[ad_1]
Threat actors are capitalizing on a well-liked TikTok problem to trick customers into downloading information-stealing malware, in accordance with new analysis from Checkmarx.
The pattern, known as Invisible Challenge, entails making use of a filter referred to as Invisible Body that simply leaves behind a silhouette of the individual’s physique.
But the truth that people filming such movies could possibly be undressed has led to a nefarious scheme whereby the attackers publish TikTok movies with hyperlinks to rogue software program dubbed “unfilter” that purport to take away the utilized filters.
“Instructions to get the ‘unfilter’ software program deploy WASP stealer malware hiding inside malicious Python packages,” Checkmarx researcher Guy Nachshon mentioned in a Monday evaluation.
The WASP stealer (aka W4SP Stealer) is a malware that is designed to steal customers’ passwords, Discord accounts, cryptocurrency wallets, and different delicate info.
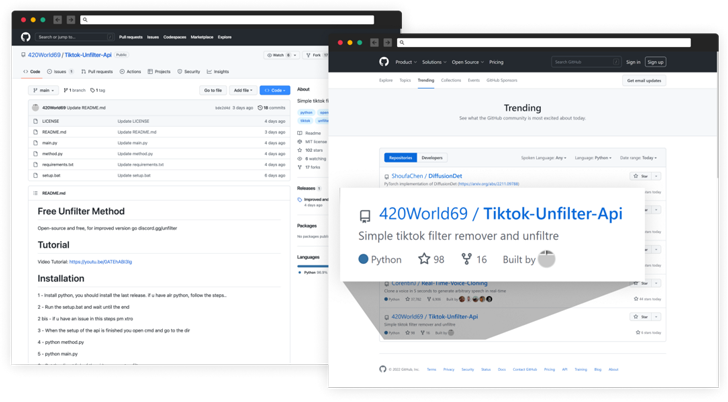
The TikTok movies posted by the attackers, @learncyber and @kodibtc, on November 11, 2022, are estimated to have reached over one million views. The accounts have been suspended.
Also included within the video is an invitation hyperlink to a Discord server managed by the adversary, which had almost 32,000 members earlier than it was reported and deleted. Victims becoming a member of the Discord server subsequently obtain a hyperlink to a GitHub repository that hosts the malware.
The attacker has since renamed the venture to “Nitro-generator” however not earlier than it landed on GitHub’s Trending repositories record for November 27, 2022, by urging the brand new members on Discord to star the venture.
Besides altering the repository title, the menace actor deleted previous information within the venture and uploaded recent ones, one in every of which even described the up to date Python code as “Its open supply, its not a **VIRUS**.” The GitHub account has now been pulled.
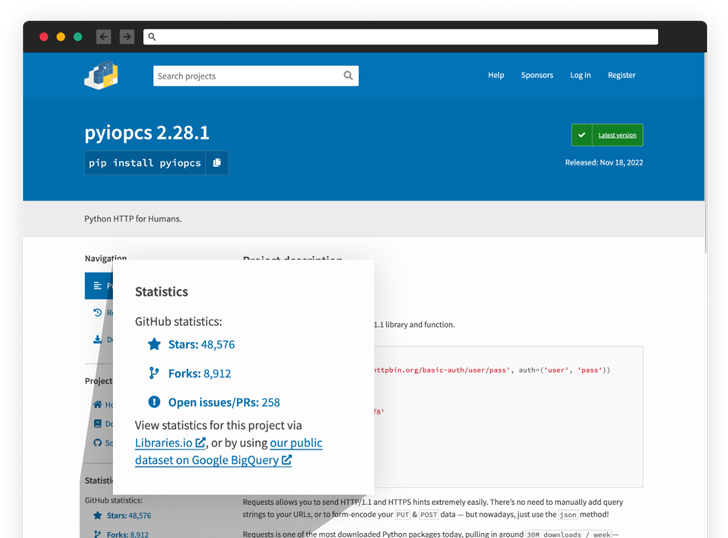
The stealer code is alleged to have been embedded in numerous Python packages equivalent to “tiktok-filter-api,” “pyshftuler,” “pyiopcs,” and “pydesings,” with the operators swiftly publishing new replacements to the Python Package Index (PyPI) beneath completely different names upon getting eliminated.
“The stage of manipulation utilized by software program provide chain attackers is growing as attackers develop into more and more intelligent,” Nachshon famous. “These assaults display once more that cyber attackers have began to focus their consideration on the open supply package deal ecosystem.”
[ad_2]