[ad_1]
A password supervisor can preserve your delicate info in-house. Here’s how one can deploy Passbolt to your information heart or cloud-hosted service.

Passbolt is a password supervisor you should utilize for crew collaboration, and it affords loads of the options you’ve grown accustomed to having at your fingertips, reminiscent of a random password generator, crew collaboration, folders, tags and consumer entry management. This password supervisor is designed particularly for Agile and DevOps groups, and it’s software programming interface-centric and developer-first.
Why would you need to run a self-hosted occasion of Passbolt?
If your venture or group wants to save lots of delicate info and also you don’t need to belief it to third-party servers, you would possibly need to run a self-hosted occasion of Passbolt. If you’re snug utilizing Docker, it is a surefire answer for safeguarding your passwords from breaches, reminiscent of what lately occurred to LastPass.
SEE: Password breach: Why popular culture and passwords don’t combine (free PDF) (TechRepublic)
If Passbolt appears like a password supervisor well-suited to your wants, learn the way it may be deployed with the assistance of Docker.
What you’ll have to deploy Passbolt
To run the self-hosted model of Passbolt, you’ll want a server with an working system that helps Docker. I’ll exhibit with Ubuntu Server 22.04 and the newest model of Docker CE; for that, you’ll want a working occasion of Ubuntu Server and a consumer with sudo privileges.
How to put in Docker
First, add the official Docker GPG key with the command:
curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo gpg --dearmor -o /usr/share/keyrings/docker-archive-keyring.gpg
With the important thing in place, add the Docker repository with the command:
echo "deb [arch=amd64 signed-by=/usr/share/keyrings/docker-archive-keyring.gpg] https://download.docker.com/linux/ubuntu $(lsb_release -cs) steady" | sudo tee /and so on/apt/sources.checklist.d/docker.checklist > /dev/null
Next, set up the required dependencies with the command:
sudo apt-get set up apt-transport-https ca-certificates curl gnupg lsb-release -y
Update apt, and set up Docker CE with the instructions:
sudo apt-get replacesudo apt-get set up docker-ce docker-ce-cli containerd.io -y
Make certain your consumer remains to be a member of the docker group with the command:
sudo usermod -aG docker $USER
Log out and log again in for the adjustments to take impact.
Download the Passbolt Docker Compose YAML file with:
wget https://download.passbolt.com/ce/docker/docker-compose-ce.yaml
Open that file for modifying with the command:
nano docker-compose-ce.yaml
Go via that file and edit any entries you want. For instance, you would possibly change the APP_FULL_BASE_URL: line to mirror your server’s IP handle or hostname. Once you’ve edited the file, save and shut it. You can then begin the containers with the command:
docker-compose -f docker-compose-ce.yaml up -d
Once the containers have began, you should then create your first admin consumer with the command:
docker-compose -f docker-compose-ce.yaml exec passbolt su -m -c "/usr/share/php/passbolt/bin/cake passbolt register_user -u EMAIL -f FIRSTNAME -l LASTNAME -r admin" -s /bin/sh www-data
Where:
- EMAIL is your e mail handle.
- FIRSTNAME is your first title.
- LASTNAME is your final title.
The above command will output an handle like this:
https://192.168.1.60/setup/install/f398345d-3bee-897d-afe5-321ea3dd3a5b/724fe653-80d7-4042-8667-ea61ddd104c6
Open your default net browser, which have to be both Firefox, Chrome, Edge, Brave or Vivaldi, paste the output handle and hit enter. Now, you’ll be able to create a passphrase to your vault (Figure A), ensuring it’s robust and distinctive.
Figure A
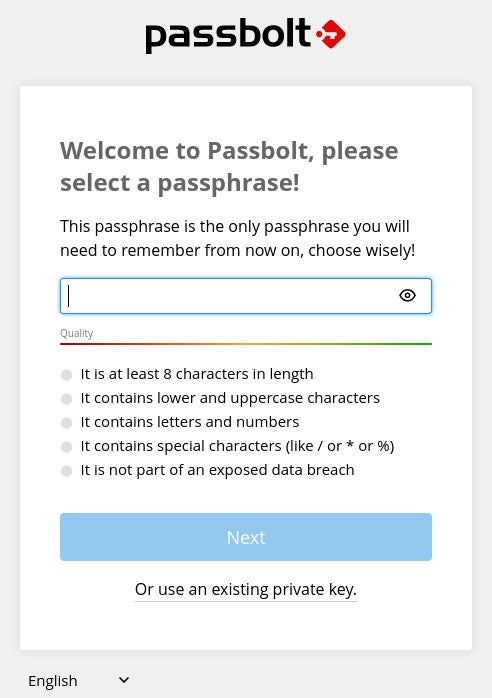
Click Next, save the restoration equipment file to your native drive and click on Next once more. You will likely be required to select a coloration and kind three random characters (Figure B).
Figure B
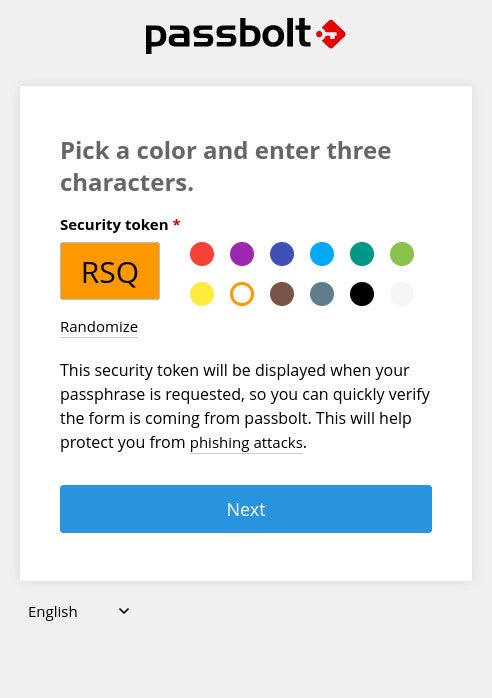
Click Next, and also you’ll end up on the Passbolt predominant window (Figure C), the place you can begin including vault entries.
Figure C

Another safety useful resource to make use of is TechRepublic Premium’s password administration coverage.
Subscribe to TechRepublic’s How To Make Tech Work on YouTube for all the newest tech recommendation for enterprise professionals from Jack Wallen.
