[ad_1]
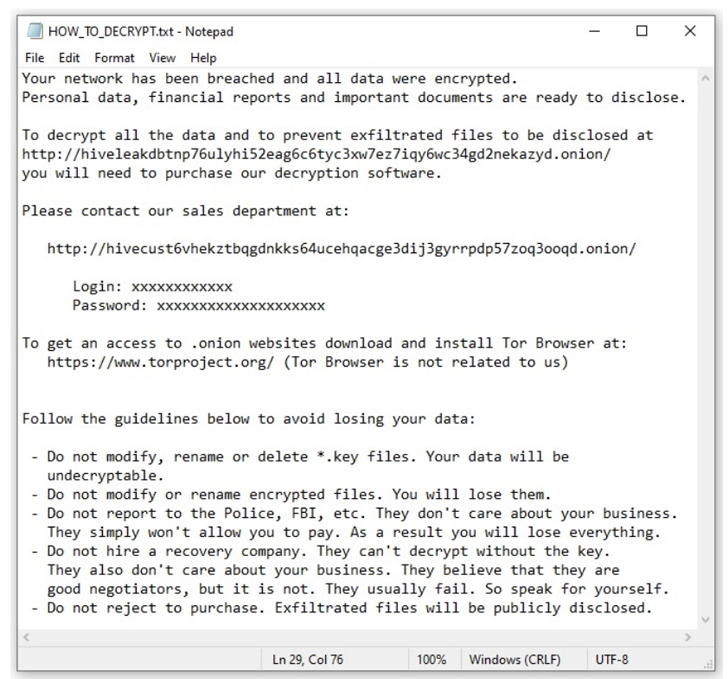
The risk actors behind the Hive ransomware-as-a-service (RaaS) scheme have launched assaults in opposition to over 1,300 corporations the world over, netting the gang $100 million in illicit funds as of November 2022.
“Hive ransomware has focused a variety of companies and demanding infrastructure sectors, together with authorities services, communications, vital manufacturing, data know-how, and — particularly — Healthcare and Public Health (HPH),” U.S. cybersecurity and intelligence authorities stated in an alert.
Active since June 2021, Hive’s RaaS operation includes a mixture of builders, who create and handle the malware, and associates, who’re liable for conducting the assaults on track networks by typically buying preliminary entry from preliminary entry brokers (IABs).
In most circumstances, gaining a foothold includes the exploitation of ProxyShell flaws in Microsoft Exchange Server, adopted by taking steps to terminate processes related to antivirus engines and information backups in addition to delete Windows occasion logs.
The risk actor, which not too long ago upgraded its malware to Rust as a detection evasion measure, can be recognized to take away virus definitions previous to encryption.
“Hive actors have been recognized to reinfect — with both Hive ransomware or one other ransomware variant — the networks of sufferer organizations who’ve restored their community with out making a ransom cost,” the U.S. Cybersecurity and Infrastructure Security Agency (CISA) stated.
According to information shared by cybersecurity firm Malwarebytes, Hive compromised about seven victims in August 2022, 14 in September, and two different entities in October, marking a drop in exercise from July, when the group focused 26 victims.