[ad_1]
Unknown malware presents a big cybersecurity menace and may trigger critical injury to organizations and people alike. When left undetected, malicious code can acquire entry to confidential info, corrupt knowledge, and permit attackers to realize management of techniques. Find out how you can keep away from these circumstances and detect unknown malicious conduct effectively.
Challenges of recent threats’ detection
While identified malware households are extra predictable and will be detected extra simply, unknown threats can tackle quite a lot of kinds, inflicting a bunch of challenges for his or her detection:
- Malware builders use polymorphism, which allows them to switch the malicious code to generate distinctive variants of the identical malware.
- There is malware that’s nonetheless not recognized and would not have any rulesets for detection.
- Some threats will be Fully UnDetectin a position (FUD) for a while and problem perimeter safety.
- The code is commonly encrypted, making it troublesome to detect by signature-based safety options.
- Malware authors might use a “low and gradual” method, which includes sending a small quantity of malicious code throughout a community over a very long time, which makes it tougher to detect and block. This will be particularly damaging in company networks, the place the shortage of visibility into the atmosphere can result in undetected malicious exercise.
Detection of recent threats
When analyzing identified malware households, researchers can make the most of present details about the malware, resembling its conduct, payloads, and identified vulnerabilities, as a way to detect and reply to it.
But coping with new threats, researchers have to begin from scratch, utilizing the next information:
Step 1. Use reverse engineering to research the code of the malware to determine its function and malicious nature.
Step 2. Use static evaluation to look at the malware’s code to determine its conduct, payloads, and vulnerabilities.
Step 3. Use dynamic evaluation to look at the conduct of the malware throughout execution.
Step 4. Use sandboxing to run the malware in an remoted atmosphere to look at its conduct with out harming the system.
Step 5. Use heuristics to determine probably malicious code primarily based on observable patterns and behaviors.
Step 6. Analyze the outcomes of reverse engineering, static evaluation, dynamic evaluation, sandboxing, and heuristics to find out if the code is malicious.
There are loads of instruments from Process Monitor and Wireshark to ANY.RUN that can assist you undergo the primary 5 steps. But how to attract a exact conclusion, what must you take note of whereas having all this knowledge?
The reply is easy – concentrate on indicators of malicious conduct.
Monitor suspicious actions for efficient detection
Different signatures are used to detect threats. In laptop safety terminology, a signature is a typical footprint or sample related to a malicious assault on a pc community or system.
Part of those signatures is behavioral ones. It’s not possible to do one thing within the OS and depart no tracing behind. We can determine what software program or script it was by way of their suspicious actions.
You can run a suspicious program in a sandbox to look at the conduct of the malware and determine any malicious conduct, resembling:
- irregular file system exercise,
- suspicious course of creation and termination
- irregular networking exercise
- studying or modifying system recordsdata
- entry system assets
- create new customers
- connect with distant servers
- execute different malicious instructions
- exploit identified vulnerabilities within the system
Microsoft Office is launching PowerShell – seems suspicious, proper? An utility provides itself to the scheduled duties – undoubtedly take note of it. A svchost course of runs from the temp registry – one thing is certainly improper.
You can at all times detect any menace by its conduct, even with out signatures.
Let’s show it.
Use case #1
Here is a pattern of the stealer. What does it do? Steals person knowledge, cookies, wallets, and so on. How can we detect it? For instance, it reveals itself when the appliance opens the Chrome browser’s Login Data file.
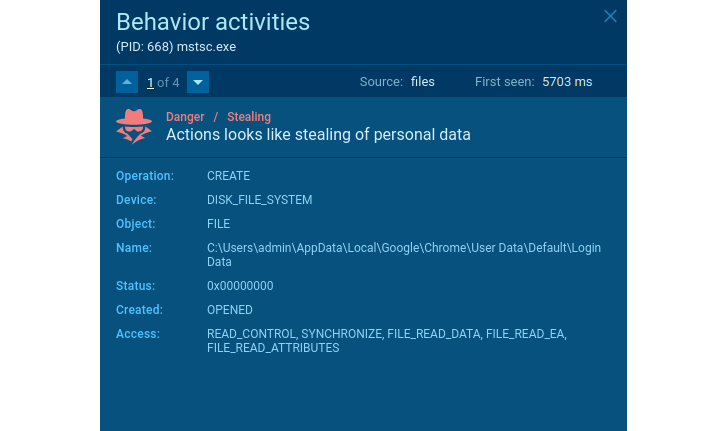 |
| Stealer’s suspicious conduct |
The exercise within the community site visitors additionally broadcasts the menace’s malicious intentions. A legit utility would by no means ship credentials, OS traits, and different delicate knowledge collected domestically.
In the case of site visitors, malware will be detected by well-known options. Agent Tesla in some instances doesn’t encrypt knowledge despatched from an contaminated system like on this pattern.
