[ad_1]
The operators of the Glupteba botnet resurfaced in June 2022 as a part of a renewed and “upscaled” marketing campaign, months after Google disrupted the malicious exercise.
The ongoing assault is suggestive of the malware’s resilience within the face of takedowns, cybersecurity firm Nozomi Networks stated in a write-up. “In addition, there was a tenfold improve in TOR hidden providers getting used as C2 servers because the 2021 marketing campaign,” it famous.
The malware, which is distributed by way of fraudulent adverts or software program cracks, can also be geared up to retrieve further payloads that allow it to steal credentials, mine cryptocurrencies, and develop its attain by exploiting vulnerabilities in IoT gadgets from MikroTik and Netgear.
It’s additionally an occasion of an uncommon malware that leverages blockchain as a mechanism for command-and-control (C2) since at the least 2019, rendering its infrastructure immune to takedown efforts as within the case of a standard server.
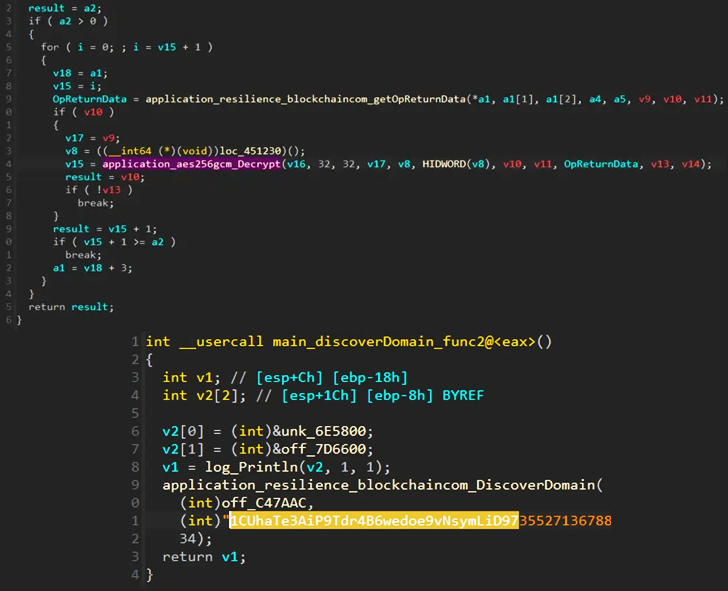
Specifically, the botnet is designed to look the general public Bitcoin blockchain for transactions associated to pockets addresses owned by the risk actor in order to fetch the encrypted C2 server deal with.
“This is made doable by the OP_RETURN opcode that permits storage of as much as 80 bytes of arbitrary information inside the signature script,” the commercial and IoT safety agency defined, including the mechanism additionally makes Glupteba exhausting to dismantle as “there isn’t any approach to erase nor censor a validated Bitcoin transaction.”
The technique additionally makes it handy to interchange a C2 server ought to it’s taken down, as all that’s wanted for the operators is to publish a brand new transaction from the actor-controlled Bitcoin pockets deal with with the encoded up to date server.
In December 2021, Google managed to trigger a big dent to its operations, alongside submitting a lawsuit in opposition to two Russian nationals who oversaw the botnet. Last month, a U.S. courtroom dominated in favor of the tech large.
“While Glupteba operators have resumed exercise on some non-Google platforms and IoT gadgets, shining a authorized highlight on the group makes it much less interesting for different felony operations to work with them,” the web behemoth identified in November.
Nozomi Networks, which examined over 1,500 Glupteba samples uploaded to VirusTotal, stated it was capable of extract 15 pockets addresses that have been put to make use of by the risk actors relationship all the way in which again to June 19, 2019.
The ongoing marketing campaign that commenced in June 2022 can also be maybe the most important wave prior to now few years, what with the variety of rogue bitcoin addresses leaping to 17, up from 4 in 2021.
One of these addresses, which was first energetic on June 1, 2022, has transacted 11 occasions to this point and is utilized in as many as 1,197 artifacts, making it probably the most broadly used pockets deal with. The final transaction was recorded on November 8, 2022.
“Threat actors are more and more leveraging blockchain know-how to launch cyberattacks,” the researchers stated. “By making the most of the distributed and decentralized nature of blockchain, malicious actors can exploit its anonymity for quite a lot of assaults, starting from malware propagation to ransomware distribution.”