[ad_1]
The menace actors related to the Gootkit malware have made “notable modifications” to their toolset, including new parts and obfuscations to their an infection chains.
Google-owned Mandiant is monitoring the exercise cluster underneath the moniker UNC2565, noting that the utilization of the malware is “unique to this group.”
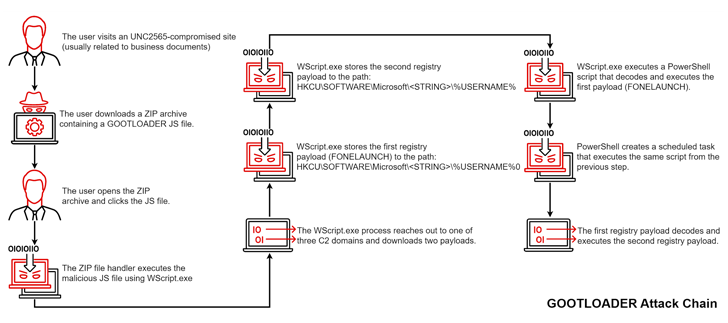
Gootkit, additionally known as Gootloader, is unfold by compromised web sites that victims are tricked into visiting when trying to find business-related paperwork like agreements and contracts by way of a way known as search engine marketing (search engine optimisation) poisoning.
The purported paperwork take the type of ZIP archives that harbor the JavaScript malware, which, when launched, paves the best way for extra payloads akin to Cobalt Strike Beacon, FONELAUNCH, and SNOWCONE.
FONELAUNCH is a .NET-based loader designed to load an encoded payload into reminiscence, and SNOWCONE is a downloader that is tasked with retrieving next-stage payloads, usually IcedID, by way of HTTP.
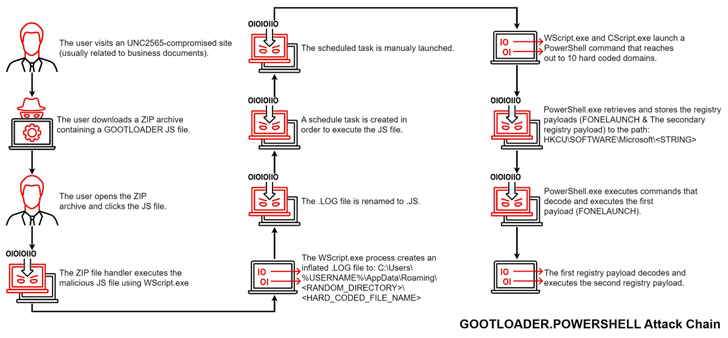
While the overarching objectives of Gootkit have remained unchanged, the assault sequence in itself has acquired vital updates, whereby the JavaScript file inside the ZIP archive is trojanized and incorporates one other obfuscated JavaScript file that consequently proceeds to execute the malware.
The new variant, which was noticed by the menace intelligence agency in November 2022, is being tracked as GOOTLOADER.POWERSHELL. It’s price noting that the revamped an infection chain was additionally documented by Trend Micro earlier this month, detailing Gootkit assaults concentrating on the Australian healthcare sector.
What’s extra, the malware authors are mentioned to have taken three totally different approaches to obscure Gootkit, together with concealing the code inside altered variations of reliable JavaScript libraries akin to jQuery, Chroma.js, and Underscore.js, in an try to flee detection.
It’s not simply Gootkit, as three totally different flavors of FONELAUNCH – FONELAUNCH.FAX, FONELAUNCH.PHONE, and FONELAUNCH.DIALTONE – have been put to make use of by UNC2565 since May 2021 to execute DLLs, .NET binaries, and PE information, indicating that the malware arsenal is being constantly maintained and up to date.
“These modifications are illustrative of UNC2565’s lively growth and progress in capabilities,” Mandiant researchers Govand Sinjari and Andy Morales mentioned.