[ad_1]
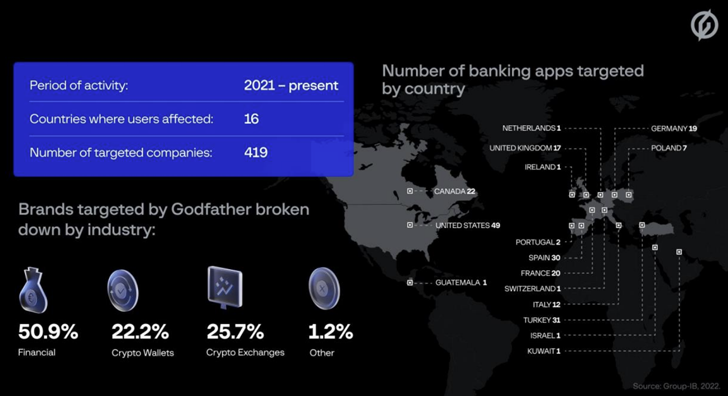
An Android banking trojan referred to as GodFather is getting used to focus on customers of greater than 400 banking and cryptocurrency apps spanning throughout 16 international locations.
This consists of 215 banks, 94 crypto pockets suppliers, and 110 crypto trade platforms serving customers within the U.S., Turkey, Spain, Italy, Canada, and Canada, amongst others, Singapore-headquartered Group-IB stated in a report shared with The Hacker News.
The malware, like many monetary trojans focusing on the Android ecosystem, makes an attempt to steal consumer credentials by producing convincing overlay screens (aka net fakes) which can be served atop goal purposes.
First detected by Group-IB in June 2021 and publicly disclosed by ThreatFabric in March 2022, GodFather additionally packs in native backdoor options that permits it to abuse Android’s Accessibility APIs to document movies, log keystrokes, seize screenshots, and harvest SMS and name logs.
Group-IB’s evaluation of the malware has revealed it to be a successor of Anubis, one other banking trojan that had its supply code leaked in an underground discussion board in January 2019. It’s additionally stated to be distributed to different menace actors by the malware-as-a-service (MaaS) mannequin.
The similarities between the 2 malware households lengthen to the strategy of receiving the command-and-control (C2) tackle, implementation of C2 instructions, and the net pretend, proxy and display screen seize modules. However, audio recording and placement monitoring options have been eliminated.
“Interestingly, GodFather spares customers in post-Soviet international locations,” Group-IB stated. “If the potential sufferer’s system preferences embrace one of many languages in that area, the Trojan shuts down. This may counsel that GodFather’s builders are Russian audio system.”
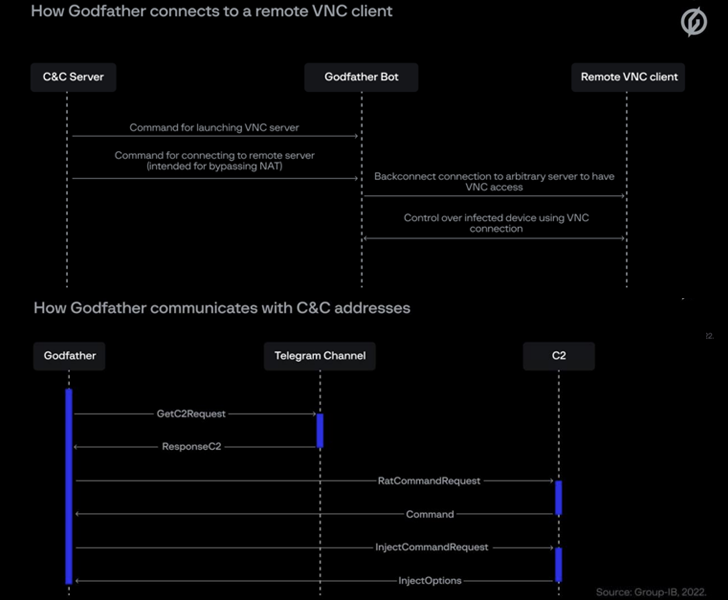
What makes GodFather stand out is the truth that it retrieves its command-and-control (C2) server tackle by decrypting actor-controlled Telegram channel descriptions which can be encoded utilizing the Blowfish cipher.
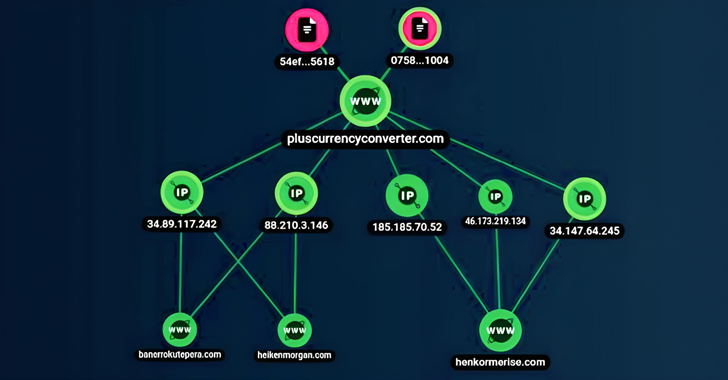
The actual modus operandi employed to contaminate consumer gadgets isn’t recognized, though an examination of the menace actor’s command-and-control (C2) infrastructure reveals trojanized dropper apps as one potential distribution vector.
This is predicated on a C2 tackle that is linked to an app named Currency Converter Plus (com.plus.currencyconverter) that was hosted on the Google Play Store as of June 2022. The software in query is now not obtainable for obtain.
Another artifact examined by Group-IB impersonates the reliable Google Play Protect service that, upon being launched, creates an ongoing notification and hides its icon from the record of put in purposes.
The findings come as Cyble found quite a lot of GodFather samples masquerading because the MYT Müzik app geared toward customers in Turkey.
GodFather isn’t the one Android malware primarily based on Anubis. Earlier this July, ThreatFabric revealed {that a} modified model of Anubis referred to as Falcon focused Russian customers by impersonating the state-owned VTB Bank.
“The emergence of GodFather underscores the power of menace actors to edit and replace their instruments to keep up their effectiveness regardless of efforts by malware detection and prevention suppliers to replace their merchandise,” Group-IB researcher Artem Grischenko stated.
“With a device like GodFather, menace actors are restricted solely by their means to create convincing net fakes for a specific software. Sometimes, the sequel actually could be higher than the unique.”
[ad_2]