[ad_1]

Open supply software program and software program provide chain safety dangers proceed to be a main concern for builders and organizations. According to a 2022 research by digital design and automation firm Synopsys, 84% of open supply software program codebases contained a minimum of one recognized vulnerability — an almost 4% improve from final 12 months — and 48% contained a high-risk vulnerability.
In response to the threats hidden in open supply software program, Google Cloud is making its Assured Open Source Software service for Java and Python ecosystems obtainable to all for free of charge. The free Assured OSS offers any group entry to Google-vetted codebase packages that Google makes use of in its workflows.
The transfer comes on the heels of Google Cloud’s choice to supply its Project Shield distributed denial-of-service (DDoS) protection to authorities websites, information and impartial journalists, websites associated to elections and voting and websites that cowl human rights — a response to the rise in politically motivated DDoS assaults.
SEE: What DevSecOps means for securing the software program lifecycle.
Assured OSS, a walled backyard for open-source codebases
Google launched Assured OSS in May of 2022 partially to handle the fast progress in cyberattacks geared toward open supply suppliers, based on Andy Chang, group product supervisor, safety and privateness at Google. He cited trade sources reporting a 650% surge in software program provide chain assaults in 2021, when using OSS elevated dramatically.
He informed TechRepublic that because the firm first introduced and launched Assured OSS, it meant that the service have the ability to meet DevSecOps groups and builders the place they’re at this time with the pipeline and tooling they already use and leverage each day.
“Software supply chain attacks targeting open source continue to increase. Secure ingest of open source packages is a widespread challenge for organizations and developers wherever they choose to build code,” he stated. “Google is uniquely positioned to help in this area as we are a long time contributor, maintainer, user of open source software and have developed a robust set of technology, processes, security capabilities and controls.”
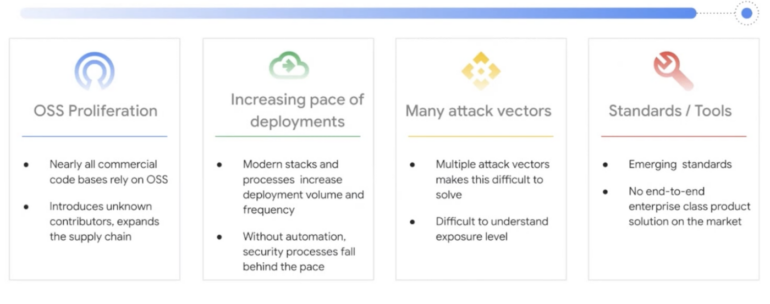
He articulated 4 key components behind the rise in assaults:
- OSS proliferation
- The rising tempo of deployments, particularly with the development driving containers, microservices and an rising variety of cloud knowledge companies.
- Many assault vectors attacking all layers of the stack: {hardware}, infrastructure programs, working programs, middleware, app companies, APIs and — essentially the most susceptible level of entry — people.
- Gaps in standardization round tooling wanted to holistically handle the product cycle and in safety and danger data (Figure A).
Figure A
Mike McGuire, senior software program options supervisor at Synopsys, defined that Google has a direct curiosity within the open supply neighborhood being as safe as potential.
“The open source community really is just that — a ‘community’ that best operates when its members don’t just take, but also contribute, and Google has always supported that with their actions,” he stated. “Google clearly has many tools, processes and frameworks in place to ensure the integrity of their dependencies and development pipeline, so they are simply sharing the fruit of those efforts out to the broader community.”
He added that Google is working to construct up their cloud-native utility growth platform, “And that platform is all the more valuable when using it means having to worry less about complicated software supply chain threats.”
Features of Assured OSS
Google stated the code packages which are obtainable as a part of Google’s Assured OSS program:
- Are frequently scanned, analyzed, and fuzz-tested for vulnerabilities.
- Have corresponding enriched metadata incorporating Container/Artifact Analysis knowledge.
- Are constructed with Cloud Build, together with proof of verifiable SLSA-compliance.
- Are verifiably signed by Google.
- Are distributed from an Artifact Registry secured and guarded by Google.
Securing codebases from fuzz testing to SLSA compliance
Securing codebases means addressing potential ports of entry for attackers and likewise crash testing software program for so-called nook instances, or weaknesses in sudden areas.
McGuire stated Google has rigorous requirements with regards to which packages they belief, and for those who they do, they’re primarily endorsing them to the general public and offering proof of their efforts in vetting these elements.