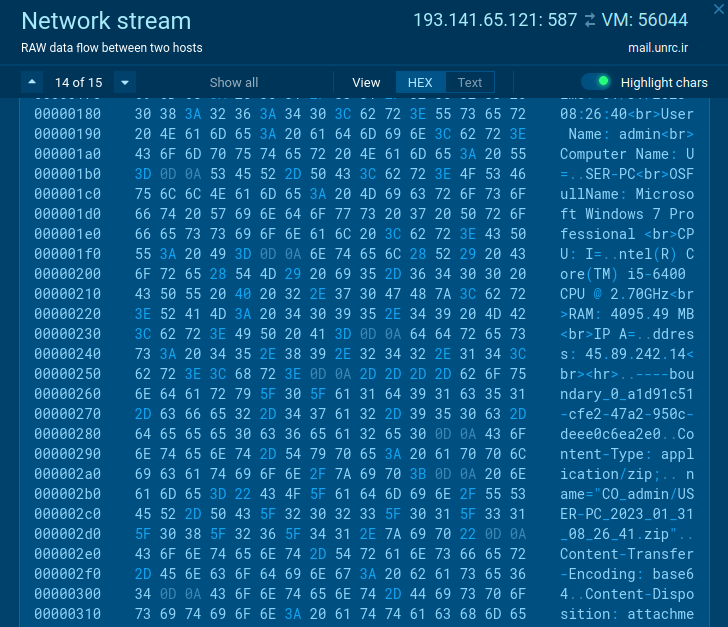 |
| Suspicious exercise within the community site visitors |
Use case #2
There aren’t many legit packages that have to cease Windows Defender or different functions to guard the OS or make an exclusion for itself. Every time you encounter this type of conduct – that is an indication of suspicious exercise.
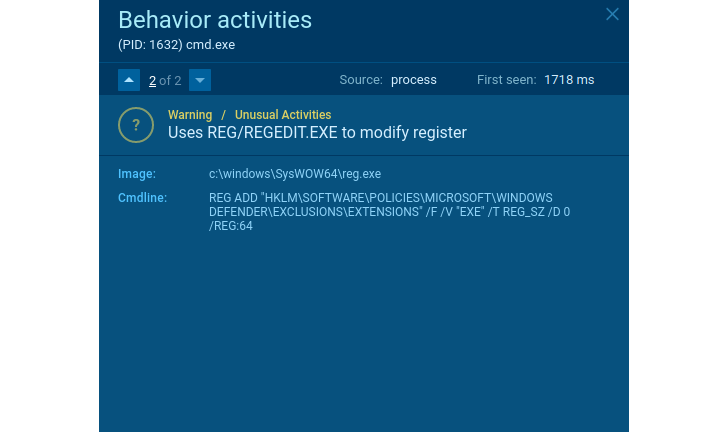 |
| Suspicious conduct |
Does the appliance delete shadow copies? Looks like ransomware. Does it take away shadow copies and create a TXT/HTML file with readme textual content in every listing? It’s yet one more proof of it.
If the person knowledge is encrypted within the course of, we will be positive it’s ransomware. Like what occurred on this malicious instance. Even if we have no idea the household, we are able to determine what sort of safety menace this software program poses after which act accordingly and take measures to guard working stations and the group’s community.
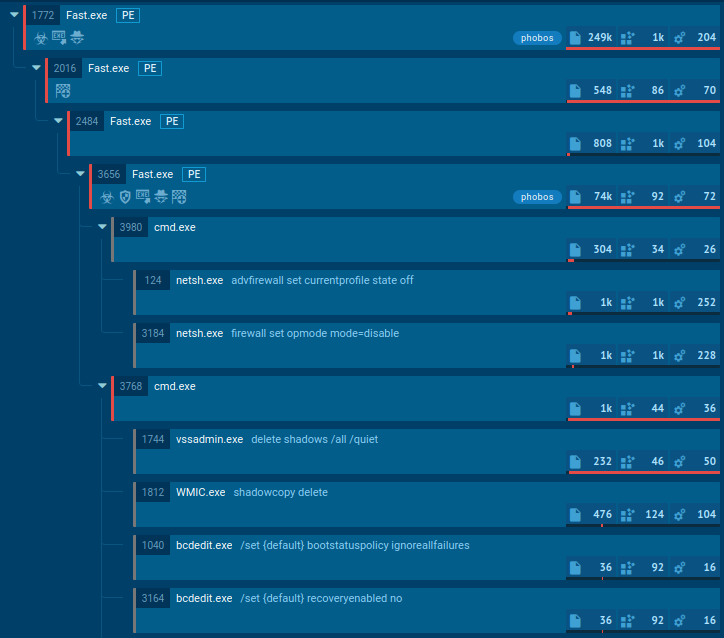 |
| Ransomware suspicious conduct |
We can draw conclusions about virtually every kind of malware primarily based on the conduct noticed within the sandbox. Try ANY.RUN on-line interactive service to watch it – you will get the primary outcomes instantly and see all malware’s motion in actual time. Exactly what we have to catch any suspicious actions.
Write the “HACKERNEWS2” promo code at help@any.run utilizing your enterprise e-mail tackle and get 14 days of ANY.RUN premium subscription free of charge!
Wrapping up
Cybercriminals can use unknown threats to extort companies for cash and launch large-scale cyberattacks. Even if the malware household will not be detected – we are able to at all times conclude the menace’s performance by contemplating its conduct. Using this knowledge, you possibly can construct info safety to forestall any new threats. Behavior evaluation enhances your means to reply to new and unknown threats and strengthens your group’s safety with out extra prices.

