[ad_1]
Travel businesses have emerged because the goal of a hack-for-hire group dubbed Evilnum as a part of a broader marketing campaign aimed toward authorized and monetary funding establishments within the Middle East and Europe.
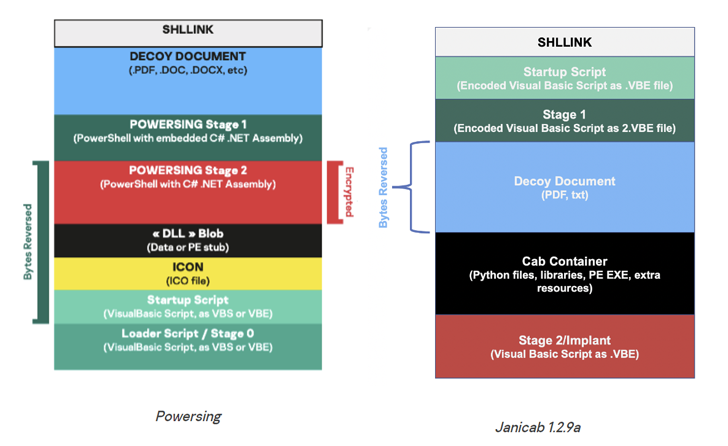
The assaults focusing on legislation companies all through 2020 and 2021 concerned a revamped variant of a malware referred to as Janicab that leverages various public companies like YouTube as useless drop resolvers, Kaspersky mentioned in a technical report printed this week.
Janicab infections comprise a various set of victims positioned in Egypt, Georgia, Saudi Arabia, the UAE, and the U.Ok. The growth marks the primary time authorized organizations in Saudi Arabia have been focused by this group.
Also tracked as DeathStalker, the menace actor is thought to deploy backdoors like Janicab, Evilnum, Powersing, and PowerPepper to exfiltrate confidential company info.
“Their curiosity in gathering delicate enterprise info leads us to imagine that DeathStalker is a gaggle of mercenaries providing hacking-for-hire companies, or performing as some kind of info dealer in monetary circles,” the Russian cybersecurity firm famous in August 2020.
According to ESET, the hacking crew has a sample of harvesting inner firm shows, software program licenses, e mail credentials, and paperwork containing buyer lists, investments and buying and selling operations.
Earlier this yr, Zscaler and Proofpoint uncovered contemporary assaults orchestrated by Evilnum which were directed in opposition to firms within the crypto and fintech verticals since late 2021.
Kaspersky’s evaluation of the DeathStalker intrusions has revealed the usage of an LNK-based dropper embedded inside a ZIP archive for preliminary entry via a spear-phishing assault.
The lure attachment purports to be a company profile doc associated to energy hydraulics that, when opened, results in the deployment of the VBScript-based Janicab implant, which is able to command execution and deploying extra instruments.
Newer variations of the modular malware have concurrently eliminated audio recording options and added a keylogger module that shares overlaps with prior Powersing assaults. Other capabilities embody checking for put in antivirus merchandise and getting a listing of processes indicating malware evaluation.
The 2021 assaults are additionally notable for using unlisted outdated YouTube hyperlinks which are used to host an encoded string that is deciphered by Janicab to extract the command-and-control (C2) IP handle for retrieving follow-on instructions and exfiltrating knowledge.
“Since the menace actor makes use of unlisted outdated YouTube hyperlinks, the probability of discovering the related hyperlinks on YouTube is sort of zero,” the researchers mentioned. “This additionally successfully permits the menace actor to reuse C2 infrastructure.”
The findings underscore that the menace actor has continued to replace its malware toolset to keep up stealthiness over prolonged intervals of time.
Besides software allowlisting and working system hardening, organizations are beneficial to watch Internet Explorer processes, because the browser is utilized in hidden mode to speak with the C2 server.
As authorized and monetary sectors are a standard goal for the menace actor, the researchers additional theorized that DeathStalker’s prospects and operators might be weaponizing the intrusions to maintain tabs on lawsuits, blackmail high-profile people, observe monetary property, and harvest enterprise intelligence about potential mergers and acquisitions.