[ad_1]
Cloud-based repository internet hosting service GitHub has addressed a high-severity safety flaw that would have been exploited to create malicious repositories and mount provide chain assaults.
The RepoJacking method, disclosed by Checkmarx, entails a bypass of a safety mechanism known as standard repository namespace retirement, which goals to forestall builders from pulling unsafe repositories with the identical identify.
The situation was addressed by the Microsoft-owned subsidiary on September 19, 2022 following accountable disclosure.
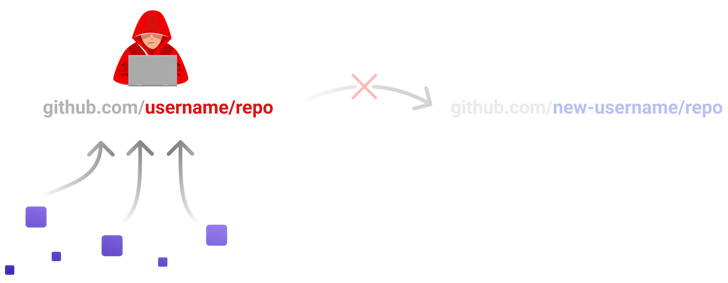
RepoJacking happens when a creator of a repository opts to vary the username, doubtlessly enabling a menace actor to assert the outdated username and publish a rogue repository with the identical identify in an try to trick customers into downloading them.
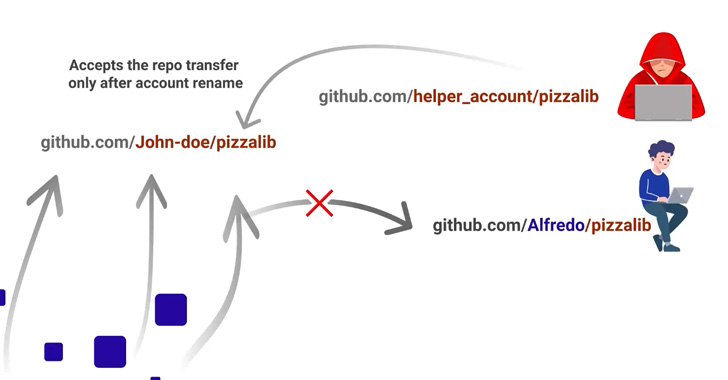
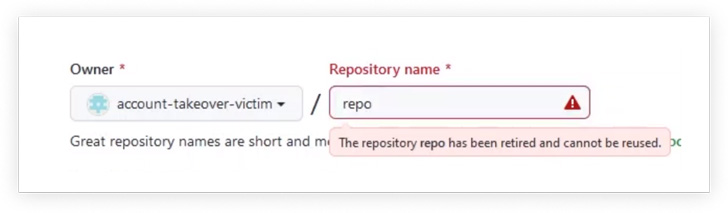
While Microsoft’s countermeasure “retire[s] the namespace of any open supply mission that had greater than 100 clones within the week main as much as the proprietor’s account being renamed or deleted,” Checkmarx discovered that this may be circumvented via the “repository switch” characteristic.
The method this works is as follows –
- A menace actor creates a repository with the identical identify because the retired repository (say, “repo”) owned by a consumer named “sufferer” however beneath a unique username (say, “helper”)
- “helper” transfers possession of “repo” to a second account with username “attacker”
- “attacker” renames the account’s username to “sufferer”
- The namespace “sufferer/repo” is now beneath the adversary’s management
In different phrases, the assault hinges on the quirk that GitHub solely considers as retired the namespace, i.e., the mix of username and repository identify, allowing a nasty actor to reuse the repository identify at the side of an arbitrary username.
A profitable exploitation may have successfully allowed attackers to push poisoned repositories, placing renamed usernames vulnerable to being a sufferer of provide chain assaults.
“If not explicitly tended, all renamed usernames on GitHub had been susceptible to this flaw, together with over 10,000 packages on the Go, Swift, and Packagist bundle managers,” Checkmarx researcher Aviad Gershon stated.