know I definitely made mistakes, but I also know Google could do a lot better job protecting people,” he mentioned.
In response to questions from KrebsOnSecurity, Google mentioned it could possibly affirm that this was a slender phishing marketing campaign, reaching a “very small group of people.”
“We’re aware of this narrow and targeted attack, and have hardened our defenses to block recovery attempts from this actor,” the corporate mentioned in a written assertion, which emphasised that the actual Google won’t ever name you.
“While these types of social engineering campaigns are constantly evolving, we are continuously working to harden our systems with new tools and technical innovations, as well as sharing updated guidance with our users to stay ahead of attackers,” the assertion reads.
Both Griffin and Tony say they proceed to obtain “account security” calls from folks pretending to work for Google or one of many cryptocurrency platforms.
“It’s like you get put on some kind of list, and then those lists get recycled over and over,” Tony mentioned.
Griffin mentioned that for a number of months after his ordeal, he accepted virtually each cryptocurrency rip-off name that got here his manner, enjoying alongside within the useless hope of someway tricking the caller into revealing particulars about who they’re in actual life. But he stopped after his taunting precipitated one of many scammers to start out threatening him personally.
“I probably shouldn’t have, but I recorded two 30-minute conversations with these guys,” Griffin mentioned, acknowledging that perhaps it wasn’t such an ideal thought to antagonize cybercriminals who clearly already knew every part about him. “One guy I talked to about his personal life, and then his friend called me up and said he was going to dox me and do all this other bad stuff. My FBI contact later told me not to talk to these guys anymore.”
Sound recommendation. So is hanging up each time anybody calls you a couple of safety downside with one in every of your accounts. Even security-conscious folks are likely to underestimate the complicated and shifting menace from phone-based phishing scams, however they achieve this at their peril.
When unsure: Hang up, lookup, and name again. If your response to these kinds of calls entails something apart from hanging up, researching the right telephone quantity, and contacting the entity that claims to be calling, you could be setting your self up for a expensive and humbling studying expertise.
Understand that your e mail credentials are greater than probably the important thing to unlocking your complete digital id. Be positive to make use of an extended, distinctive passphrase on your e mail deal with, and by no means decide a passphrase that you’ve ever used wherever else (not even a variation on an outdated password).
Finally, it’s additionally a good suggestion to make the most of the strongest multi-factor authentication strategies supplied. For Gmail/Google accounts, that features the usage of passkeys or bodily safety keys, that are closely phishing resistant. For Google customers holding measurable sums of cryptocurrency, essentially the most safe possibility is Google’s free Advanced Protection program, which incorporates extra intensive account security measures but in addition comes with some severe comfort trade-offs.
[ad_2]
