[ad_1]
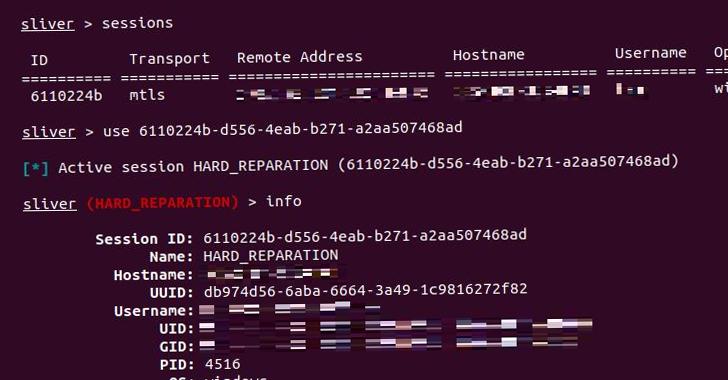
Threat actors are leveraging identified flaws in Sunlogin software program to deploy the Sliver command-and-control (C2) framework for finishing up post-exploitation actions.
The findings come from AhnLab Security Emergency response Center (ASEC), which discovered that safety vulnerabilities in Sunlogin, a distant desktop program developed in China, are being abused to deploy a variety of payloads.
“Not solely did menace actors use the Sliver backdoor, however in addition they used the BYOVD (Bring Your Own Vulnerable Driver) malware to incapacitate safety merchandise and set up reverse shells,” the researchers stated.
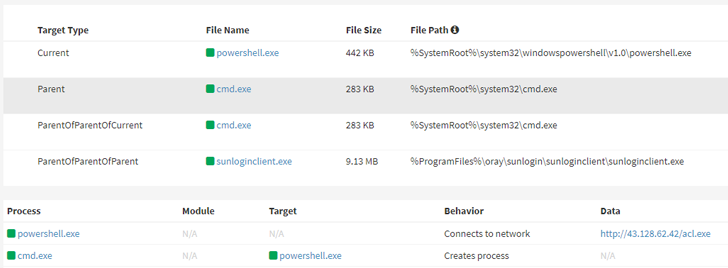
Attack chains begin with the exploitation of two distant code execution bugs in Sunlogin variations previous to v11.0.0.33 (CNVD-2022-03672 and CNVD-2022-10270), adopted by delivering Sliver or different malware reminiscent of Gh0st RAT and XMRig crypto coin miner.
In one occasion, the menace actor is claimed to have weaponized the Sunlogin flaws to put in a PowerShell script that, in flip, employs the BYOVD method to incapacitate safety software program put in within the system and drop a reverse shell utilizing Powercat.
The BYOVD methodology abuses a legit however weak Windows driver, mhyprot2.sys, that is signed with a legitimate certificates to achieve elevated permissions and terminate antivirus processes.
It’s value noting right here that the anti-cheat driver for the Genshin Impact online game was beforehand utilized as a precursor to ransomware deployment, as disclosed by Trend Micro.
“It is unconfirmed whether or not it was finished by the identical menace actor, however after just a few hours, a log exhibits {that a} Sliver backdoor was put in on the identical system by a Sunlogin RCE vulnerability exploitation,” the researchers stated.
The findings come as menace actors are adopting Sliver, a Go-based legit penetration testing instrument, as an alternative choice to Cobalt Strike and Metasploit.
“Sliver affords the required step-by-step options like account info theft, inner community motion, and overtaking the interior community of corporations, similar to Cobalt Strike,” the researchers concluded.