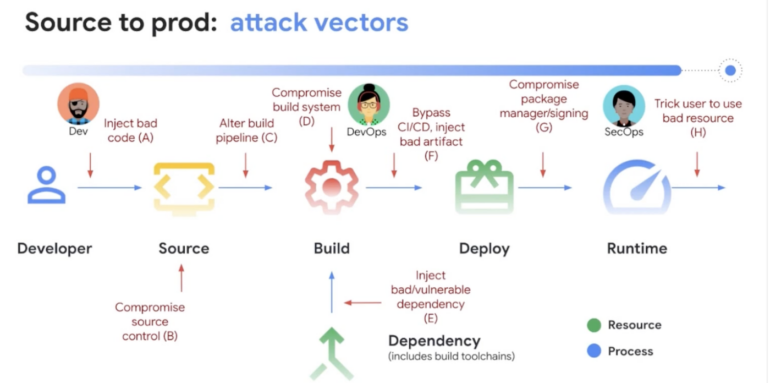
“Assured OSS clearly provides value to organizations looking for guidance on which packages are trustworthy within the sprawling open source universe,” he stated. “But it’s important that they also have the tools in place to keep problematic components from entering their development pipeline, as well as continuously monitor previously trustworthy components for any newly discovered issues.” (Figure B)
Figure B
Fuzz testing
Chang defined that fuzz testing, aka “fuzzing,” makes use of invalid, sudden or random inputs to show irregular habits corresponding to reminiscence leaks, crashes or undocumented performance.
Salsa for software program
The SLSA — “supply chain levels for software artifacts,” pronounced “salsa” — framework provides a stage of assurance to the software program growth lifecycle. “Today, software developers are challenged to make informed decisions about the external software they bring into their own systems,” stated Chang. “Especially if it is owned and operated by a third party.”
He stated SLSA formalizes the standards round software program provide chain integrity and helps companies take incremental steps towards a safer software program provide chain by including extra safety tips to handle the commonest threats throughout the panorama at this time.
“When software is provided at an assured and attested SLSA level, customers know upfront which risks have already been mitigated by the provider,” he defined.
“Simply put, SLSA is a framework introduced by Google that can be used to assess the security of both software packages and the development lifecycles that built and delivered them,” added McGuire. “As it pertains to Assured OSS, the packages that Google supports as part of this program have been built, evaluated and delivered in alignment with the SLSA standard, which aims to assure the community of the integrity of the packages,” he stated.
Enriched metadata
According to Chang, enriched metadata that includes container evaluation knowledge is essential as a result of, “The more you know about the open source software being used, the better choices DevSecOps teams have related to policy enforcement and risk.”
He supplied examples of how clients can use enriched metadata with Assured OSS packages:
- Reviewing the offered lists of transitive dependencies to know what else could also be impacted.
- Reviewing the SLSA stage to assist information the admission and guard rail insurance policies they set for packages to progress of their pipeline.
- Reviewing the VEX — or vulnerability, exploitability and change — knowledge to higher perceive that are essentially the most impactful vulnerabilities within the open supply elements.
- Understanding the offered license file knowledge in order that clients can apply insurance policies as wanted to make sure they meet their inside open supply program workplace insurance policies.
Signatures for software program
Like a signed test, the verifiable signing Assured OSS gives for each its binaries and metadata allow clients to simply confirm that the binaries and metadata come from Google and haven’t been tampered with throughout distribution, based on Chang.
“In addition, because the metadata is signed, customers can have confidence that the details contained in the metadata — including how the package is built, the build steps, which build tools touched the code and which security scan tools were run on the code — are all as they were when Google created them,” he stated.
SEE: DevSecOps is greater than shifting left.
Focus on Java and Python packages
Google stated the Assured OSS program will make it potential for organizations to get OSS packages from a vetted supply and know what the software program contains as a result of it consists of Google’s software program invoice of supplies, generally called SBOMs. The firm stated the Assured OSS challenge consists of 1,000 Java and Python packages and reduces the necessity for DevOps groups to determine and function their very own OSS safety workflows.
“Using methods such as fuzz testing, and including metadata of container or artifact analysis results, serves to attest to the security efforts performed,” stated McGuire. “As a matter of fact, being able to perform this type of security testing on dependencies, and provide this level of information, might be a sign of what’s to come in the near future for software producers, especially for those doing business in highly regulated industries.”
SEE: Why provide chain safety ought to be a part of your 2023 DevOps plan.
Massive progress in OSS, and OSS vulnerabilities
Synopsys’ eighth annual Open Source Security & Risk Analysis (OSSRA) report, primarily based on 1,700 audits throughout 17 industries, discovered:
- 163% improve in use of OSS by the EdTech sector.
- 97% improve in OSS use by aerospace, aviation, automotive, transportation and logistics sectors, with a 232% improve in high-risk vulnerabilities.
- 74% progress in OSS use by the manufacturing and robotics sectors.
- 557% progress in high-risk vulnerabilities within the retail and eCommerce sector since 2019.
- 89% of the entire code being open supply, and a 130% improve in high-risk vulnerabilities in the identical interval.
- 31% of codebases are utilizing open supply with no discernable license or with custom-made licenses.
