[ad_1]
Chinese-speaking people in Southeast and East Asia are the targets of a brand new rogue Google Ads marketing campaign that delivers distant entry trojans corresponding to FatalRAT to compromised machines.
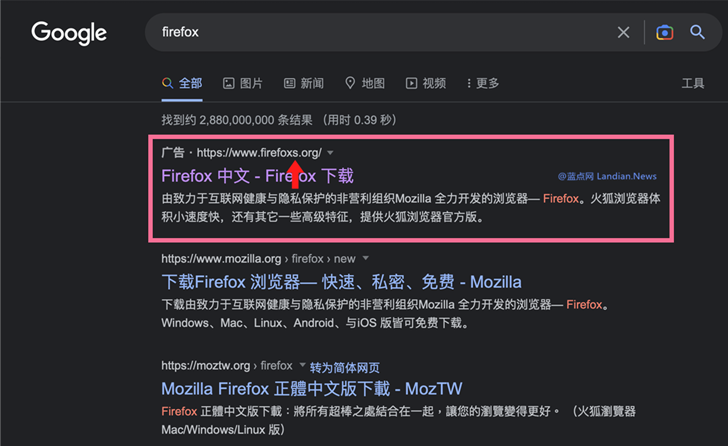
The assaults contain buying advert slots to seem in Google search outcomes and direct customers searching for in style purposes to rogue web sites internet hosting trojanized installers, ESET stated in a report printed at this time. The advertisements have since been taken down.
Some of the spoofed purposes embrace Google Chrome, Mozilla Firefox, Telegram, WhatsApp, LINE, Signal, Skype, Electrum, Sogou Pinyin Method, Youdao, and WPS Office.
“The web sites and installers downloaded from them are largely in Chinese and in some instances falsely supply Chinese language variations of software program that isn’t out there in China,” the Slovak cybersecurity agency stated, including it noticed the assaults between August 2022 and January 2023.
A majority of the victims are situated in Taiwan, China, and Hong Kong, adopted by Malaysia, Japan, the Philippines, Thailand, Singapore, Indonesia, and Myanmar. The attackers’ finish objectives are unclear as but.
The most necessary facet of the assaults is the creation of lookalike web sites with typosquatted domains to propagate the malicious installer, which, in an try to sustain the ruse, installs the authentic software program, but additionally drops a loader that deploys FatalRAT.
In doing so, it grants the attacker full management of the victimized laptop, together with executing arbitrary shell instructions, operating information, harvesting knowledge from internet browsers, and capturing keystrokes.
“The attackers have expended some effort concerning the domains used for his or her web sites, attempting to be as just like the official names as potential,” the researchers stated. “The faux web sites are, usually, equivalent copies of the authentic websites.”
The findings arrive lower than a yr after Trend Micro disclosed a Purple Fox marketing campaign that leveraged tainted software program packages mimicking Adobe, Google Chrome, Telegram, and WhatsApp as an arrival vector to propagate FatalRAT.
“We could not verify if these two investigations are linked,” Matías Porolli, malware researcher at ESET, instructed The Hacker News. “While there are some similarities (use of FatalRAT, use of faux installers), we did not discover similarities within the chain of elements used to ship the RAT or within the infrastructure utilized by the attackers.”
They additionally arrive amid a broader abuse of Google Ads to serve a variety of malware, or alternatively, take customers to credential phishing pages.
In a associated growth, Symantec, a part of Broadcom Software, make clear a “very small” and “focused” malware marketing campaign that leverages a beforehand undocumented .NET-based implant dubbed Frebniis. The assaults are estimated to be “lower than a handful” and “very targeted on Taiwan.”
“The method utilized by Frebniis entails injecting malicious code into the reminiscence of a DLL file (iisfreb.dll) associated to an IIS function used to troubleshoot and analyze failed internet web page requests,” Symantec stated.
“This permits the malware to stealthily monitor all HTTP requests and acknowledge specifically formatted HTTP requests despatched by the attacker, permitting for distant code execution.”
The cybersecurity agency, which attributed the intrusions to an unidentified actor, stated it is at present not recognized how entry to the Windows machine operating the Internet Information Services (IIS) server was obtained.